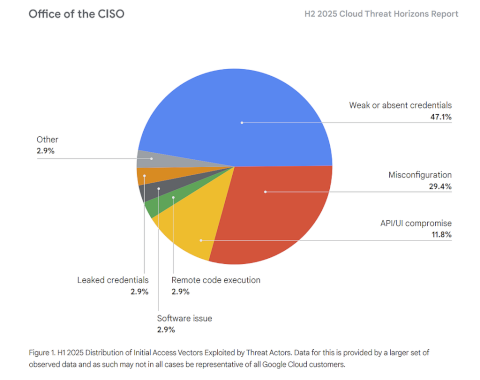
Source: securityboulevard.com – Author: Anton Chuvakin This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our next Threat...
Month: July 2025
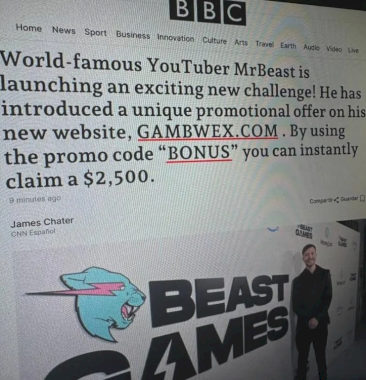
Scammers Unleash Flood of Slick Online Gaming Sites – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Fraudsters are flooding Discord and other social media platforms with ads for hundreds of polished online gaming and wagering websites that...
Senate Committee Advances Trump Nominee to Lead CISA – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A U.S. Senate committee voted Wednesday to advance President Donald Trump’s pick to lead the agency that secures the nation’s...
Cost of Data Breach in US Rises to $10.22 Million, Says Latest IBM Report – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend IBM’s Cost of a Breach Report shows that global costs are down, but US costs are up. More than anything...
Koreans Hacked, Blackmailed by 250+ Fake Mobile Apps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Silk Typhoon Linked to Powerful Offensive Tools, PRC-Backed Companies – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
The CrowdStrike Outage Was Bad, but It Could Have Been Worse – Source: www.darkreading.com
Source: www.darkreading.com – Author: Roger Cressey Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
ChatGPT, GenAI Tools Open to ‘Man in the Prompt’ Browser Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
African Orgs Fall to Mass Microsoft SharePoint Exploits – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Hidden Backdoor Found in ATM Network via Raspberry Pi – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A covert attack targeting ATM infrastructure has been observed using a hidden Raspberry Pi device to breach internal bank systems. The intrusion...
Google to Publicly Report New Vulnerabilities Within One Week of Vendor Disclosure – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Google is set to begin publicly reporting vulnerability discoveries within one week of informing the impacted vendor. The trial policy, named Reporting...
Third of Exploited Vulnerabilities Weaponized Within a Day of Disclosure – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Written by Threat actors are becoming faster at exploiting vulnerabilities and rely more than ever on zero-day exploitation. According to VulnCheck’s latest...
Measuring the Attack/Defense Balance – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier “Who’s winning on the internet, the attackers or the defenders?” I’m asked this all the time, and I can only...
Aeroflot Hacked – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • July 29, 2025 12:44 PM Hmm, I would have said that it should have been...
32% of exploited vulnerabilities are now zero-days or 1-days – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Jul 30, 20255 mins Patch Management SoftwareThreat and Vulnerability ManagementZero-Day Vulnerabilities Recent research into KEVs and CVEs shows that threat actors...
Palo Alto kauft CyberArk – Source: www.csoonline.com
Source: www.csoonline.com – Author: News-Analyse 30. Juli 20254 Minuten Mergers and AcquisitionsTechnologie-Industrie Palo Alto Networks greift richtig tief in die Tasche, um einen Fuß in die...
Game changer: How AI simplifies implementation of Zero Trust security objectives – Source: www.csoonline.com
Source: www.csoonline.com – Author: AI can transform Zero Trust security implementation and management from a complex manual and multi-year task into a highly-automated, rapidly-deployable solution for...
Palo Alto Networks to buy CyberArk for $25B as identity security takes center stage – Source: www.csoonline.com
Source: www.csoonline.com – Author: Updated News Jul 30, 20255 mins Identity Management SolutionsMergers and AcquisitionsSecurity The cybersecurity giant is finally ready to tackle the identity management...
Erneuter Hackerangriff bei Orange – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 30. Juli 20252 Minuten HackingTelekommunikationsindustrie Die Attacke erinnert an frühere Angriffe, die mutmaßlich von Salt Typhoon verübt wurden. Nachdem bereits im...
Dobrindt prüft Einsatz von US-Software Palantir – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Analyse-Software des Unternehmens Palantir ist umstritten, einige Bundesländer nutzen sie. Ob sie auch bundesweit zum Einsatz kommt, ist noch nicht entschieden....
Ransomware upstart Gunra goes cross-platform with encryption upgrades – Source: www.csoonline.com
Source: www.csoonline.com – Author: The Linux variant signals Gunra’s move to cross-platform attacks with new multi-threaded and partial encryption features. A new Linux variant of the...
Prepping for the quantum threat requires a phased approach to crypto agility – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis Jul 30, 20257 mins Data and Information SecurityEncryption Banking sector security leaders shed light on what it takes for CISOs...
How CISOs can scale down without compromising security – Source: www.csoonline.com
Source: www.csoonline.com – Author: When budget cuts hit, CISOs face tough choices. But clear priorities, transparency, and a focus on people and processes can help them...
MCP‑Sicherheit: Das Rückgrat von Agentic AI sichern – Source: www.csoonline.com
Source: www.csoonline.com – Author: MCP macht Agentic AI flexibel – aber auch angreifbar. Für CISOs gilt: Sichtbarkeit, Kontrolle und sichere Workflows sind entscheidend für Vertrauen und...
Cobalt Strike Beacon delivered via GitHub and social media – Source: securelist.com
Source: securelist.com – Author: Maxim Starodubov, Valery Akulenko, Danila Semenov Introduction In the latter half of 2024, the Russian IT industry, alongside a number of entities...
SWE’s Global Ambassador Program Receives 2025 Power of Associations Gold Award
ASAE: The Center for Association Leadership recognizes the impact and reach of SWE’s globally inclusive leadership program. Source Views: 3
Nimble ‘Gunra’ Ransomware Evolves With Linux Variant – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Critical Flaw in Vibe-Coding Platform Base44 Exposes Apps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
The Hidden Threat of Rogue Access – Source: www.darkreading.com
Source: www.darkreading.com – Author: Durgaprasad Balakrishnan Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
The AI Fix #61: Replit panics, deletes $1M project; AI gets gold at Math Olympiad – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 61 of The AI Fix, a robot called DeREK goes bananas, OpenAI, Google DeepMind, and...