Source: www.securityweek.com – Author: Ionut Arghire A large-scale account takeover (ATO) campaign has been abusing the TeamFiltration penetration testing framework to target Entra ID users, Proofpoint...
Day: June 14, 2025
Friday Squid Blogging: Stubby Squid – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Stubby Squid Video of the stubby squid (Rossia pacifica) from offshore Vancouver Island. As usual, you...
New Way to Covertly Track Android Users – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Researchers have discovered a new way to covertly track Android users. Both Meta and Yandex were using it, but have...
Dutch police identify users as young as 11-year-old on Cracked.io hacking forum – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Dutch police have announced that they have identified 126 individuals linked to the now dismantled Cracked.io cybercrime forum. Cracked.io was...
CISA Reveals ‘Pattern’ of Ransomware Attacks Against SimpleHelp RMM – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
SWE Receives IACET Reaccreditation
SWE has a long-standing tradition of providing our members with effective learning programs and has been an IACET Accredited Provider since 2008. Source Views: 3
CLI and Me: A Blueprint for Bold Leadership
Ayomide Zul Kazeem shares how the SWE Collegiate Leadership Institute (CLI) equipped her to listen, communicate, and lead in STEM. Source Views: 0
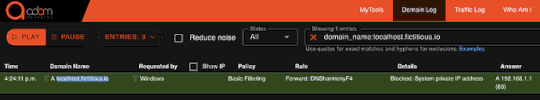
DNS Rebind Protection Revisited – Source: securityboulevard.com
Source: securityboulevard.com – Author: David After this week’s attention to META and Yandex localhost abuses, it is time to revisit a core feature/option of protective DNS...
News alert: Arsen launches AI-powered vishing simulation to help combat voice phishing at scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Paris, Jun. 3, 2025, CyberNewswire–Arsen, the cybersecurity startup known for defending organizations against social engineering threats, has announced the release of...
LinuxFest Northwest: Chaos Testing Of A Postgres Cluster On Kubernetes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenter: Nikolay Sivko (Co-Founder And CEO At Coroot) Our sincere appreciation to LinuxFest Northwest (Now Celebrating Their Organizational 25th Anniversary...
Shadow AI: Examples, Risks, and 8 Ways to Mitigate Them – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mend.io Team What is Shadow AI? Shadow AI refers to the unauthorized or unmanaged use of AI tools, models, frameworks, APIs or...
Meta AI is a ‘Privacy Disaster’ — OK Boomer – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Pundits accuse Zuckerberg’s latest app of having a “dark pattern,” tricking the over 50s into oversharing. The Meta AI app’s public...
HR’s 2025 Guide to Preventing Interview and Onboarding Fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Vy Chen A Wake-Up Call for HR in the Age of Deepfakes and Remote Work In 2025, HR leaders are facing a...
Zero-Click Flaw in Microsoft Copilot Illustrates AI Agent, RAG Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A critical vulnerability found in Microsoft’s Copilot puts a focus on the growing security risks that come with new AI...
A Guide to Managed Kubernetes-as-a-Service Shared Responsibility Model – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mary Henry Kubernetes is powerful, but managing it in-house can be a major drain on your engineering resources. That’s why many organizations...
LinuxFest Northwest: Easy Modular Sensors And Automation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenter: Sam Groveman (Research Associate) Our sincere appreciation to LinuxFest Northwest (Now Celebrating Their Organizational 25th Anniversary Of Community Excellence),...
How identity management is shifting into the agent era – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eric Olden Let’s break down how identity must evolve across the key functions to support secure, scalable AI agent architectures. Agent Authentication:...
Former CISA and NCSC Heads Warn Against Glamorizing Threat Actor Names – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Written by The former heads of the leading cybersecurity government agencies in the US and UK have called for an overhaul in...
The AI Arms Race: Deepfake Generation vs. Detection – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend If deepfakes were a disease, this would be a pandemic. Artificial Intelligence (AI) now generates deepfake voice at a scale...
Hackerangriff treibt Serviettenhersteller Fasana in die Insolvenz – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Papierserviettenfabrik Fasana leidet unter den schweren Folgen eines Cyberangriffs. Das Unternehmen hat nun einen Insolvenzantrag gestellt. Die Serviettenfabrik Fasana ist Opfer...
Fog ransomware gang abuses employee monitoring tool in unusual multi-stage attack – Source: www.csoonline.com
Source: www.csoonline.com – Author: Hackers use Syteca, GC2, and Adaptix in an espionage-style intrusion against an Asian financial institution. Fog ransomware hackers, known for targeting US...
Ungepatchte Lücken ermöglichen Übernahme von GitLab-Konten – Source: www.csoonline.com
Source: www.csoonline.com – Author: Admins und Entwickler, die selbstverwaltete Installationen über GitLab verwenden, sollten so schnell wie möglich ein Upgrade durchführen. Experten warnen vor einem neuen...
How to log and monitor PowerShell activity for suspicious scripts and commands – Source: www.csoonline.com
Source: www.csoonline.com – Author: Attackers are increasingly abusing sanctioned tools to subvert automated defenses. Tracking your Windows fleet’s PowerShell use — especially consultant workstations — can...
‘Dangerous’ vulnerability in GitLab Ultimate Enterprise Edition – Source: www.csoonline.com
Source: www.csoonline.com – Author: Admins and developers using self-managed installations urged to upgrade ASAP. A new vulnerability in GitLab’s Ultimate Enterprise Edition used for managing source...