Source: securityboulevard.com – Author: Pierre Coyne
Conventional wisdom suggests best-of-breed is the only way to secure your clouds. But what of hybrid attack paths that cross security domains — like those exploited in the SolarWinds and Capital One breaches? Exposing the gaps attackers exploit to move laterally requires visibility and context across security silos.
Insidious attacks like those associated with the 2020 SolarWinds breach — which compromised the software supply chain — frequently progressed from on-premises to cloud infrastructures completely unchecked. Others, like the 2019 Capital One breach, exploited a vulnerable web application to ultimately compromise client data stored in cloud infrastructure. These are just two examples of high-profile cloud breaches that traversed traditional security silos, making them challenging to prevent using siloed approaches.
Whether you’re responsible for securing cloud environments, or the entirety of your attack surface, even the best point tools will not give you the level of visibility needed to expose and close the gaps that attackers exploit to move across environments and compromise high-value targets.
Cloud-related breaches in the past 18 months

Source: Tenable, 2024 Cloud Security Outlook: Navigating Barriers and Setting Priorities
In this blog, we explore the SolarWinds and Capital One breaches, including the techniques used by attackers, and the security conventions that contributed to their success. More importantly, we explore how you can augment your existing security practices and understand the elusive attacker’s perspective to help you shut down even the most sophisticated threat actors.
“Combined with the use of sophisticated authentication exploits, [the SolarWinds breach] also leveraged vulnerabilities and major authentication protocols, basically granting the intruder the keys to the kingdom, allowing them to deftly move across both on-premises and cloud-based services, all while avoiding detection.”
— Senator Mark R. Warner (D-Virginia), Chairman, U.S. Senate Select Committee on Intelligence, SolarWinds Hearing, Feb. 23, 2021
SolarWinds: Even the best cloud security solutions were ineffective
The breach of the SolarWinds Orion infrastructure management platform will go down in history as one of the costliest when measured in terms of total financial impact — estimated at nearly $1 billion — and sheer number of organizations affected. The United States government alone invested over $750 million to upgrade security systems in response. Insurers paid out $90 million in claims. And SolarWinds spent $40 million in just the first year, plus an additional $25 million to settle investor lawsuits.
Beyond the financial impact, the attack — which embedded malicious code into SolarWinds Orion software— introduced a layer of suspicion into a previously trusted and almost routine supply chain process used by countless vendors and customers.
Attackers reportedly directed by the Russian intelligence service first breached the SolarWinds development environment and injected the malicious code, known as Sunburst, into the Orion platform before the final build process. The software was then automatically sent to nearly 18,000 organizations, including the U.S. Department of Defense, the Department of Homeland Security, the Treasury Department, numerous government organizations in other countries, as well as leading enterprises including Cisco, Intel, Microsoft, Mandiant and Palo Alto Networks. The Sunburst code provided a back door attackers could use to gain initial entry into target organizations, along with machine privileges.
Threat actors did not honor security silos
The breaches of SolarWinds customers that followed frequently exploited the back door in the Orion software to gain an initial foothold on premises before moving laterally to the cloud. Attackers were able to move to the cloud despite varying degrees of existing cloud security tools, network segmentation and multi-factor authentication (MFA) in use at the targeted organizations.
After gaining initial access to the networks of the targeted organizations, attackers used popular tools and techniques to exploit unpatched vulnerabilities and misconfigurations and move laterally to high-value targets. For example, using mimikatz, attackers frequently accessed credentials stored as LSA Secrets to create a rogue domain controller in Microsoft Active Directory, ultimately leading to control over the Active Directory Federation Service.
Techniques used in the SolarWinds breaches
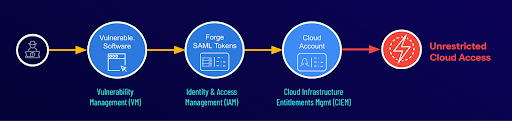
Source: Tenable, October 2024
Attackers then forge SAML tokens, bypassing MFA and allowing them to move laterally to clouds using SAML for SSO, such as Microsoft Azure and Office 360. Attackers were not only able to give themselves full administrative privileges, but they were authenticated as legitimate users. Once authorized to access the respective cloud, they were effectively unstoppable by traditional cloud security.
40% of organizations using Active Directory have unpatched critical or high severity vulnerabilities that are frequently exploited by attackers.
— Tenable Research, based on data from 9,000 organizations using Active Directory
Capital One: Without relationship context, security was an illusion
Unlike the SolarWinds breach, the Capital One breach targeted the company’s Amazon Web Services (AWS) cloud infrastructure and demonstrates the ease with which an attacker can move across security silos frequently seen in cloud infrastructure.
Web applications offer a primary way in for attackers

