Source: grahamcluley.com – Author: Graham Cluley Skip to content Ever wonder how those “free” browser extensions that promise to save you money actually work? We dive...
Year: 2025
Space Bears ransomware: what you need to know – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley What is Space Bears? Space Bear is a relatively new ransomware group that first appeared on the radar in April...
In Other News: Bank of America Warns of Data Breach, Trucking Cybersecurity, Treasury Hack Linked to Silk Typhoon – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy stories that might have slipped under the radar. We provide...
Banshee macOS Malware Expands Targeting – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Banshee macOS information stealer has been updated to expand its target list to systems using the Russian language, cybersecurity...
Major Addiction Treatment Firm BayMark Confirms Ransomware Attack Caused Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Healthcare and substance abuse treatment provider BayMark Health Services has started notifying patients that their personal information was stolen in...
PayPal Phishing Campaign Employs Genuine Links to Take Over Accounts – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A new phishing campaign relies on legitimate links to trick victims into logging in and giving attackers control of their...
Microsoft DRM Hacking Raises Questions on Vulnerability Disclosures – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A research project targeting vulnerabilities in widely used content access and protection technology from Microsoft raises some questions over certain...
Hursti hacks, DEF CON villages, and the Dubious state of electronic voting – Source:www.hackerone.com
Source: www.hackerone.com – Author: luke. Harri Hursti is one of the most knowledgeable hackers of election technology. He’s most known for the eponymous hack in 2005...
Zero-Day Vulnerability in Ivanti VPN – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Aaron • January 9, 2025 3:11 PM What does it say about the current philosophies of the corporate...
Fortifying The Links – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In today’s hyper-connected world, supply chains are the lifeblood of industries, spanning across continents and involving numerous third-party vendors. While...
The Key to AI-Enabled Multi-Coalition Warfare – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In February, the top artificial intelligence (AI) official at the Department of Defense (DoD) laid out his vision for AI-enabled warfare....
Chinese APT Group Is Ransacking Japan’s Secrets – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Birgit Korber via Alamy Stock Photo The National Police Agency and the National Center of...
Banshee 2.0 Malware Steals Apple’s Encryption to Hide on Macs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Charles Walker Collection via Alamy Stock Photo The macOS infostealer “Banshee” has been spotted skating by antivirus...
Hacking Group ‘Silk Typhoon’ Linked to US Treasury Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: World History Archive via Alamy Stock Photo NEWS BRIEF The Chinese threat actor group known...
New AI Challenges Will Test CISOs & Their Teams in 2025 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Josh Lemos Source: marcos alvarado via Alamy Stock Photo COMMENTARY Security teams have always had to adapt to change, but new developments...
Chinese-linked Hackers May Be Exploiting Latest Ivanti Vulnerability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Management software maker Ivanti continues to struggle with security flaws in its products – this week announcing two more vulnerabilities...
DEF CON 32 – Reflections on a Decade in Bug Bounties – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, January 9, 2025 Home » Security Bloggers Network » DEF CON 32 – Reflections on a Decade in Bug...
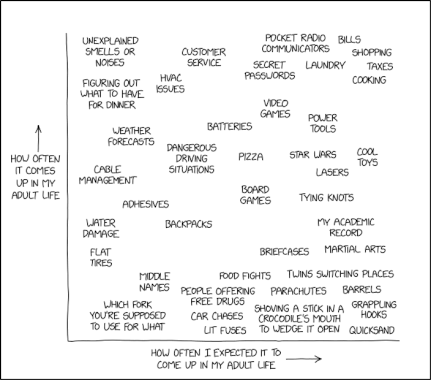
Randall Munroe’s XKCD ‘Features of Adulthood’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Open Interfaces Needed to Cut Security Operations Costs & Boost Efficiency – Source: securityboulevard.com
Source: securityboulevard.com – Author: George V. Hulme While AI/ML and automation promise to help streamline and reduce security operation costs, these efforts could be significantly boosted...
8 Cyber Predictions for 2025: A CSO’s Perspective – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepen Desai As we step into 2025, the cyberthreat landscape is once again more dynamic and challenging than the year before. In...
DEF CON 32 – Reverse Engineering And Hacking Ecovacs Robots – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Reverse Engineering And Hacking Ecovacs Robots Authors/Presenters: Dennis Giese, Braelynn...
Vulnerability Research Highlights 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Gerste With more and more code generated by humans and AI, keeping track of its security remains a top priority. This...
The Hidden Costs of Poor Access Management: Why Small Businesses Can’t Afford to Ignore It – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author Imagine you run a growing software company. Your team is expanding, projects are flowing, and...
SafeBreach 2024 Year in Review: Reflections from Co-Founder & CEO Guy Bejerano – Source: securityboulevard.com
Source: securityboulevard.com – Author: Guy Bejerano Author: Guy Bejerano, CEO & Co-Founder, SafeBreach Happy new year! 2025 is underway and the SafeBreach team is off to...
Security Implications of Configuration Drift – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mariusz Michalowski Configuration drift occurs when systems deviate from their intended settings over time. This seemingly minor issue can lead to significant...
Hackers Descend on London for First Ever UK Live Hacking Event: H1-4420 – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. On Saturday, June 16, almost 50 hackers gathered from across the world to hack one of the most popular and mature...
Legitimate PoC exploited to spread information stealer – Source: www.csoonline.com
Source: www.csoonline.com – Author: It’s another example of how openly-posted proofs of concepts are being abused to sucker security researchers. A recently copied and abused open...
Ivanti zero-day exploited by APT group that previously targeted Connect Secure appliances – Source: www.csoonline.com
Source: www.csoonline.com – Author: Vulnerability revealed by Ivanti has been exploited by the same group that targeted Connect Secure from January 2024. Researchers from Google’s Mandiant...
New Mirai botnet targets industrial routers – Source: www.csoonline.com
Source: www.csoonline.com – Author: Security researchers warn of a new variant of the Mirai botnet. Attackers used it for zero-day exploits on industrial routers. According to...
SonicWall firewall hit with critical authentication bypass vulnerability – Source: www.csoonline.com
Source: www.csoonline.com – Author: The company urged admins to immediately patch their firewalls to fend off threats of easy exploitation. SonicWall is warning customers of a...