Source: www.cyberdefensemagazine.com – Author: News team The Common Vulnerability Scoring System (CVSS) offers a standardized framework for characterizing and scoring vulnerabilities, helping the effort for vulnerability...
Year: 2025
Beyond the Hype: How to Set Up Your AI Project for Real Success – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Today, AI is the golden ticket to productivity gains and competitive advantage. From automating repetitive tasks to unearthing insights hidden in oceans...
Digital transformation 2025: What’s in, what’s out – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: This year CIOs will want to increase focus on developing AI-ready employees, improving data governance, and enhancing training efforts rather than take...
Malware metamorphosis: 2024 reflections and 2025 predictions. – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Welcome in! You’ve entered, Only Malware in the Building. Join us each month to sip tea and solve mysteries about today’s most...
What Boards Need To Know On Digital And Cybersecurity Governance In 2025 – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Will digital governance move backwards in 2025? Photo by Hulton Archive/Getty Images. Getty Images The year 2024 was a relatively big year...
Cybersecurity leaders scramble to educate employees on generative AI threats – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Cybersecurity leaders scramble to educate employees on generative AI threats This graphic shows the most commonly impersonated brands by online scammers, based...
Threat Actors Exploit a Critical Ivanti RCE Bug, Again – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Lobro via Alamy Stock Photo A Chinese threat actor is once again exploiting Ivanti remote access devices...
Hacking The Planet – Hack The World 2017 Recap – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. After 1 month of our community’s best and brightest going head to head to be named Hack The World 2017 champion,...
Meloni Says Italy Is Exploring Deals on Telecoms Security, but Denies Private Talks With Musk – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Italy’s Premier Giorgia Meloni said Thursday that her government is in talks with several private companies, including Elon Musk’s SpaceX,...
Friday Squid Blogging: Cotton-and-Squid-Bone Sponge – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier News: A sponge made of cotton and squid bone that has absorbed about 99.9% of microplastics in water samples in...
Apps That Are Spying on Your Location – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier 404 Media is reporting on all the apps that are spying on your location, based on a hack of the...
Q&A with Jane Frankland: GDPR, CISOs, and Women in Cybersecurity – Source:www.hackerone.com
Source: www.hackerone.com – Author: luke. Jane Frankland is an award-winning entrepreneur, speaker, and consultant in cybersecurity and entrepreneurism. For more than 20 years, Jane has been...
Four Steps Security Teams Can Take to Unlock Resources In Budget-Constrained Environments – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Imagine walking into a board meeting with a tool that shows your board exactly how protected the organization is, based...
SWE Mid-Career Professionals Affinity Group Highlights
Each month, SWE spotlights one of our 22 Affinity Groups (AGs). As part of their spotlight month, the Mid-Career Professionals AG shares their AG’s background, goals,...
Navigating the Professional Engineer Exam Approval
Explore a step-by-step guide and tips to obtaining your PE licensure, presented by the Early Career Professionals Affinity Group as part of their spotlight month. Source...
2025 SaaS Security Word of the Year: Adaptability | Grip – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog Every year, we collectively look for ways to define our focus, to ground ourselves in something that guides us...
Strategic Approaches to Enhance Data Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn How Crucial Are Non-Human Identities to Data Security? Data security has long been the bedrock of digital enterprises, providing robust...
The Cost of Complacency in Credential Hygiene – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog In case you missed it, PowerSchool, a leading provider of cloud-based software solutions for K-12 schools, recently announced a...
DEF CON 32 – Practical Exploitation of DoS in Bug Bounty – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Practical Exploitation of DoS in Bug Bounty Author/Presenter: Roni Lupin...
Below the Surface Winter 2024 Edition – The Year in Review – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland The Year of the Typhoon Highlights from this edition: The Year of the Typhoon: Critical infrastructure was in the path of...
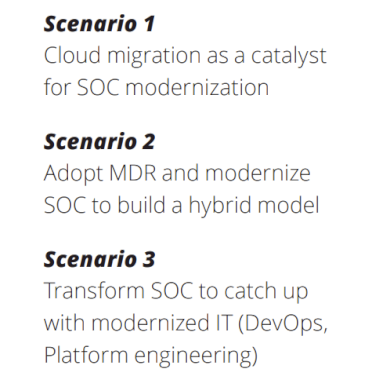
New Paper: “Future of SOC: Transform the ‘How’” (Paper 5) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin After a long, long, long writing effort … eh … break, we are ready with our 5th Deloitte and Google Cloud Future...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #320 – Aligning Teams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Friday, January 10, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Hackers Attack PowerSchool, Expose K-12 Teacher and Student Data – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The personal information of some students and teachers in school districts across the United States was exposed in a data...
Unlock collaboration and efficiency in software management with SBOMs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens As software supply chains grow more complex, organizations face increasing challenges to manage and secure open source components. *** This...
DEF CON 32 – Programming A CTS-V Gauge Cluster Into An ATS-V: Out Of Pure Spite – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Programming A CTS-V Gauge Cluster Into An ATS-V: Out Of...
2025 Cybersecurity and AI Predictions – Source: www.csoonline.com
Source: www.csoonline.com – Author: The cybersecurity and AI landscape continues to evolve at a breathtaking pace, and with it, the associated risks. The cybersecurity and AI...
Software-Lücke bei KigaRoo: Millionen Kita-Daten offen im Netz – Source: www.csoonline.com
Source: www.csoonline.com – Author: Aufgrund einer Schwachstelle in der Software KigaRoo standen mehr als zwei Millionen Kita-Daten offen im Netz. Die Lücke wurde inzwischen geschlossen. Die...
Malware targets Mac users by using Apple’s security tool – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 10 Jan 20253 mins EncryptionMalwarePhishing Using Apple’s proprietary string encryption, the malware evaded detection for months. A variant of the Banshee...
SEC rule confusion continues to put CISOs in a bind a year after a major revision – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 10 Jan 20256 mins Business IT AlignmentCSO and CISORegulation Despite a spate of recent actions exemplifying how the US Securities and...
6 Risk-Assessment-Frameworks im Vergleich – Source: www.csoonline.com
Source: www.csoonline.com – Author: IT-Risiken “so Pi mal Daumen” zu bewerten, kann ins Auge gehen. Mit diesen sechs Frameworks fahren Sie besser. Mit dem richtigen Framework...