Source: www.csoonline.com – Author: News 03 Mar 20256 mins CyberattacksGovernment ITRansomware Press reports suggest that US Cybercom is standing down from tracking Russia’s offensive cyber operations,...
Year: 2025
Download the AI Risk Management Enterprise Spotlight – Source: us.resources.csoonline.com
Source: us.resources.csoonline.com – Author: Register Download the March 2025 issue of the Enterprise Spotlight from the editors of CIO, Computerworld, CSO, InfoWorld, and Network World. See...
Download the UEM vendor comparison chart, 2025 edition – Source: us.resources.csoonline.com
Source: us.resources.csoonline.com – Author: Home Mobile Device Management Foundry Editorial Register From the editors of Computerworld, this enterprise buyer’s guide helps IT staff understand what the...
Forscher entdecken LLM-Sicherheitsrisiko – Source: www.csoonline.com
Source: www.csoonline.com – Author: Forscher haben Anmeldeinformationen in den Trainingsdaten von Large Language Models entdeckt. BOY ANTHONY – Shutterstock.com Beliebte LLMs wie DeepSeek werden mit Common...
Engineering a Brighter Future: The State of Women and Minorities in Engineering
Join the 50K Coalition’s founding members in this important video session! Source Views: 0
Decoding Your STEM Career Journey: Navigating Work-Life Phases
Gunjan Goswami shares about three career phases that many engineers experience and how to thrive in each one. Source Views: 0
Meet SWENexter Nishka Sharma
Nishka went from being hesitant about engineering to embracing her future as a STEM leader. Learn how she is encouraging other young women to pursue STEM...
Celebrating Black History Month With SWE
To commemorate the occasion, the Society of Women Engineers (SWE) has compiled some of our top blog posts, podcast episodes, and magazine articles that highlight the...
What Recruiters Look for at Virtual Career Fairs
Use these tips to make a positive first impression with recruiters, then register for SWE’s upcoming Virtual Career Fair for Professionals on May 7! Source Views:...
SWE Diverse Podcast Ep 247: Aviation, Dance, and STEM Outreach: A Conversation With Deysi Melgar
Deysi Melgar shares her inspiring journey as a STEM advocate and aviation leader in this episode of Diverse: a SWE podcast! Source Views: 0
Win up to $750 for Your SWE Community College Affiliate!
The SWE Community Colleges Affinity Group (AG) and SWE’s Community College Affiliate Support and Expansion (CCASE) Program have partnered to present a video challenge for SWE...
5 Career Mistakes Common to Both Early Career and Seasoned Professionals
Asia Bribiesca-Hedin shares five critical career mistakes to avoid in your professional engineering journey. Plus, join her free course “Creating Confidence When You Are the First...
7 Stages of Non-Human Identity Security Maturity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Kaplan With no centralized inventory or management system, organizations struggled to answer basic questions like ‘What secrets do we have?’, ‘Who...
Bubba AI, Inc. is launching Comp AI to help 100,000 startups get SOC 2 compliant by 2032. – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire San Francisco, California, March 3rd, 2025, CyberNewsWire With the growing importance of security compliance for startups, more companies are seeking to...
DEF CON 32 – Differential Privacy Beyond Algorithm: Challenges For Deployment – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Differential Privacy Beyond Algorithm: Challenges For Deployment Author/Presenter: Rachel Cummings...
What Is Credential Management? Best Practices and Examples – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Strong credentials safeguard your digital resources, but common mistakes like weak passwords, credential reuse, and exposed secrets give attackers an...
What Is Code Scanning? Approaches and Best Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Identifying security flaws early in the software development lifecycle (SDLC) prevents vulnerabilities from reaching production, where they become more complex...
6 Effective Secret Scanning Tools – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Secret scanning tools identify and protect sensitive information that may be exposed within software assets. Developers often embed secrets like...
Randall Munroe’s XKCD ‘Giants’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Monday, March 3, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Security Pros Push Back as Trump Orders Halt to Cyber Ops vs. Russia – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The Trump Administration’s reported move to stop federal agencies from offensive cyber operations and investigations against Russia drew sharp rebuke...
DEF CON 32 – Cybersecurity Schoolhouse Rock – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » DEF CON 32 – Cybersecurity Schoolhouse Rock by Marc Handelman on...
Enhancing Application Security | Contrast ADR and Splunk | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Contrast Marketing Have you silenced WAF alerts in your SIEM or just stopped sending them altogether? You’re not alone. Many SOCs find...
Mozilla Revises Firefox Terms of Use After Inflaming Users Over Data Usage – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Esther Shein Image: iStock Mozilla wants to set the record straight: The company needs a license “to make some of the basic...
EU’s New Product Liability Directive & Its Cybersecurity Impact – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jatin Mannepalli Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Latin American Orgs Face 40% More Attacks Than Global Average – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Cisco’s SnapAttack Deal Expands Splunk’s Capabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
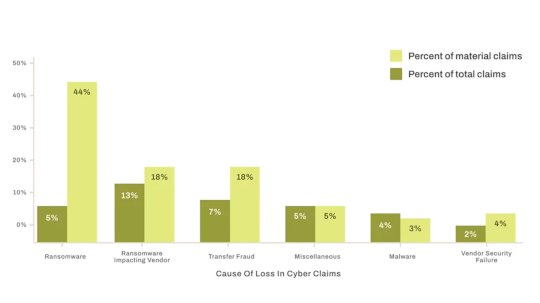
Third-Party Risk Top Cybersecurity Claims – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Stop targeting Russian hackers, Trump administration orders US Cyber Command – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley For years, the United States has joined with much of the rest of the world, in declaring that Russia poses...
Mobile malware evolution in 2024 – Source: securelist.com
Source: securelist.com – Author: Anton Kivva These statistics are based on detection alerts from Kaspersky products, collected from users who consented to provide statistical data to...
Black Basta Leak Offers Glimpse Into Group’s Inner Workings – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend A massive hoard of internal chats has been leaked from the Black Basta ransomware group, rivalling the Conti leaks of...