Source: www.cyberdefensemagazine.com – Author: News team AI is transforming the way work gets done across industries. But while it improves business efficiencies, it also arms cybercriminals...
Year: 2025
Telcom Security: The Intersection of Critical Infrastructure – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Telecommunications service providers (TSP) are foundational to the functioning of our modern technical society, serving as the conduit through which...
Free Wi-Fi Leaves Buses Vulnerable to Remote Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Researchers demonstrated that smart buses, the transportation vehicles that incorporate various systems to improve safety, efficiency, and passenger experience, can...
The Future of API Security Reviews – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team As organizations increasingly rely on application programming interfaces (APIs) to facilitate communication and data exchange between software systems, these “gates”...
SMBs Know the Risks, So Why Are Cybercriminals Still Winning? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Cybercriminals are no longer primarily focused on large enterprises. They now see small- and medium-sized businesses (SMBs) as prime targets...
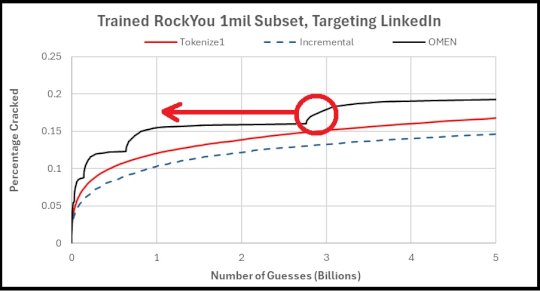
OMEN Improvements – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Weir “If I had an hour to solve a problem, I would spend 55 minutes thinking about the problem and five...
Tips to Protect Yourself on LinkedIn from Fraud, Social Engineering, and Espionage – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist LinkedIn is a great communication tool for business professionals that informs, provides opportunities, and fosters collaboration — which is exactly why...
Friday Squid Blogging: New Vulnerability in Squid HTTP Proxy Server – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments finagle • August 9, 2025 6:47 AM I was asked recently to do a security audit on a...
Google Project Zero Changes Its Disclosure Policy – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Google’s vulnerability finding team is again pushing the envelope of responsible disclosure: Google’s Project Zero team will retain its existing...
Former New York Times Cyber Reporter Issues Chilling Warning at Black Hat – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Matt Gonzales Nicole Perlroth, former New York Times reporter and founding partner of Silver Buckshot Ventures, speaking at Black Hat 2025 in...
KrebsOnSecurity in New ‘Most Wanted’ HBO Max Series – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A new documentary series about cybercrime airing next month on HBO Max features interviews with Yours Truly. The four-part series follows...
Are You Sending the Wrong Signals? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The Salt team has spent the last 5-10 years producing blogs, comparison documents and webinars which highlight our credentials versus...
VCF 9.0 Live Patching Ends Maintenance Window Dread – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Hollingsworth For IT administrators, two words sure to cause undue stress are “patching cycle.” It’s a necessary process fraught with challenges....
Randall Munroe’s XKCD ‘Geologic Periods’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the cosmic humor & dry-as-the-desert wit of Randall Munroe, creator of XKCD Permalink The post Randall Munroe’s XKCD ‘Geologic...
Survey Sees Drop in Cybersecurity Spending Growth Rates – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A survey of 587 CISOs published this week finds security budget growth dropped to 4%, down from 8% in 2024,...
Tea App Data Breach Fallout: A New App with Security Flaws and Lawsuits – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt In the wake of the high-profile data breaches of the popular and controversial Tea app, another app called TeaOnHer for...
60 RubyGems Packages Steal Data From Annoying Spammers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
BigID Launches Shadow AI Discovery to Uncover Rogue Models and Risky AI Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This website is...
PwC Announces Addition of Morgan Adamski to Leadership of Cyber, Data & Technology Risk Platform – Source: www.darkreading.com
Source: www.darkreading.com – Author: Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This website is...
Ransomware Attacks Fall by Almost Half in Q2 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This website is...
Cybersecurity Incident at Allianz Life Exposes Personal Information of Hundreds of Thousands – Source: www.darkreading.com
Source: www.darkreading.com – Author: Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This website is...
860K Compromised in Columbia University Data Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Redefining the Role: What Makes a CISO Great – Source: www.darkreading.com
Source: www.darkreading.com – Author: Lane Sullivan Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Data Dump From APT Actor Yields Clues to Attacker Capabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Attackers Target the Foundations of Crypto: Smart Contracts – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Prime Security Wins Black Hat’s Startup Spotlight Competition – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
What ‘CMMC 3.0’ Really Means for Government Contractors – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kyle Dewar Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Black Hat: Researchers demonstrate zero-click prompt injection attacks in popular AI agents – Source: www.csoonline.com
Source: www.csoonline.com – Author: Researchers from Zenity have found multiple ways to inject rogue prompts into agents from mainstream vendors to extract sensitive data from linked...
ECScape: New AWS ECS flaw lets containers hijack IAM roles without breaking out – Source: www.csoonline.com
Source: www.csoonline.com – Author: Naor Haziz’s discovery shows how a compromised container on EC2-backed ECS tasks can impersonate the ECS agent and steal IAM credentials from...
Beyond cryptocurrency: Blockchain 101 for CISOs and why it matters – Source: www.csoonline.com
Source: www.csoonline.com – Author: Opinion Aug 8, 20258 mins Data and Information SecurityEncryptionRegulation Blockchain is emerging as a powerful tool for CISOs to close trust gaps...