Source: Verizon 2024 Data Breach Investigations Report, Web applications were the number one ways-in vector, used in upwards of 60% of non-error, non-misuse breaches.
The attacker, a former Amazon Web Services (AWS) engineer, initially exploited an externally facing web application to gain machine privileges. They leveraged the machine identity to access credentials and elevate privileges further. And they ultimately exploited a misconfiguration to discover and exfiltrate sensitive data stored in cloud object storage. The result? Sensitive data from more than 100 million Capital One users was compromised.
What is not immediately obvious is that each of these findings is typically identified by separate security tools (and teams) — web application scanning, cloud security posture management (CSPM), and cloud infrastructure entitlements management (CIEM) respectively. Independently, all lacked the technical and business context needed to identify the criticality and entirety of the attack path.
Techniques used in the Capital One breach
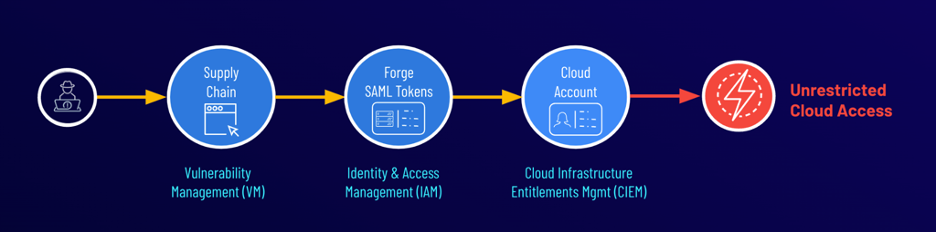
Source: Tenable, 2024
A better approach to securing the modern attack surface
So what lessons can we take from these attacks, and how can we apply them in the context of our existing security program to drive better outcomes?
- Breaches can begin anywhere and attackers can move anywhere. Whether they originate on prem or in the cloud, some initial attack vectors are virtually impossible to prevent outright, such as supply chain or phishing attacks. It is therefore imperative to have complete visibility into all assets and their relationships across the attack surface to not only identify potential entry points, but also to close off opportunities for attackers to move laterally.
Select ways-in enumerations in non-error, non-misuse breaches over time

- Every breach is an identity breach. Whether an attacker exploits a vulnerability or misconfiguration to compromise an asset, or uses a social engineering attack or stolen password to commandeer a user account, EVERY ATTACK looks to exploit identity — be it human or machine — to elevate privileges and ultimately gain control over crown jewels, such as administrator accounts and identity systems like Active Directory, or critical business applications and data stores.
- Security without context is an illusion. Security silos are a fact of life, and necessity in many cases, but without integrated visibility into assets, identities, risk relationships and their potential impact to crown jewels, organizations lack the attacker’s point of view needed to effectively identify and close viable attack paths — the ones attackers will ultimately exploit once they gain initial access.
The challenge, of course, is that traditional security tools are not designed with these considerations in mind.
Exposure management unifies visibility, insight and action
The role of exposure management platforms, such as Tenable One, is to unify visibility, insight and action across the attack surface. Tenable One not only discovers asset, identity and risk relationships across multi-cloud environments, it also discovers on prem IT, operational technology (OT) and internet of things (IoT) assets and identities.
Exposure management is a preventative security strategy that leverages deep context, in the form of business-aligned asset, identity and risk relationships to distinguish ordinary risk findings from true exposure that can have a material impact on an organization. What makes exposure management different is that it looks at the entire attack surface (cloud, IT, OT, IoT, identities, applications), and the full spectrum of preventable risk (vulnerabilities, misconfigurations, human and machine privileges) which enable all breaches, exposing and closing viable attack paths before a breach can begin.
For example, Tenable One’s inventory includes human and machine identities and privileges from Active Directory — provided by Tenable Identity Exposure. This information is integrated with multi-cloud identities and privileges – provided by Tenable Cloud Security. Combined, they enable Tenable One to map technical and business relationships across traditional security boundaries, prioritizing attack paths such as those used in the SolarWinds and Capital One breaches.
The short video below demonstrates how Tenable One can uncover and bridge visibility gaps exploited in the SolarWinds and Capital One breaches t so users can remediate high exposure attack paths before they can be exploited by attackers.
Source: Tenable, October 2024
Tenable One’s capabilities set it apart from other exposure management platforms in two key ways:.
- Cloud-only exposure management platforms (sometimes referred to as CNAPP) focus on public cloud assets, identities and risks. This means they can miss security risks that traverse cloud and hybrid environments.
- Other exposure management platforms focus on identifying assets across the attack surface (e.g. IT, OT, IoT, Cloud), but lack visibility into identities and their permissions, which are leveraged to progress virtually every attack.
To learn more about exposure management, download the whitepaper “Hackers Don’t Honor Security Silos: 5 Steps To Prioritize True Business Exposure.”
Learn more about Tenable products featured in this blog
- Tenable One is the world’s only AI-powered exposure management platform, designed to radically unify security visibility, insight and action across the modern attack surface to rapidly expose and close the priority gaps that drive up business risk. Security leaders rely on Tenable One to protect against attacks from IT to the cloud to OT and everywhere in between.
- Available as part of Tenable One, Tenable Cloud Security is a comprehensive CNAPP solution that simplifies identification and remediation of risk across multi-cloud environments. Unlike silo tools that leave visibility gaps, it maps every cloud asset, identity, sensitive data and risk – identifying toxic combinations of risk that pose the greatest threat to your business, and helps you close cyber exposure, and improve productivity.
- Also available as part of Tenable One, Tenable Identity Exposure equips modern enterprises with a new level of end-to-end protection from identity-based attacks. This singular solution isolates and eradicates the security gaps where identity-based exploits thrive. Reduce risk by finding and fixing priority exposures across your identity environment to strengthen your security posture and prevent attacks before they occur.
*** This is a Security Bloggers Network syndicated blog from Tenable Blog authored by Pierre Coyne. Read the original post at: https://www.tenable.com/blog/at-nearly-1-billion-global-impact-the-best-cloud-security-couldnt-stop-this-hybrid-attack-path
Original Post URL: https://securityboulevard.com/2024/10/at-nearly-1-billion-global-impact-the-best-cloud-security-couldnt-stop-this-hybrid-attack-path-lesson-map-and-close-viable-attack-paths-before-breaches-begin/
Category & Tags: Security Bloggers Network – Security Bloggers Network
Views: 4





















































