Source: www.csoonline.com – Author: Users could potentially allow access to the entire drive because of the way Microsoft implements OAuth in OneDrive File Picker. Using Microsoft...
Year: 2025
Hacker stehlen Coca-Cola-Daten – Source: www.csoonline.com
Source: www.csoonline.com – Author: Der weltgrößte Coca-Cola-Abfüller Coca-Cola Europacific Partners wurde Ziel einer Cyberattacke. Dabei wurden Daten gestohlen. Der Coca-Cola-Abfüller Coca-Cola Europacific Partners ist von einem...
‘Secure email’: A losing battle CISOs must give up – Source: www.csoonline.com
Source: www.csoonline.com – Author: Opinion May 28, 20257 mins Email SecurityEncryption Security wise, email has long been an outdated mode of communication in our increasingly cyber-threatened...
Will AI agent-fueled attacks force CISOs to fast-track passwordless projects? – Source: www.csoonline.com
Source: www.csoonline.com – Author: AI agents are looming as another security headache for CISOs that could force their hand on shifting to passwordless authentication. And this...
Die wertvollsten Security-Zertifizierungen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Diese Cybersecurity-Zertifizierungen sind bei Arbeitgebern hochgeschätzt und können zur Gehaltsoptimierung beitragen. Zertifizierte IT-Sicherheitsprofis sind (unter anderem) gefragter und verdienen besser. Gorodenkoff |...
New Russian APT group Void Blizzard targets NATO-based orgs after infiltrating Dutch police – Source: www.csoonline.com
Source: www.csoonline.com – Author: News May 27, 20256 mins Advanced Persistent ThreatsCyberattacksEmail Security The cyberespionage group uses compromised credentials to steal emails and data from public...
Code security in the AI era: Balancing speed and safety under new EU regulations – Source: www.csoonline.com
Source: www.csoonline.com – Author: Organizations face the challenge of securing AI-generated code while maintaining a rapid development pace to meet market demands and comply with new...
Adidas Customer Data Stolen in Third-Party Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Adidas has disclosed that customer data was breached following a cyber-attack on a third-party. The global sportswear giant said the data mainly...
Vietnam-Nexus Hackers Distribute Malware Via Fake AI Video Generator Websites – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A hacking group allegedly from Vietnam has been leveraging social media ads promoting generative AI tools to distribute malware since at least...
New Russian State Hacking Group Hits Europe and North America – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A newly discovered Russian state hacking group is targeting government and critical sectors across Europe and North America, Microsoft has warned. The...
Zanubis in motion: Tracing the active evolution of the Android banking malware – Source: securelist.com
Source: securelist.com – Author: Leandro Cuozzo Introduction Zanubis is a banking Trojan for Android that emerged in mid-2022. Since its inception, it has targeted banks and...
Adidas customers’ personal information at risk after data breach – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Lovers of Adidas clothes would be wise to be on their guard against phishing attacks, after the German sportswear giant...
The AI Fix #52: AI adopts its own social norms, and AI DJ creates diversity scandal – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 52 of The AI Fix, our hosts watch a non-existent musical about garlic bread, Graham...
Indian Police Arrest Cybercrime Gang Copycats of Myanmar Biz Model – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Adidas Falls Victim to Third-Party Data Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
CISA Warns of Attacks Targeting Commvault SaaS Environment – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
DragonForce Ransomware Strikes MSP in Supply Chain Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
MathWorks, Creator of MATLAB, Confirms Ransomware Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
FBI: Silent Ransom Group Adopts Vishing Campaign Against Law Firms – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
How the New Hacker Millionaire Class Was Built – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Danabot Takedown Deals Blow to Russian Cybercrime – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
CVE Uncertainty Underlines Importance of Cyber Resilience – Source: www.darkreading.com
Source: www.darkreading.com – Author: Amar Ramakrishnan Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Understanding the Cookie-Bite MFA Bypass Risk – Source: securityboulevard.com
Source: securityboulevard.com – Author: MixMode Threat Research MixMode Threat Research MixMode Threat Research is a dedicated contributor to MixMode.ai’s blog, offering insights into the latest advancements and...
eSkimming Security – Driving Bottom Line Results through Fraud Reduction and Revenue Maximization – Source: securityboulevard.com
Source: securityboulevard.com – Author: Scott Fiesel by Source Defense Even with the PCI DSS 4.0 deadline now behind us, many organizations are still exposed to costly...
BSidesLV24 – PasswordsCon – Long Live Short Lived Credentials – Auto-Rotating Secrets At Scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – PasswordsCon – Long Live Short Lived Credentials – Auto-Rotating Secrets At Scale...
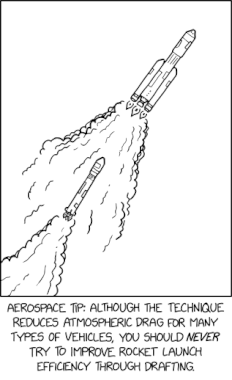
Randall Munroe’s XKCD ‘Drafting’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, May 28, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
RSA and Bitcoin at BIG Risk from Quantum Compute – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Researchers find we’ll need 20 times fewer qubits to break public-key encryption than previously believed. A new paper puts a fire...
Seceon Wins “MSP Platform Provider Vendor of the Year” at Technology Reseller Awards 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kriti Tripathi At Seceon, we’re honored to announce that we have been named the “MSP Platform Provider Vendor of the Year” at...
SBOM management and generation: How Sonatype leads in software supply chain visibility – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens As software supply chain threats become more complex, organizations need more than just vulnerability scanning — they need complete visibility...
Protecting Biomedical Devices in the Large Healthcare Enterprise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bob Palmer The Cyber Risk to the Healthcare Enterprise is Significant—and it’s Growing Due to Increased Connectivity of Medical Devices Biomedical devices...