Source: www.cyberdefensemagazine.com – Author: News team Imagine walking into a board meeting with a tool that shows your board exactly how protected the organization is, based...
Year: 2025
SWE Mid-Career Professionals Affinity Group Highlights
Each month, SWE spotlights one of our 22 Affinity Groups (AGs). As part of their spotlight month, the Mid-Career Professionals AG shares their AG’s background, goals,...
Navigating the Professional Engineer Exam Approval
Explore a step-by-step guide and tips to obtaining your PE licensure, presented by the Early Career Professionals Affinity Group as part of their spotlight month. Source...
2025 SaaS Security Word of the Year: Adaptability | Grip – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog Every year, we collectively look for ways to define our focus, to ground ourselves in something that guides us...
Strategic Approaches to Enhance Data Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn How Crucial Are Non-Human Identities to Data Security? Data security has long been the bedrock of digital enterprises, providing robust...
The Cost of Complacency in Credential Hygiene – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog In case you missed it, PowerSchool, a leading provider of cloud-based software solutions for K-12 schools, recently announced a...
DEF CON 32 – Practical Exploitation of DoS in Bug Bounty – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Practical Exploitation of DoS in Bug Bounty Author/Presenter: Roni Lupin...
Below the Surface Winter 2024 Edition – The Year in Review – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland The Year of the Typhoon Highlights from this edition: The Year of the Typhoon: Critical infrastructure was in the path of...
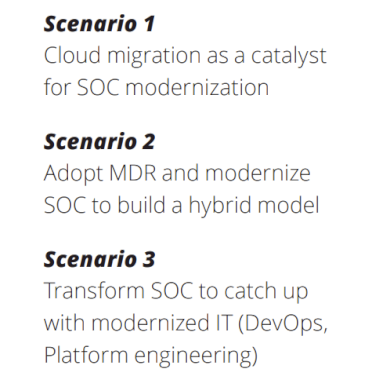
New Paper: “Future of SOC: Transform the ‘How’” (Paper 5) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin After a long, long, long writing effort … eh … break, we are ready with our 5th Deloitte and Google Cloud Future...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #320 – Aligning Teams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Friday, January 10, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Hackers Attack PowerSchool, Expose K-12 Teacher and Student Data – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The personal information of some students and teachers in school districts across the United States was exposed in a data...
Unlock collaboration and efficiency in software management with SBOMs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens As software supply chains grow more complex, organizations face increasing challenges to manage and secure open source components. *** This...
DEF CON 32 – Programming A CTS-V Gauge Cluster Into An ATS-V: Out Of Pure Spite – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Programming A CTS-V Gauge Cluster Into An ATS-V: Out Of...
2025 Cybersecurity and AI Predictions – Source: www.csoonline.com
Source: www.csoonline.com – Author: The cybersecurity and AI landscape continues to evolve at a breathtaking pace, and with it, the associated risks. The cybersecurity and AI...
Software-Lücke bei KigaRoo: Millionen Kita-Daten offen im Netz – Source: www.csoonline.com
Source: www.csoonline.com – Author: Aufgrund einer Schwachstelle in der Software KigaRoo standen mehr als zwei Millionen Kita-Daten offen im Netz. Die Lücke wurde inzwischen geschlossen. Die...
Malware targets Mac users by using Apple’s security tool – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 10 Jan 20253 mins EncryptionMalwarePhishing Using Apple’s proprietary string encryption, the malware evaded detection for months. A variant of the Banshee...
SEC rule confusion continues to put CISOs in a bind a year after a major revision – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 10 Jan 20256 mins Business IT AlignmentCSO and CISORegulation Despite a spate of recent actions exemplifying how the US Securities and...
6 Risk-Assessment-Frameworks im Vergleich – Source: www.csoonline.com
Source: www.csoonline.com – Author: IT-Risiken “so Pi mal Daumen” zu bewerten, kann ins Auge gehen. Mit diesen sechs Frameworks fahren Sie besser. Mit dem richtigen Framework...
China’s UNC5337 Exploits a Critical Ivanti RCE Bug, Again – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Lobro via Alamy Stock Photo A Chinese threat actor is once again exploiting Ivanti remote access devices...
Fake CrowdStrike ‘Job Interviews’ Become Latest Hacker Tactic – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: ImageBroker.com GmbH & Co. KG via Alamy Stock Photo NEWS BRIEF Cybercriminals have picked up...
Russia Carves Out Commercial Surveillance Success Globally – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Golden Dayz via Shutterstock A half-dozen governments in Central Asia and Latin American have purchased the System...
The Path Toward Championing Diversity in Cybersecurity Education – Source: www.darkreading.com
Source: www.darkreading.com – Author: Laurie Salvail Source: Aleksei Gorodenkov via Alamy Stock Photo COMMENTARY As we enter 2025 and face an new presidential administration, the United...
Australian IT Sector Maintains Strong Employment Outlook for 2025 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott The IT sector remains a bright spot in the Australian job market heading into 2025, boasting the most positive employment...
What’s Next for Open Source Software Security in 2025? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Open-source software is common throughout the tech world, and tools like software composition analysis can spot dependencies and secure them....
Cybercriminals Use Fake CrowdStrike Job Offers to Distribute Cryptominer – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Written by Cybercriminals are impersonating CrowdStrike recruiters to distribute a cryptominer on victim devices. CrowdStrike said it identified phishing campaign exploiting its...
Slovakia Hit by Historic Cyber-Attack on Land Registry – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A large-scale cyber-attack originating from outside Slovakia’s borders has hit the information system of the Office of Geodesy, Cartography and Cadastre of...
Medusind Breach Exposes Sensitive Patient Data – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: US dental and medical billing firm Medusind is notifying over 360,000 customers that their personal, financial and medical data may have been...
Fake PoC Exploit Targets Security Researchers with Infostealer – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Threat actors have created a fake proof-of-concept (PoC) exploit for a critical Microsoft vulnerability, designed to lure security researchers into downloading and...
Drug addiction treatment service admits attackers stole sensitive patient data – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones BayMark Health Services, one of the biggest drug addiction treatment facilities in the US, says it is notifying some patients...
Devs sent into security panic by ‘feature that was helpful … until it wasn’t’ – Source: go.theregister.com
Source: go.theregister.com – Author: Simon Sharwood On Call Velkomin, Vælkomin, Hoş geldin, and welcome to Friday, and therefore to another edition of On Call – The...