Source: www.infosecurity-magazine.com – Author: Hackers have gained unauthorized, persistent access to about 9000 ASUS routers in an ongoing exploitation campaign, according to cyber intelligence firm GreyNoise....
Year: 2025
Cybersecurity Teams Generate Average of $36M in Business Growth – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Cybersecurity teams have become a significant contributor to business growth, contributing a median value of $36m per enterprise initiative they are involved...
#Infosec2025: Over 90% of Top Email Domains Vulnerable to Spoofing Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Over 90% of the world’s top email domains are vulnerable to spoofing, enabling cybercriminals to launch sophisticated phishing attacks, according to new...
Even $5M a year can’t keep top CISOs happy – Source: www.csoonline.com
Source: www.csoonline.com – Author: Many CISOs in large enterprises are unhappy with both their compensation and the resources they’re given to secure the business; despite this,...
Microsoft Entra’s billing roles pose privilege escalation risks in Azure – Source: www.csoonline.com
Source: www.csoonline.com – Author: Guest users with certain billing roles can create and own subscriptions, potentially gaining persistence and privilege escalation within an organization’s Azure environment....
6 rising malware trends every security pro should know – Source: www.csoonline.com
Source: www.csoonline.com – Author: From infostealers commoditizing initial access to a more targeted approach to ransomware attacks, cybercriminals’ malware tools, tactics, and techniques are evolving rapidly....
Most LLMs don’t pass the security sniff test – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISOs are advised to apply the same evaluation discipline to AI as they do to any other app in the enterprise. Almost...
Separating hype from reality: How cybercriminals are actually using AI – Source: www.csoonline.com
Source: www.csoonline.com – Author: Countering more advanced AI-driven threats requires that we collectively evolve our defenses, and the good news is that many security practitioners are...
Smashing Security podcast #419: Star Wars, the CIA, and a WhatsApp malware mirage – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Why is a cute Star Wars fan website now redirecting to the CIA? How come Cambodia has become the world’s...
RSAC Fireside Chat: ‘Purple’ teams dismantle the reactive trap — and can help restore cyber readiness – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido Reactive security isn’t just outdated — it’s become a liability. Attackers have figured out how to weaponize...
Find the Best CIAM Solution for Your Business: A Comprehensive Guide to Modern Customer Identity Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dev Kumar Understanding how to choose the right Customer Identity and Access Management (CIAM) solution can feel overwhelming, especially when you’re evaluating...
What Your Traffic Logs Aren’t Telling You About Cloud Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Hazel Raoult Cloud security isn’t just about merely collecting data. You need to extract meaning from it if you want to actually...
We’re Switching to Calendar Versioning: Here’s Why – Source: securityboulevard.com
Source: securityboulevard.com – Author: Granville Schmidt Calendar Versioning is a system where version numbers are tied directly to the release date. Our new format is: .....
In The News | Locking Up Phones, Logging Into AI: Classrooms Navigate New Tech Amid Public Debate – Source: securityboulevard.com
Source: securityboulevard.com – Author: Katie Fritchen This article was originally published in Unite.AI on 05/14/25. School policies around phone use are changing—and fast. In Ontario, Canada...
BSidesLV24 – PasswordsCon – CVE Hunting: Wi-Fi Routers, OSINT & ‘The Tyranny Of The Default’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – PasswordsCon – CVE Hunting: Wi-Fi Routers, OSINT & ‘The Tyranny Of The...
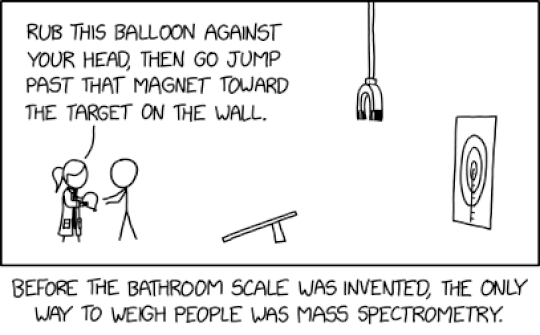
Randall Munroe’s XKCD ‘Mass Spec’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, May 29, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
FTC Orders GoDaddy to Bolster its Security After Years of Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Federal regulators are telling giant web hosting firm GoDaddy that it needs to drastically improve its security operations following a...
Your Mobile Apps May Not Be as Secure as You Think… – FireTail Blog – Source: securityboulevard.com
Source: securityboulevard.com – Author: FireTail – AI and API Security Blog May 28, 2025 – Lina Romero – Your Mobile Apps May Not Be as Secure...
How HealthTech Startups Can Build Scalable Data Governance Frameworks from Day One – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ashley Garvin Launching a HealthTech startup without data governance is like building a hospital with no patient records: risky, chaotic, and destined...
BSidesLV24 – PasswordsCon – Zero Downtime Credential Rotation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – PasswordsCon – Zero Downtime Credential Rotation Author/Presenter: Kenton McDonough Our sincere appreciation...
Pakistan Arrests 21 in ‘Heartsender’ Malware Service – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Authorities in Pakistan have arrested 21 individuals accused of operating “Heartsender,” a once popular spam and malware dissemination service that operated...
Hundreds of Web Apps Have Full Access to Microsoft OneDrive Files – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Implementing Secure by Design Principles for AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Diana Kelley Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Cellcom Restores Regional Mobile Services After Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Why Take9 Won’t Improve Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Bruce Schneier, Arun Vishwanath Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Have Your Say: Dark Reading Seeks Your Input – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kelly Jackson Higgins, Editor-in-Chief, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Zscaler Announces Deal to Acquire Red Canary – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
Location Tracking App for Foreigners in Moscow – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Russia is proposing a rule that all foreigners in Moscow install a tracking app on their phones. Using a mobile...
AI-Generated Carbon Black Detection Rule for DarkCrystal RAT Campaign – Source: socprime.com
Source: socprime.com – Author: Steven Edwards How It Works Uncoder AI processes threat reports like CERT-UA#14045 on DarkCrystal RAT and generates Carbon Black-compatible detection logic. This...
Vulnerabilities in CISA KEV Are Not Equally Critical: Report – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Security flaws in CISA’s Known Exploited Vulnerabilities (KEV) catalog should be treated with urgency based on environmental context assessments, according...