Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Year: 2025
‘EncryptHub’ OPSEC Failures Reveal TTPs & Big Plans – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Under Pressure: US Charges China’s APT-for-Hire Hackers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
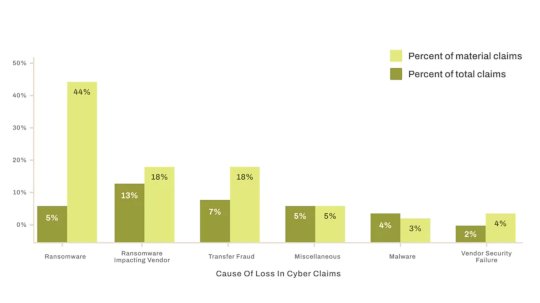
Third-Party Risk Tops Cybersecurity Claims – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
SWE Pune Affiliate Empowering Tomorrow’s Tech Leaders
Highlights from campus to corporate tech program with Vishwakarma Institute of Technology Source Views: 2
Caring for Elders With Mary Zeis
Each month, SWE spotlights one of our affinity groups. As part of their spotlight month, the Late Career and Retiree Affinity Group explores caring for elders...
Armis Acquires Otorio to Expand OT and CPS Security Suite – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News California cyber exposure management firm Armis on Thursday announced the acquisition of Otorio, a deal that adds technology for operational...
How Social Engineering Sparked a Billion-Dollar Supply Chain Cryptocurrency Heist – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Last week’s $1.4 billion cryptocurrency heist was the result of a multi-pronged attack that combined social engineering, stolen AWS session...
House Passes Bill Requiring Federal Contractors to Implement Vulnerability Disclosure Policies – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The House of Representatives has passed a bill aimed at requiring federal contractors to have a vulnerability disclosure policy (VDP)....
Nigerian Accused of Hacking Tax Preparation Firms Extradited to US – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A Nigerian national appeared in a US court on Wednesday facing computer intrusion, wire fraud, government money theft, identity theft,...
Financial Organizations Urge CISA to Revise Proposed CIRCIA Implementation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A group of financial organizations sent an open letter to the US cybersecurity agency CISA, urging it to rescind and...
BadBox Botnet Powered by 1 Million Android Devices Disrupted – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A second iteration of the BadBox botnet has been partially disrupted after impacting over one million Android devices worldwide, bot...
AIceberg Gets $10 Million in Seed Funding for AI Security Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs AIceberg announced on Thursday the launch of its AI trust platform, for which it raised $10 million in seed funding...
Exploited VMware ESXi Flaws Put Many at Risk of Ransomware, Other Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Scans show that tens of thousands of VMware ESXi instances are affected by the vulnerabilities disclosed recently as zero-days. On...
Indictments of Chinese Cyber Spies Reveal Hacker-For-Hire Operation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The indictments this week of 12 Chinese nationals accused of hacking into computer systems of an array of individuals and...
How can NHIs be incorporated into our overall security strategy? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Do Non-Human Identities Play a Significant Role in Our Security Strategy? Indeed, they do. Non-Human Identities (NHIs) are becoming increasingly...
What are the key security controls for NHIs at the executive level? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why Should CISOs Consider Non-Human Identities Security Controls? Did you know NHIs represent a significant portion of all entities in...
What role do NHIs play in our organization’s security posture? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn What Essential Role Do Non-Human Identities (NHIs) Play in Our Organization’s Security Posture? When our world increasingly moves towards digitalization,...
How can I align NHI management with our digital transformation initiatives? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Non-Human Identities Management Critical for Digital Transformation? Have you ever considered the sheer quantity of non-human identities (NHIs)...
What Is Data Leak Prevention? Benefits and Best Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Today’s organizations work with incredible quantities of data. From corporate trade secrets to customers’ and employees’ personal information, much of...
What Is an Identity Provider (IdP) and How Does It Work? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Managing online accounts shouldn’t feel like a chore. But when so many websites and systems require credentials, it’s hard to...
Patch Management Guide: Benefits and Best Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Developers periodically review software and release patches to remedy any bugs. When patches happen often, they can be hard to...
DEF CON 32 – War Stories – Hacking Millions Of Modems And Investigating Who Hacked My Modem – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – War Stories – Hacking Millions Of Modems And Investigating Who...
Votiro’s Proven Protection: Retroscan for Zero-Day Threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro On any given day, a seemingly harmless file may enter your organization, sometimes via your email system, bypassing every layer of...
Who is the DOGE and X Technician Branden Spikes? – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs At 49, Branden Spikes isn’t just one of the oldest technologists who has been involved in Elon Musk’s Department of Government...
Chinese APT Silk Typhoon exploits IT supply chain weaknesses for initial access – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis 06 Mar 20256 mins Advanced Persistent ThreatsGovernmentHacker Groups The threat group’s tactics mark a shift from direct exploits to lateral...
Hackerangriff auf Stadtwerke Schwerte – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Stadt Schwerte ist Opfer einer Cyberattacke. Auch Bürgerdienste sind betroffen. Aufgrund einer Cyberattacke auf die Stadtwerke Schwerte sind aktuell einige Dienste...
US charges 12 Chinese hackers in major government-backed espionage campaign – Source: www.csoonline.com
Source: www.csoonline.com – Author: Justice Department unveils indictments against Silk Typhoon group members, seizes domains in escalating cybersecurity standoff. US authorities have announced criminal charges against...
Badbox Android botnet disrupted through coordinated threat hunting – Source: www.csoonline.com
Source: www.csoonline.com – Author: Human Security, in collaboration with Google, Shadowserver and others, has sinkholed C2 operations affecting 500,000 infected machines. Badbox, the notorious Android malware...
Access Management Systems sind offene Türen für Hacker – Source: www.csoonline.com
Source: www.csoonline.com – Author: Falsch konfigurierte Zugangsverwaltungssysteme stellen für Unternehmen ein hohes Sicherheitsrisiko dar. Wenn Hacker biometrische Zugangsdaten erbeuten, können Sie erhebliche Schäden anrichten. shuttertsock –...