Source: www.securityweek.com – Author: Eduard Kovacs More than forty cybersecurity merger and acquisition (M&A) deals were announced in June 2025. An analysis conducted by SecurityWeek shows...
Month: July 2025
Undetectable Android Spyware Backfires, Leaks 62,000 User Logins – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A vulnerability in Catwatchful, an Android spyware posing as parental control software, exposed the credentials of over 62,000 customer accounts,...
North Korean Hackers Use Fake Zoom Updates to Install macOS Malware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire North Korean hackers are luring employees at web3 and crypto-related organizations into installing Nim-compiled macOS malware via fake Zoom software...
Technical difficulties or cyber attack? Ingram Micro’s website goes down just in time for the holiday weekend – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content There’s no official word on what the problem is, but Ingram Micro’s website has been down since...
Catwatchful stalkerware app spills secrets of 62,000 users – including its own admin – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content Another scummy stalkerware app has spilled its guts, revealing the details of its 62,000 users – and...
Hunters International ransomware group shuts down – but will it regroup under a new guise? – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The notorious Hunters International ransomware-as-a-service operation has announced that it has shut down, in a message posted on its dark...
The 47-Day SSL Certificate Era: What It Means for Site Owners and IT Teams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grant Shapiro The move to 47-day SSL certificates is a major step toward a more secure, automated internet. While it introduces new...
Yet More Stalkerware Leaks Secret Data: ‘Catwatchful’ is Latest Nasty App – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Content warning: Domestic abuse, stalking, controlling behavior, Schadenfreude, irony. The post Yet More Stalkerware Leaks Secret Data: ‘Catwatchful’ is Latest...
Validation is an Increasingly Critical Element of Cloud Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Kellerman Cloud security isn’t just about having the right solutions in place — it’s about determining whether they are functioning correctly....
Mastering Real-Time Cloud Data Governance Amid Evolving Threats and Regulations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Karthik Reddy Real-time data governance provides security and privacy teams with immediate visibility into what is happening, allowing them to stop a...
The Role Culture and Trust Play in Countering Deepfakes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Perry Carpenter Empowering employees with critical thinking and transparency to combat synthetic media impersonations and fortify organizational defenses. The post The Role...
Like Ransoming a Bike: Organizational Muscle Memory Drives the Most Effective Response – Source: www.securityweek.com
Source: www.securityweek.com – Author: Trevin Edgeworth Ransomware has become an enterprise boogeyman experiencing 37 percent increase over 2024 according to the Verizon Data Breach Investigations Report...
Kelly Benefits Data Breach Impacts 550,000 People – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Benefits and payroll solutions firm Kelly & Associates Insurance Group (dba Kelly Benefits) has informed authorities that a recent data...
Verified, but vulnerable: Malicious extensions exploit IDE trust badges – Source: www.csoonline.com
Source: www.csoonline.com – Author: Microsoft and other vendors downplay the threat, but OX Security warns the exploit is still active. Developers across popular integrated development environments...
Kritische Schwachstelle in Cisco Unified CM entdeckt – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine schwerwiegende Sicherheitslücke in der Kommunikationssoftware Cisco Unified CM sowie in der SME ermöglicht Root-Zugriffe durch Angreifer. Bereits zum zweiten Mal in...
Dobrindt will mehr in Cybersicherheit investieren – Source: www.csoonline.com
Source: www.csoonline.com – Author: Cyberangriffe auf Unternehmen und Verwaltungen haben zugenommen. Der Schutz vor solchen Attacken sei genauso wichtig wie der militärische Schutz, sagt der Minister....
CVE-2025-5777 Detection: A New Critical Vulnerability Dubbed “CitrixBleed 2” in NetScaler ADC Faces Exploitation Risk – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Shortly after the disclosure of two Sudo-related local privilege escalation vulnerabilities affecting major Linux distributions, attention has shifted to a...
Friday Squid Blogging: How Squid Skin Distorts Light – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
New Cyber Blueprint Aims to Guide Organizations on AI Journey – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Dark Web Vendors Shift to Third Parties, Supply Chains – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
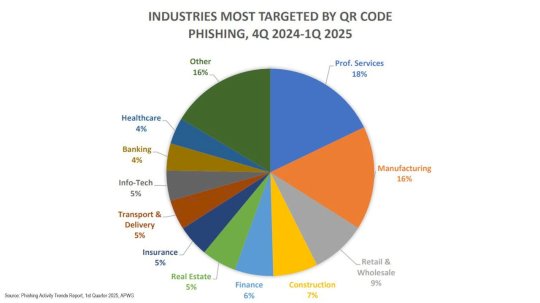
Criminals Sending QR Codes in Phishing, Malware Campaigns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
IDE Extensions Pose Hidden Risks to Software Supply Chain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Attackers Impersonate Top Brands in Callback Phishing – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Browser Extensions Pose Heightened, but Manageable, Security Risks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
AI Tackles Binary Code Challenges to Fortify Supply Chain Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Big Tech’s Mixed Response to U.S. Treasury Sanctions – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs In May 2025, the U.S. government sanctioned a Chinese national for operating a cloud provider linked to the majority of virtual...
Cybersecurity in the supply chain: strategies for managing fourth-party risks – Source: www.csoonline.com
Source: www.csoonline.com – Author: Third-party vendors are a well-known risk but they are often not the last point in the supply chain and cybersecurity leaders need...
Hunters International shuts ransomware operations, reportedly becomes an extortion-only gang – Source: www.csoonline.com
Source: www.csoonline.com – Author: As a parting gift, the gang is offering free decryption keys to victim firms. Ransomware gang Hunters International says it’s shutting down...
Hardcoded root credentials in Cisco Unified CM trigger max-severity alert – Source: www.csoonline.com
Source: www.csoonline.com – Author: Static root credentials left in limited Unified Communications Manager builds could let attackers gain full control over enterprise communications systems. Cisco (Nasdaq:CSCO)...
Erneute Cyberattacke auf Internationalen Strafgerichtshof – Source: www.csoonline.com
Source: www.csoonline.com – Author: Der kürzlich erfolgte Cyberangriff auf den Internationalen Strafgerichtshof zeigt die anhaltenden Bedrohungen für globale Justizsysteme auf. Der Internationale Strafgerichtshof wurde bereists zum...