Source: www.darkreading.com – Author: Fahmida Y. Rashid Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
Day: June 11, 2025
The AI Fix #54: Will AI collapse under its own garbage, and AI charity “Hunger Games” – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 54 of The AI Fix, Graham saves humanity with a CAPTCHA, Mark wonders whether AI...
SinoTrack GPS Devices Vulnerable to Remote Vehicle Control via Default Passwords – Source:thehackernews.com
Source: thehackernews.com – Author: . Two security vulnerabilities have been disclosed in SinoTrack GPS devices that could be exploited to control certain remote functions on connected...
How to Build a Lean Security Model: 5 Lessons from River Island – Source:thehackernews.com
Source: thehackernews.com – Author: . In today’s security landscape, budgets are tight, attack surfaces are sprawling, and new threats emerge daily. Maintaining a strong security posture...
Microsoft Patches 67 Vulnerabilities Including WEBDAV Zero-Day Exploited in the Wild – Source:thehackernews.com
Source: thehackernews.com – Author: . Microsoft has released patches to fix 67 security flaws, including one zero-day bug in Web Distributed Authoring and Versioning (WebDAV) that...
8 things CISOs have learned from cyber incidents – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISOs who have been through cyber attacks share some of the enduring lessons that have changed their approach to cybersecurity. When a...
Is attacker laziness enabled by genAI shortcuts making them easier to catch? – Source: www.csoonline.com
Source: www.csoonline.com – Author: An OpenAI report details a variety of techniques that the model maker is deploying against various attack methods, especially those leveraging social...
Mirai botnet weaponizes PoC to exploit Wazuh open-source XDR flaw – Source: www.csoonline.com
Source: www.csoonline.com – Author: Popular for monitoring Docker containers, Wazuh is being exploited by two Mirai botnet variants — one of which aligns closely with researchers’...
Seraphic Security Unveils BrowserTotal™ – Free AI-Powered Browser Security Assessment for Enterprises – Source: www.csoonline.com
Source: www.csoonline.com – Author: Available to the public and debuting at the Gartner Security & Risk Management Summit, BrowserTotal is a first of its kind browser security...
New npm threats can erase production systems with a single request – Source: www.csoonline.com
Source: www.csoonline.com – Author: The packages carry backdoors that first collect environment information and then delete entire application directories. Two malicious npm packages have been found...
June 2025 Patch Tuesday: Microsoft Fixes 66 Bugs, Including Active 0-Day – Source:hackread.com
Source: hackread.com – Author: Waqas. Microsoft’s June Patch Tuesday update has landed, bringing security fixes for 66 vulnerabilities across its product line. Among the patched flaws...
Two Mirai Botnets, Lzrd and Resgod Spotted Exploiting Wazuh Flaw – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. Cybersecurity experts at Akamai have uncovered a new threat: two separate botnets are actively exploiting a critical flaw in Wazuh...
OpenAI Shuts Down 10 Malicious AI Ops Linked to China, Russia, Iran, N. Korea – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. OpenAI, a leading artificial intelligence company, has revealed it is actively fighting widespread misuse of its AI tools by malicious...
How LMS Software Supports Secure Online Employee Learning – Source:hackread.com
Source: hackread.com – Author: Owais Sultan. Explore how learning management systems (LMS) software supports safe online learning, protects employee data, and ensures compliance in corporate training. ...
How To Protect Your Family’s Smartphones While on Vacation – Source:www.mcafee.com
Source: www.mcafee.com – Author: Amy Bunn. Summer is synonymous with vacations, a time when families pack their bags, grab their sunscreen, and embark on exciting adventures....
Texas Department of Transportation (TxDOT) data breach exposes 300,000 crash reports – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Texas Department of Transportation (TxDOT) data breach exposes 300,000 crash reports Hackers breached Texas DOT (TxDOT), stealing 300,000 crash reports...
SAP June 2025 Security Patch Day fixed critical NetWeaver bug – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini SAP fixed a critical NetWeaver flaw that let attackers bypass authorization and escalate privileges. Patch released in June 2025 Security...
U.S. CISA adds RoundCube Webmail and Erlang Erlang/OTP SSH server flaws to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds RoundCube Webmail and Erlang Erlang/OTP SSH server flaws to its Known Exploited Vulnerabilities...
Mirai botnets exploit Wazuh RCE, Akamai warned – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Mirai botnets are exploiting CVE-2025-24016, a critical remote code execution flaw in Wazuh servers, Akamai warned. Akamai researchers warn that...
China-linked threat actor targeted +70 orgs worldwide, SentinelOne warns – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini China-linked threat actor targeted over 70 global organizations, including governments and media, in cyber-espionage attacks from July 2024 to March...
Why agent fabrics and registries are central to AI identity security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eric Olden The age of agentic AI is here — and it’s changing everything about how we secure identity. As AI agents...
AI Ready: The Complete Guide to AI-Powered Cybersecurity Training in 2025/2026 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Polatsek Introduction: The AI Cybersecurity Crisis The cybersecurity landscape has fundamentally changed. AI-powered cyberattacks are projected to surge by 50% in...
Why Users Are Satisfied with Secure NHIs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Is Securing Non-Human Identities (NHIs) the Key to User Satisfaction? I can attest to the increasing importance of NHIs. Machine...
Capabilities Unlocked by Advanced NHI Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Can NHI Management Unlock Advanced Security Capabilities? Ever considered the security measures that stand behind extensive data networks? A...
Innovative Approaches to NHI Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Will Rising Cybercrimes Warrant a More Innovative Approach to NHI Protection? With the intensifying wave of cybercrimes, robust and innovative...
5 Common Ways Non-Human Identities Are Exploited – and How to Secure Them – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Kaplan 1) Token Abuse Token misuse remains one of the most effective attack techniques – especially when access tokens are bearer-based...
OffensiveCon25 – Breaking The Sound Barrier: Exploiting CoreAudio Via Mach Message Fuzzing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenter: Dillon Franke Our sincere appreciation to OffensiveCon by Binary Gecko, and the Presenters/Authors for publishing their outstanding OffensiveCon 2025...
How to Overcome Modern Colocation Challenges with DCIM Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi Effective digital infrastructure management remains crucial as colocation data centers grow more intricate and essential in supporting global digital operations....
Microsoft’s June 2025 Patch Tuesday Addresses 65 CVEs (CVE-2025-33053) – Source: securityboulevard.com
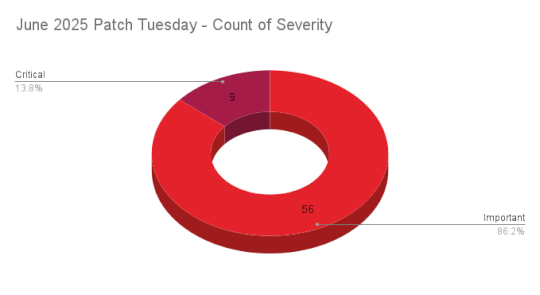
Source: securityboulevard.com – Author: Research Special Operations 9Critical 56Important 0Moderate 0Low Microsoft addresses 65 CVEs, including two zero-day vulnerabilities, with one being exploited in the wild....
Randall Munroe’s XKCD ‘Trojan Horse’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, June 11, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...