Source: socprime.com – Author: Veronika Telychko Shortly after the disclosure of two Sudo-related local privilege escalation vulnerabilities affecting major Linux distributions, attention has shifted to a...
Day: July 4, 2025
Friday Squid Blogging: How Squid Skin Distorts Light – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
New Cyber Blueprint Aims to Guide Organizations on AI Journey – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Dark Web Vendors Shift to Third Parties, Supply Chains – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
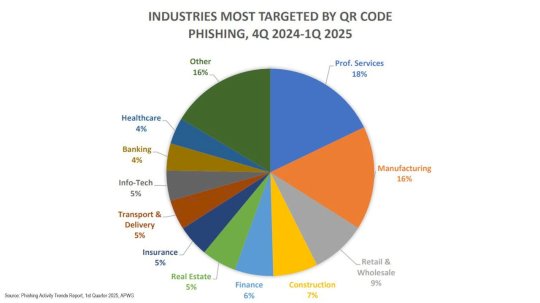
Criminals Sending QR Codes in Phishing, Malware Campaigns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
IDE Extensions Pose Hidden Risks to Software Supply Chain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Attackers Impersonate Top Brands in Callback Phishing – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Browser Extensions Pose Heightened, but Manageable, Security Risks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
AI Tackles Binary Code Challenges to Fortify Supply Chain Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Big Tech’s Mixed Response to U.S. Treasury Sanctions – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs In May 2025, the U.S. government sanctioned a Chinese national for operating a cloud provider linked to the majority of virtual...
Cybersecurity in the supply chain: strategies for managing fourth-party risks – Source: www.csoonline.com
Source: www.csoonline.com – Author: Third-party vendors are a well-known risk but they are often not the last point in the supply chain and cybersecurity leaders need...
Hunters International shuts ransomware operations, reportedly becomes an extortion-only gang – Source: www.csoonline.com
Source: www.csoonline.com – Author: As a parting gift, the gang is offering free decryption keys to victim firms. Ransomware gang Hunters International says it’s shutting down...
Hardcoded root credentials in Cisco Unified CM trigger max-severity alert – Source: www.csoonline.com
Source: www.csoonline.com – Author: Static root credentials left in limited Unified Communications Manager builds could let attackers gain full control over enterprise communications systems. Cisco (Nasdaq:CSCO)...
Erneute Cyberattacke auf Internationalen Strafgerichtshof – Source: www.csoonline.com
Source: www.csoonline.com – Author: Der kürzlich erfolgte Cyberangriff auf den Internationalen Strafgerichtshof zeigt die anhaltenden Bedrohungen für globale Justizsysteme auf. Der Internationale Strafgerichtshof wurde bereists zum...
US Calls Reported Threats by Pro-Iran Hackers to Release Trump-Tied Material a ‘Smear Campaign’ – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Pro-Iran hackers have threatened to release emails supposedly stolen from people connected to President Donald Trump, according to a news...
Security Pros Say Hunters International RaaS Operators are ‘Changing Jerseys’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The notorious Hunters International RaaS group that racked up hundreds of victims over two years says it’s shutting down and...
Analysis Surfaces Increased Usage of LLMs to Craft BEC Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A Barracuda Networks analysis of unsolicited and malicious emails sent between February 2022 to April 2025 indicates 14% of the...
Beyond Silos: The Power of Internal Collaboration on Transforming Fraud Prevention – Source: securityboulevard.com
Source: securityboulevard.com – Author: André Ferraz By breaking down internal silos, leveraging advanced technology and embracing industrywide cooperation, organizations can shift from reactive to proactive fraud...
We Are Losing the Scan/Patch Battle – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bob Tinker There is no question that vulnerability scanning and patch management remain necessary, but they are clearly no longer sufficient The...
The Differences and Similarities Between Shadow IT and BYOC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Morey Haber Understanding the difference between Shadow IT and BYOC, although subtle, requires different policies, procedures and technology to resolve. The post...