Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Year: 2025
Ivanti EPMM Zero-Day Flaws Exploited in Chained Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Exploring Gender Bias Across Science Classrooms in India
Asambhava Shubha shares how conducting “draw a scientist” experiments in numerous classrooms inspired a documentary project on girls in STEM. Source Views: 0
Military and Veterans Affinity Group: Advocacy
As part of the Military and Veterans AG’s spotlight month, AG co-lead Helen Mills discusses how to be an ally and advocate for the military and...
What Is Generative AI (GenAI)? – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk Gartner’s Top Cybersecurity Trends of 2025 report emphasizes the growing influence of generative AI (GenAI), highlighting new opportunities for organizations...
Google’s Advanced Protection Now on Android – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Steve67 • May 14, 2025 7:35 AM They are adopting features that already exist in GrapheneOS, such as...
Smashing Security podcast #417: Hello, Pervert! – Sextortion scams and Discord disasters – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content Don’t get duped, doxxed, or drained! In this episode of “Smashing Security” we dive into the creepy...
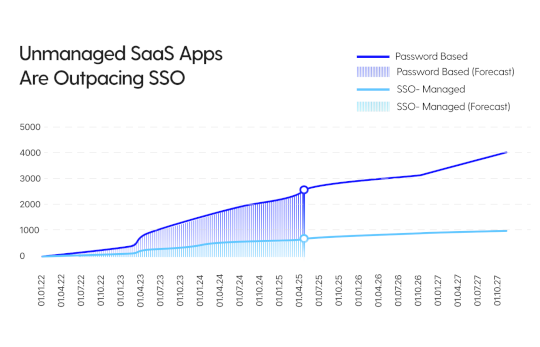
5 Identity Security Risks We Found in a Regulated Enterprise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog Even the most mature enterprises encounter new, subtle, and complex identity security challenges from the rapid growth of SaaS....
Stay Relaxed with Efficient Non-Human Identity Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Are You Safe With Your Current Non-Human Identity Security? The migration of services to the cloud promises flexibility, scalability, and...
Continuous Improvement in NHIs Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Can Continuous Improvement in NHIs Management Be the Key to Securing Your Operations? You’re no stranger to the importance of...
Building Trust Through Secure NHIs Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Can We Cultivate Trust with Secure NHIs Practices? When we navigate in increased digital interconnection, establishing trust in cybersecurity...
Cultivate Independent Secrets Management Protocols – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why is Independent Secrets Management Crucial for Cybersecurity? How crucial do you believe independent secrets management is to your organization’s...
Implementing a SCIM API for Your Application: A Comprehensive Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Devesh Patel Introduction: Why Your App Needs SCIM Yesterday Picture this: Your B2B SaaS product has finally landed that enterprise client you’ve...
BSidesLV24 – GroundFloor – A Quick Story Of Security Pitfalls With Exec Commands In Software Integrations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – GroundFloor – A Quick Story Of Security Pitfalls With Exec Commands In...
SSOJet LLM-Friendly Documentation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ankit Agarwal Make SSOJet’s API documentation accessible and easy to understand for large language models like ChatGPT, Claude, GitHub Copilot, Cursor, and...
Hacking the Hardware Brains of Computers is the Ultimate Cyberattack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist Compromising the hardware layer, especially the CPU, is the Holy Grail of cyberattacks. Recent work by Christiaan Beek, a leading...
Randall Munroe’s XKCD ‘Deposition’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, May 15, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Patch Tuesday, May 2025 Edition – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Microsoft on Tuesday released software updates to fix at least 70 vulnerabilities in Windows and related products, including five zero-day flaws...
Marks & Spencer Confirms Customer Data Stolen in Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Congress Should Tackle Cyber Threats, Not Competition – Source: www.darkreading.com
Source: www.darkreading.com – Author: Greg Guice Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Orca Security Gets AI-Powered Remediation From Opus Deal – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Hacktivists Make Little Impact During India-Pakistan Conflict – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
News alert: INE Security highlights monthly CVE Labs aimed at sharpening real-world defense – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Cary, NC, May 14, 2025, CyberNewswire — INE Security, a global leader in hands-on cybersecurity training and certifications, today highlighted how...
News Alert: INE Security outlines top 5 training priorities emerging from RSAC 2025 – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Cary, NC, May 13, 2025, CyberNewswire –Fresh from a high-impact presence at RSAC 2025, where INE Security welcomed thousands of visitors...
Ivanti Patches Two EPMM Zero-Days Exploited to Hack Customers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Ivanti on Tuesday announced patches for three vulnerabilities in its products, including two Endpoint Manager Mobile (EPMM) bugs that have...
Sharing Intelligence Beyond CTI Teams, Across Wider Functions and Departments – Source: www.securityweek.com
Source: www.securityweek.com – Author: Marc Solomon I read a recent Google Intelligence Report which highlighted a case uncovered last year involving a single North Korean worker...
SAP Patches Another Exploited NetWeaver Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Enterprise software maker SAP on Tuesday released 16 new and two updated security notes as part of its May 2025...
Court Rules Against NSO Group – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • May 13, 2025 10:03 AM With regards, “I’m sure it’ll be appealed. Everything always is.”...
The AI Fix #50: AI brings dead man back for killer’s trial, and the judge loves it – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 50 of The AI Fix, AI brings a slain man back from the dead so...
Two years’ jail for down-on-his-luck man who sold ransomware online – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley What do you do if you’re down on your luck? Maybe you struggled at school through no fault of your...