Source: www.securityweek.com – Author: Ryan Naraine Security researchers this week raised an alarm after finding hidden remote access tunnel service pre-installed on the Unitree Go1 robot...
Year: 2025
Hackers Looking for Vulnerable Palo Alto Networks GlobalProtect Portals – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat actors are probing the internet for vulnerable Palo Alto Networks GlobalProtect secure remote access instances, likely in preparation for...
Security Operations Firm ReliaQuest Raises $500M at $3.4B Valuation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Security operations solutions provider ReliaQuest on Monday announced raising $500 million in a new growth funding round that brings the...
Ransomware Group Takes Credit for National Presto Industries Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The InterLock ransomware group over the weekend claimed responsibility for a disruptive cyberattack on National Presto Industries that occurred on...
Critical Vulnerability Found in Canon Printer Drivers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Microsoft’s offensive security team has warned Canon about a critical vulnerability affecting some printer drivers. According to an advisory published...
CrushFTP Blames Security Firms for Fast Exploitation of Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The Shadowserver Foundation on Monday said it started seeing exploitation attempts aimed at a recently patched CrushFTP vulnerability. The developers...
Check Point Responds to Hacking Claims – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Israeli cybersecurity firm Check Point has issued a response after a hacker claimed to have stolen valuable information from the...
Beyond the PCI DSS v4.0 Deadline: Feroot Ensures Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: mykola myroniuk In this article The compliance deadline (March 31, 2025) for PCI DSS v4.0.1 is over. This date was a big...
Can You Confidently Handle NHI Threats? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why do breaches persist despite the increased attention and budget allocated to cybersecurity? I have noticed a recurring issue –...
Driving Innovation with Robust NHIDR Strategies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Incorporating Robust NHIDR Strategies into Your Cybersecurity Approach? This evolutionary process, has spurred an exponential increase in cybersecurity...
Scaling Your Identity Management Securely – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Can Your Cybersecurity Keep Pace with Growth? When organizations scale, it’s not just revenues and team sizes that grow. The...
BSidesLV24 – Keynotes – Day One: “Secure AI” Is 20 Years Old – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – Keynotes – Day One: “Secure AI” Is 20 Years Old Authors/Presenters: Sven...
When AI Fights Back: Simbian’s 2025 Hackathon Challenges Humans to Outsmart the Machines – Source: securityboulevard.com
Source: securityboulevard.com – Author: John D. Boyle In the 1988 cult classic They Live, protagonist John Nada discovers that, with the aid of special sunglasses, he...
AI and the Future of Cybersecurity: Opportunities and Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Assura Team Although once just a staple of science fiction, AI-powered tools are now a pillar of modern security compliance management services....
The Votiro BrewFilter: Zero Trust Filtration for Your Next Mug – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro It’s Not Just Your Files That Deserve Enterprise-grade Filtration Cybersecurity experts have long warned of suspicious attachments, shadow IT, and insider...
Safeguarding Student and Faculty Data: Cybersecurity in Higher Education – Source: securityboulevard.com
Source: securityboulevard.com – Author: Assura Team Higher education institutions store vast amounts of sensitive information, including student and personnel records, financial details, and proprietary faculty research....
The Baby Rattlesnake of Cyberattacks: Why Layer 7 DDoS Can Be More Dangerous Than Larger Threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andrew Hendry When most people think of a Distributed Denial of Service (DDoS) attack, they imagine massive floods of traffic—millions of packets...
Malaysian Airport’s Cyber Disruption a Warning for Asia – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Google Brings End-to-End Encryption to Gmail – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Surge in Scans on PAN GlobalProtect VPNs Hints at Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
As CISA Downsizes, Where Can Enterprises Get Support? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
Japan Bolsters Cybersecurity Safeguards With Cyber Defense Bill – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Check Point Disputes Hacker’s Breach Claims – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Google ‘ImageRunner’ Bug Enabled Privilege Escalation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
FDA’s Critical Role in Keeping Medical Devices Secure – Source: www.darkreading.com
Source: www.darkreading.com – Author: Morey J. Haber Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
Lazarus APT Jumps on ClickFix Bandwagon in Recent Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
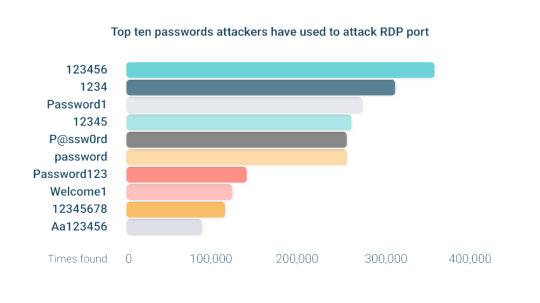
Top 10 Most-Used RDP Passwords Are Not Complex Enough – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Trend Micro Open Sources AI Tool Cybertron – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
The AI Fix #44: AI-generated malware, and a stunning AI breakthrough – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley In episode 44 of The AI Fix, ChatGPT won’t build a crystal meth lab, GPT-4o improves the show’s podcast art,...
Hackers exploit little-known WordPress MU-plugins feature to hide malware – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A new security issue is putting WordPress-powered websites at risk. Hackers are abusing the “Must-Use” plugins (MU-plugins) feature to hide...