Source: www.infosecurity-magazine.com – Author: The FBI has updated its alert about fake lawyers defrauding victims of cryptocurrency scams, adding due diligence measures to help victims. The...
Year: 2025
Hacked Law Enforcement and Government Email Accounts Sold on Dark Web for $40 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Cybercriminals are selling access to active law enforcement and government email accounts for as little as $40 on the dark web, according...
Fortinet Warns Exploit Code Available for Critical Vulnerability – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Sysadmins have been urged to prioritize updating a new critical vulnerability in Fortinet’s FortiSIEM solution, as exploit code is currently circulating in...
Campaigners Slam Expansion of Police Facial Recognition Schemes in UK – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Rights groups have reacted angrily to the news that the government is expanding police use of live facial recognition (LFR) without adequate...
7 reasons the SOC is in crisis — and 5 steps to fix it – Source: www.csoonline.com
Source: www.csoonline.com – Author: Breaches continue to happen as SOC analysts deal with too many alerts or rules of engagement that stops them from acting. Here...
FIDO ausgehebelt – Source: www.csoonline.com
Source: www.csoonline.com – Author: Sicherheitsforscher haben einen Weg gefunden, FIDO-basierte Authentifizierungen zu umgehen. Bestimmte Implementierungen der FIDO-Authentifizierung – insbesondere Windows Hello for Business – können laut...
Russian APT group Curly COMrades employs novel backdoor and persistence tricks – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Aug 13, 20255 mins Advanced Persistent ThreatsMalware A newly identified group launched attacks against key organizations in Georgia and Moldova using...
DEF CON research takes aim at ZTNA, calls it a bust – Source: www.networkworld.com
Source: www.networkworld.com – Author: Is zero trust a bust? At the DEF CON 33 security conference, researchers from AmberWolf provided a scathing report on the state of...
Critical SSH vulnerabilities expose enterprise network infrastructure as patching lags – Source: www.networkworld.com
Source: www.networkworld.com – Author: Researcher at DEF CON reveals some critical challenges in widely used SSH protocol and provider recommendations on how to make it better....
9 things CISOs need to know about the dark web – Source: www.csoonline.com
Source: www.csoonline.com – Author: What CISOs need to know about the trade of stolen information, new marketplaces, the availability of malicious tools, and the impact of...
Empowering Graduate Women in SWE: Meet the GradSWE Affinity Group
As part of their affinity group’s spotlight month, GradSWE reviews their mission and highlights their leadership. Source Views: 1
Overcoming Barriers as a Woman Engineer in Academia: My Experience With SWE’s ALWE Program
Dr. Brittany MacDonald-MacAulay, the first full-time female engineering instructor in the history of her university, reflects on her experience in SWE’s ALWE program. Source Views: 0
‘MadeYouReset’ HTTP2 Vulnerability Enables Massive DDoS Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Researchers have discovered another attack vector that can be exploited to launch massive distributed denial-of-service (DDoS) attacks. The attack, dubbed...
Adobe Patches Over 60 Vulnerabilities Across 13 Products – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Adobe’s August 2025 Patch Tuesday updates address more than 60 vulnerabilities across 3D design, content creation, publishing and other types...
AI Applications in Cybersecurity – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Gadi Evrom • August 13, 2025 1:39 PM Thank you for covering our work. We felt it was...
SIGINT During World War II – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • August 13, 2025 8:31 AM @ Bruce, All, With regards, “This is the story of...
Black Hat Fireside Chat: Automation takes center stage as TLS lifespans grow ever shorter – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido The countdown is on for security teams still managing digital certificates with spreadsheets and manual workarounds. Related:...
Smashing Security podcast #430: Poisoned Calendar invites, ChatGPT, and Bromide – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content A poisoned Google Calendar invite that can hijack your smart home, a man is hospitalised after ChatGPT...
US Reportedly Hid Trackers in Shipments to Monitor AI Chips Diverted to China – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Topic — Artificial Intelligence Published August 13, 2025 Trackers were placed in the packaging and sometimes inside servers from Dell...
Microsoft’s Patch Tuesday: 100+ Updates Including Azure OpenAI Service, Memory Corruption Flaw – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Microsoft patched CVE-2025-50165, an “extremely high-risk” memory corruption flaw in its graphics component that could let attackers execute code over...
Hack of North Korean Spy’s Computer Exposes 8.9 GB of Espionage Operations – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Liz Ticong Image: thichaa/Envato Hackers have infiltrated the computer of a North Korean government spy, stealing and leaking 8.9 GB of secret...
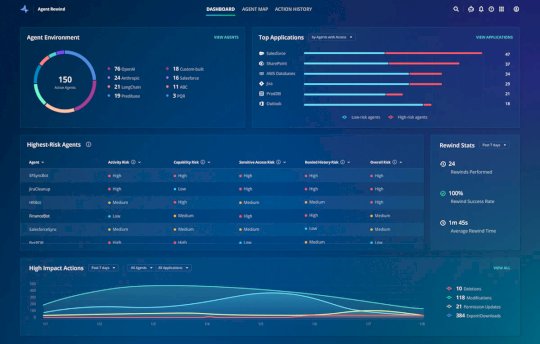
Fix AI Agent Mistakes With Rubrik’s Agent Rewind – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Aminu Abdullahi Topic — Artificial Intelligence Published August 13, 2025 Rubrik’s new Agent Rewind tool can trace, audit, and safely reverse AI...
North Korea Attacks South Koreans With Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Fortinet Products Are in the Crosshairs Again – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Whispers of XZ Utils Backdoor Live on in Old Docker Images – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Popular AI Systems Still a Work-in-Progress for Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Patch Now: Attackers Target OT Networks via Critical RCE Flaw – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
What the LockBit 4.0 Leak Reveals About RaaS Groups – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michele Campobasso Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
How an AI-Based ‘Pen Tester’ Became a Top Bug Hunter on HackerOne – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
How to Build, Optimize, & Manage AI on Google Kubernetes Engine – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Suderman Artificial Intelligence (AI) is quickly changing modern enterprises, but harnessing its full potential demands not only excellent models, but infrastructure...