Source: www.cyberdefensemagazine.com – Author: News team Competition in the eCommerce industry is becoming increasingly rivalled. As consumers turn to online stores, more and more retailers are...
Day: August 7, 2025
Researcher Deploys Fuzzer to Test Autonomous Vehicle Safety – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Critical Zero-Day Bugs Crack Open CyberArk, HashiCorp Password Vaults – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
‘ReVault’ Security Flaws Impact Millions of Dell Laptops – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
VexTrio Cybercrime Outfit Run by Legit Ad Tech Firms – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Google Gemini AI Bot Hijacks Smart Homes, Turns Off the Lights – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
SentinelOne Acquires AI Startup Prompt Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Microsoft unveils Project Ire: AI that autonomously detects malware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft’s Project Ire uses AI to autonomously reverse engineer and classify software as malicious or benign. Microsoft announced Project Ire,...
CERT-UA warns of UAC-0099 phishing attacks targeting Ukraine’s defense sector – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ukraine’s CERT-UA warns of phishing attacks by UAC-0099 targeting defense sectors, using malware like MATCHBOIL, MATCHWOK, and DRAGSTARE. Ukraine’s CERT-UA...
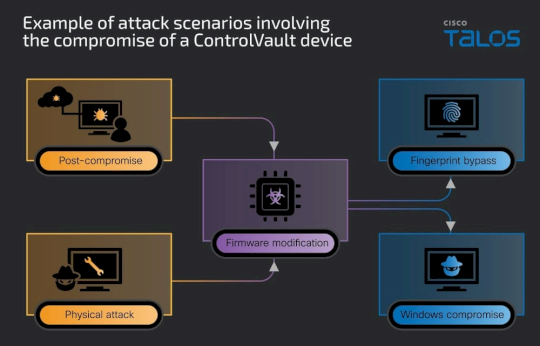
Over 100 Dell models exposed to critical ControlVault3 firmware bugs – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini ReVault flaws in Dell ControlVault3 firmware allow firmware implants and Windows login bypass on 100+ laptop models via physical access....
How CTEM Boosts Visibility and Shrinks Attack Surfaces in Hybrid and Cloud Environments – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CTEM is a continuous strategy that assesses risk from an attacker’s view, helping orgs prioritize threats across cloud and hybrid...
WhatsApp cracks down on 6.8M scam accounts in global takedown – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini WhatsApp removed 6.8M accounts linked to global scam centers, mainly in Cambodia, in a crackdown with Meta and OpenAI. Meta...
Trend Micro fixes two actively exploited Apex One RCE flaws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Trend Micro patched two critical Apex One flaws (CVE-2025-54948, CVE-2025-54987) exploited in the wild, allowing RCE via console injection. Trend...
Webinar: How to Stop Python Supply Chain Attacks—and the Expert Tools You Need – Source:thehackernews.com
Source: thehackernews.com – Author: . Python is everywhere in modern software. From machine learning models to production microservices, chances are your code—and your business—depends on Python...
UAC-0099 Attack Detection: Hackers Target Government and Defense Agencies in Ukraine Using MATCHBOIL, MATCHWOK, and DRAGSTARE Malware – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko The UAC-0099 hacking collective, active in cyber-espionage campaigns against Ukraine since mid-2022, has reemerged in the cyber threat arena. The...
Has Cyber Been Infected With the Economic Malaise? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alan Shimel From the floor at #BlackHat2025: Cybersecurity has the blinking lights, but this year it also has blood in the water,...
News alert: SpyCloud’s AI-powered platform mimics veteran analysts, speeds threat detection – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Austin, TX, Aug. 6, 2025, CyberNewswire: SpyCloud, the leader in identity threat protection, today announced a significant enhancement to its SaaS...
Project Red Hook: Chinese Gift Card Fraud at Scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gary Warner Project Red Hook is a Homeland Security Investigations operation examining how Chinese Organized Crime is committing wholesale Gift Card Fraud...
Palo Alto Networks Previews ASPM Module for Cortex Cloud Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Palo Alto Networks this week revealed it is providing early access to an application security posture management (ASPM) module for...
Contrast Security Adds GitHub Copilot and Sumo Logic Integrations to ADR Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard This week at the Black Hat USA 2025 conference, Contrast Security added integrations with GitHub Copilot and the security information and...
Who Got Arrested in the Raid on the XSS Crime Forum? – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs On July 22, 2025, the European police agency Europol said a long-running investigation led by the French Police resulted in the...
Beef up AI security with zero trust principles – Source: www.csoonline.com
Source: www.csoonline.com – Author: Guardrails just aren’t enough to lower risk for today’s AI systems, Black Hat attendees told. Many CSOs worry about their firm’s AI...
IT-Security-Jobs – 5 bittere Wahrheiten – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine Karriere im Bereich Cybersecurity verspricht ein hohes Gehalt und einen relativ sicheren Job. Allerdings zieht sie auch eine enorme Arbeitsbelastung nach...
Durch Datenlecks verursachte Kosten sind gefallen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Ein aktueller IBM-Report zeigt: Nicht zuletzt dank schnellerer Erkennung durch KI-Systeme können die Kosten für Cyberattacken gedrückt werden. Durch KI unterstützte Angriffe...
Researchers uncover RCE attack chains in popular enterprise credential vaults – Source: www.csoonline.com
Source: www.csoonline.com – Author: Open-source credential management systems HashiCorp Vault and CyberArk Conjur had flaws enabled remote code execution among other attacks. Researchers have found 14...
ReVault flaws let attackers bypass Windows login or place malware implants on Dell laptops – Source: www.csoonline.com
Source: www.csoonline.com – Author: Update now: ControlVault3 firmware vulnerabilities undermine secure enclave technology. Flaws in the firmware that ships with more than 100 models of Dell...
SpyCloud Enhances Investigations Solution with AI-Powered Insights – Revolutionizing Insider Threat and Cybercrime Analysis – Source: www.csoonline.com
Source: www.csoonline.com – Author: SpyCloud Investigations, now with AI Insights, empowers security teams to act decisively with finished intelligence built from billions of breach, malware, and...
Akira affiliates abuse legitimate Windows drivers to evade detection in SonicWall attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Aug 6, 20254 mins RansomwareSecurityWindows Security Researchers warn of kernel-level evasion and possible zero-day exploitation as ransomware activity surges. Threat researchers...
How cybersecurity leaders are securing AI infrastructures – Source: www.csoonline.com
Source: www.csoonline.com – Author: AI models, agentic frameworks, data pipelines, and all the tools, services, and open-source libraries that make AI possible are evolving quickly and...
Chinese Groups Stole 115 Million US Cards in 16-Month Smishing Campaign – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. A new report from cybersecurity firm SecAlliance has revealed a highly organized criminal operation run by Chinese syndicates that may...