Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Day: June 27, 2025
‘CitrixBleed 2’ Shows Signs of Active Exploitation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Scattered Spider Taps CFO Credentials in ‘Scorched Earth’ Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Hackers Make Hay? Smart Tractors Vulnerable to Full Takeover – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Vulnerability Debt: How Do You Put a Price on What to Fix? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Matt Middleton-Leal Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
US Falling Behind China in Exploit Production – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
CVE-2025-20281 and CVE-2025-20282 Vulnerabilities: Critical RCE Flaws in Cisco ISE and ISE-PIC Enable Root Access – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko WRITTEN BY Veronika Telychko Technical Writer [post-views] June 27, 2025 · 4 min read As the summer heat intensifies, so does...
Some Brother printers have a remote code execution vulnerability, and they can’t fix it – Source: www.csoonline.com
Source: www.csoonline.com – Author: An authentication bypass vulnerability in the printers, hardcoded at the factory, can be chained with another flaw for remote code execution on...
Microsoft-Lücke ermöglicht E-Mail-Versand ohne Authentifizierung – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine Sicherheitslücke in Microsoft 365 Direct Send erlaubt es Cyberkriminellen, Mitarbeiter ohne gestohlene Anmeldedaten anzugreifen. Drucker und Scanner werden dank einer Schwachstelle...
The rise of the compliance super soldier: A new human-AI paradigm in GRC – Source: www.csoonline.com
Source: www.csoonline.com – Author: AI is reshaping GRC, demanding a new kind of archetype — forward-operating professionals who don’t just manage governance; they engineer it. As...
6 key trends redefining the XDR market – Source: www.csoonline.com
Source: www.csoonline.com – Author: X marks the spot: Extended detection and response (XDR) continues to evolve, with XDR-as-a-service on the rise, AI developments reshaping what’s possible,...
Don’t trust that email: It could be from a hacker using your printer to scam you – Source: www.csoonline.com
Source: www.csoonline.com – Author: New research reveals a simple way threat actors are using Microsoft 365 Direct Send to phish employees, without even having to steal...
Cisco warns of critical API vulnerabilities in ISE and ISE-PIC – Source: www.csoonline.com
Source: www.csoonline.com – Author: Patch these holes before threat actors exploit them to get root access. CSOs are being urged to quickly patch multiple vulnerabilities in...
SafePay ransomware: What you need to know – Source: www.fortra.com
Source: www.fortra.com – Author: Graham Cluley What is the SafePay ransomware? SafePay is a relatively new ransomware threat that was first observed around September 2024. Like...
Hawaiian Airlines Hit by Cybersecurity Incident – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Hawaiian Airlines has been hit by a cybersecurity incident, impacting some of its IT systems. The US airline disclosed the “cybersecurity event”...
CitrixBleed 2 Vulnerability Exploited, Recalling Earlier CitrixBleed Fallout – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new critical vulnerability in Citrix NetScaler ADC and Gateway devices, bearing similarities to the notorious CitrixBleed flaw of 2023, is reportedly...
MOVEit Transfer Systems Face Fresh Attack Risk Following Scanning Activity Surge – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A significant rise in scanning activity targeting MOVEit Transfer systems has been detected, indicating the software could face a resurgence in attacks....
Microsoft to Preview New Windows Endpoint Security Platform After CrowdStrike Outage – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Microsoft on Thursday shared an update on the progress of its resiliency initiative, triggered by the highly disruptive CrowdStrike incident...
How I Built My STEM Career Without a Network
What happens when you don’t have referrals or connections? Akanksha Prasad, a senior chemical engineering scientist, shares how to build your own way forward and develop...
LGBTQ+ Students and Professionals Need Community Now More Than Ever
As sweeping anti-DEI legislation threatens progress worldwide, LGBTQ+ people in STEM face growing risks and fewer resources. Here’s how the STEM community can step up. Source...
‘Cyber Fattah’ Hacktivist Group Leaks Saudi Games Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
‘IntelBroker’ Suspect Arrested, Charged in High-Profile Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
How Geopolitical Tensions Are Shaping Cyber Warfare – Source: www.darkreading.com
Source: www.darkreading.com – Author: Andrew Costis Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Best SAST Solutions: How to Choose Between the Top 11 Tools in 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mend.io Team Best SAST Solutions: How to Choose Between the Top 11 Tools in 2025 Static Application Security Testing (SAST) is a...
AI vs. AI: How Deepfake Attacks Are Changing Authentication Forever – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dev Kumar Imagine receiving a video call from your company’s CEO asking you to immediately transfer $25 million to a specific bank...
Active Scanning vs. Passive Scanning: Key Differences – Source: securityboulevard.com
Source: securityboulevard.com – Author: FireMon Enterprise security teams are stretched thin, and the attack surface keeps growing. The harsh truth? If you’re not scanning for vulnerabilities,...
Building Trust in Your NHI Security Measures – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Reliable are Your Non-Human Identity Security Measures? Have you ever questioned the trustworthiness of your Non-Human Identity (NHI) security...
Is Your Secrets Management Getting Better? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Are Your Cybersecurity Strategies Evolving Effectively? The question arises: Is your secrets management improving? These days, robust secrets management isn’t...
Effective NHI Management that Fits Your Budget – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why is Budget-Friendly NHI Management Crucial for Business Success? Effective cybersecurity is no longer a luxury but a necessity for...
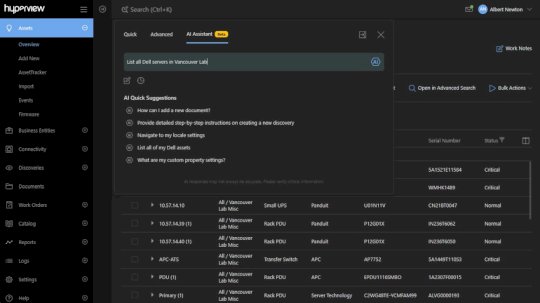
AI Assistant – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi Product Update: Version 5.0 We’ve rolled out our biggest update yet, and it’s packed with lots of great stuff that...