Source: securityboulevard.com – Author: Ayelen Torello On March 12, 2025, The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information...
Year: 2025
BSides Exeter 2024 – Blue Track – DFIR – Are We There Yet? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Promo » Cybersecurity » BSides Exeter 2024 – Blue Track – DFIR – Are We...
SafeBreach Coverage for US CERT AA25-071A (Medusa Ransomware) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tova Dvorin On March 12, 2025, the Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the Federal Bureau of Investigation (FBI)...
AD Lite Password Auditor Report: Key Insights and Data – Source: securityboulevard.com
Source: securityboulevard.com – Author: Enzoic 2024 Enzoic AD Lite Password Auditor Report In an era where cyber threats continue to evolve, password security remains one of...
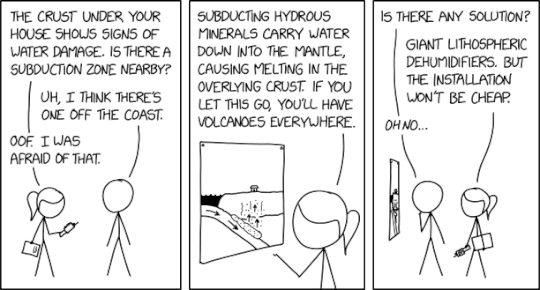
Randall Munroe’s XKCD ‘Water Damage’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Friday, March 14, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Silk Typhoon Targeting IT Supply Chains and Network Devices, Microsoft Reports – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Microsoft Threat Intelligence has issued new reporting about tactics being used by Silk Typhoon (also called APT27 or HAFNIUM by...
Unpatched Edimax Camera Flaw Exploited Since at Least May 2024 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A recently disclosed zero-day affecting Edimax devices has been exploited in the wild since at least May 2024, according to...
FreeType Zero-Day Being Exploited in the Wild – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Meta’s Facebook security team has raised an alarm after spotting live exploitation of a zero-day vulnerability in the widely used...
Cisco Patches 10 Vulnerabilities in IOS XR – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco on Wednesday announced patches for 10 vulnerabilities in IOS XR, including five that could be exploited to cause denial-of-service...
Grafana Flaws Likely Targeted in Broad SSRF Exploitation Campaign – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Grafana path traversal vulnerabilities have been exploited prior to a broad campaign targeting server-side request forgery (SSRF) bugs in multiple...
Microsoft Warns of Hospitality Sector Attacks Involving ClickFix – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A cybercrime group has been targeting organizations in the hospitality sector in attacks involving fake Booking.com emails and the use...
DeepSeek’s Malware-Generation Capabilities Put to Test – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Researchers at security firm Tenable have analyzed the ability of the Chinese gen-AI DeepSeek to develop malware such as keyloggers...
North Korean Hackers Distributed Android Spyware via Google Play – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A North Korean APT actor has been targeting Korean and English-speaking users with an Android surveillance tool distributed via Google...
Medusa Ransomware Made 300 Critical Infrastructure Victims – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Since June 2021, Medusa ransomware-as-a-service (RaaS) affiliates have hit over 300 critical infrastructure organizations, the US government warns. Medusa was...
Medusa Ransomware Detection: The FBI, CISA & Partners Warn of Increasing Attacks by Ransomware Developers and Affiliates Against Critical Infrastructure – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk According to Sophos, ransomware recovery costs soared to $2.73 million in 2024, displaying a 500% rise compared to 2023 and...
F5 Integrates API Security and Networking to Address AI Onslaught – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
OpenAI Operator Agent Used in Proof-of-Concept Phishing Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
Abu Dhabi Guidelines Offer Blueprint for Cybersecurity in Health – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
China-Backed Hackers Backdoor US Carrier-Grade Juniper MX Routers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
NIST Finalizes Differential Privacy Rules to Protect Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Apple Drops Another WebKit Zero-Day Bug – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Smashing Security podcast #408: A gag order backfires, and a snail mail ransom demand – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content What happens when a healthcare giant’s legal threats ignite a Streisand Effect wildfire… while a ransomware gang...
Man found guilty of planting infinite loop logic bomb on ex-employer’s system – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley 55-year old Davis Lu, of Houston, Texas, has been found guilty of intentionally causing damage to the computer systems of...
The AI Fix #41: Can AIs be psychopaths, and why we should be AI optimists – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 41 of the AI Fix, our hosts learn that society needs to be completely reordered...
Generative AI red teaming: Tips and techniques for putting LLMs to the test – Source: www.csoonline.com
Source: www.csoonline.com – Author: Getting started with a generative AI red team or adapting an existing one to the new technology is a complex process that...
Hiring privacy experts is tough — here’s why – Source: www.csoonline.com
Source: www.csoonline.com – Author: Unrealistic expectations by hiring managers paired with budget constraints are some of the impediments to hiring experts in privacy, on top of...
6 wichtige Punkte für Ihren Incident Response Plan – Source: www.csoonline.com
Source: www.csoonline.com – Author: Nach einem Cybervorfall müssen CISOs die richtigen Strategien, Rollen und Prozesse zur Hand haben. Diese Tipps können helfen. Lesen Sie, welche Schritte...
Aptori Now on Google Cloud Marketplace for AI-Powered Security and Automated Risk Remediation – Source: www.csoonline.com
Source: www.csoonline.com – Author: Aptori’s AI-Driven AppSec Platform Proactively Eliminates Vulnerabilities to Minimize Risk and Ensure Compliance. Aptori, a leader in AI-driven application security, today announced...
Trump nominates cyber vet Sean Plankey for CISA chief amid DOGE cuts and firings – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 12 Mar 20255 mins Government ITSecurityThreat and Vulnerability Management The cybersecurity veteran’s extensive leadership chops might spare the US federal cybersecurity...
SAP patches severe vulnerabilities in NetWeaver and Commerce apps – Source: www.csoonline.com
Source: www.csoonline.com – Author: The enterprise software vendor bundled 25 security patches into its March update, addressing flaws that impact middleware, interfaces, custom apps, and more....