🎯 ¡CISOs, preparemos el café (y el presupuesto)! Llega el “Firewall de IA” Hola, comunidad CISO! 🚀 ¿Cómo les va navegando este mar de desafíos que...
Day: June 21, 2025
Friday Squid Blogging: Gonate Squid Video – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Surveillance in the US – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Good article from 404 Media on the cozy surveillance relationship between local Oregon police and ICE: In the email thread,...
AI in Health Care: An Interview With Dr. Xueying Zhao, SWE Member & Medical Device Engineer
Learn how Becton, Dickinson and Company (BD) is advancing health care innovation by bridging microfluids, automation, and AI. Source Views: 2
Celebrating Community and Collaboration on International Women in Engineering Day
Hear from members of SWE and SWE’s joint member organizations on how supporting each other made this year’s INWED special. Source Views: 1
The Digital Pandemic: Inside 2024’s Most Devastating Cyber Breaches – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The cybersecurity landscape of 2024 has revealed an unprecedented surge in both the frequency and sophistication of data breaches, setting...
AWS Enhances Cloud Security With Better Visibility Features – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Hackers Post Dozens of Malicious Copycat Repos to GitHub – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Telecom Giant Viasat Is Latest Salt Typhoon Victim – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
How Cyber Warfare Changes the Face of Geopolitical Conflict – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Krispy Kreme hack exposed sensitive data of over 160,000 people – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Krispy Kreme, the dispenser of delectable doughnuts, has revealed that an astonishingly wide range of personal information belonging to past...
Qilin offers “Call a lawyer” button for affiliates attempting to extort ransoms from victims who won’t pay – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley Imagine for one moment that you are a cybercriminal. You have compromised an organisation’s network, you have stolen their data,...
The $4.88 Million Question: Why Password-Based Breaches Are Getting More Expensive – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dev Kumar If you’re responsible for cybersecurity at your organization, there’s a number that should make you pause and reconsider your entire...
PCI DSS 4.0.1: What Changed and How is this the Next Step for Universal MFA – Source: securityboulevard.com
Source: securityboulevard.com – Author: Roman Kadinsky, Cofounder, President & COO, HYPR As the transition period for PCI DSS 4.0 draws to a close on March 31,...
LinuxFest Northwest: The Geology of Open Source – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenter: Hazel Weakly (Nivenly Foundation; Director, Haskell Foundation; Infrastructure Witch of Hachyderm) Our sincere appreciation to LinuxFest Northwest (Now Celebrating...
US Pig Butchering Victims ‘Will’ Get Refunds — Feds Seize $225M Cryptocurrency – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Pretty girls plus investment fraud equals forfeiture recovery (eventually). U.S. federal agencies have spent the past 18 months piecing together this complex...
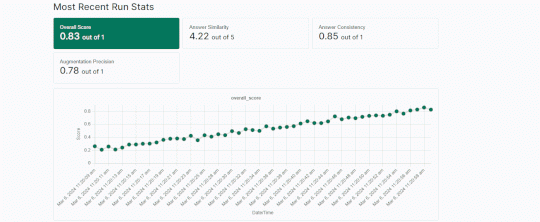
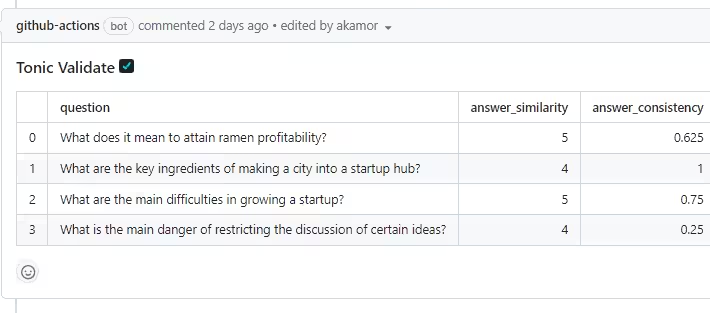
Tonic Validate is now on GitHub Marketplace! (Part 2) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog Tonic Validate is a free, open-source library for evaluating RAG and LLM based...
Tonic.ai Achieves HIPAA Compliance Certification, Ensuring Enhanced Security for Protected Health Information – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog Tonic.ai offers a developer platform for data de-identification, synthesis, and provisioning to keep...
Tonic Validate is now available on GitHub Marketplace! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog Tonic Validate is a free, open-source library for evaluating RAG and LLM based...
Steam Phishing: popular as ever – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bart A month or so ago a friend of mine received the following message on Steam from someone in their Friends list...
CVE-2025-49763 – Remote DoS via Memory Exhaustion in Apache Traffic Server via ESI Plugin – Source: securityboulevard.com
Source: securityboulevard.com – Author: Yohann Sillam Remote attackers can trigger an avalanche of internal ESI requests, exhausting memory and causing denial-of-service in Apache Traffic Server. Executive...
Top 7 Ambient Listening AI Tools Revolutionizing Healthcare in 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chetan Saxena Imagine if every doctor had an invisible assistant, one that quietly listens during every patient interaction, captures every detail with...