Source: krebsonsecurity.com – Author: BrianKrebs Microsoft today released security updates to fix at least 67 vulnerabilities in its Windows operating systems and software. Redmond warns that...
Day: June 11, 2025
Congress Introduces Bill to Strengthen Healthcare Cybersecurity – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: US legislators have introduced a new Healthcare Cybersecurity Bill to Congress, which is designed to expand the federal government’s role in preventing...
News alert: Seraphic launches BrowserTotal™ — a free AI-powered tool to stress test browser security – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Tel Aviv, Israel, June 9, 2025, CyberNewswire — Seraphic Security, a leader in enterprise browser security, today announced the launch of...
Toxic trend: Another malware threat targets DeepSeek – Source: securelist.com
Source: securelist.com – Author: Lisandro Ubiedo Introduction DeepSeek-R1 is one of the most popular LLMs right now. Users of all experience levels look for chatbot websites...
Mirai Botnets Exploit Flaw in Wazuh Security Platform – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
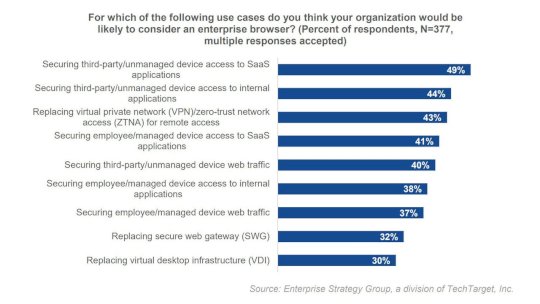
Bridging the Secure Access Gap in Third-Party, Unmanaged Devices – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
India’s Security Leaders Struggle to Keep Up With Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Stealth Falcon APT Exploits Microsoft RCE Zero-Day in Mideast – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
PoC Code Escalates Roundcube Vuln Threat – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Red Canary Expands AI Innovations to Cut Alert Overload – Source: www.darkreading.com
Source: www.darkreading.com – Author: Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This website is...
GitHub: How Code Provenance Can Prevent Supply Chain Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
Gartner: Secure Enterprise Browser Adoption to Hit 25% by 2028 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
The AI Fix #54: Will AI collapse under its own garbage, and AI charity “Hunger Games” – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 54 of The AI Fix, Graham saves humanity with a CAPTCHA, Mark wonders whether AI...
8 things CISOs have learned from cyber incidents – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISOs who have been through cyber attacks share some of the enduring lessons that have changed their approach to cybersecurity. When a...
Is attacker laziness enabled by genAI shortcuts making them easier to catch? – Source: www.csoonline.com
Source: www.csoonline.com – Author: An OpenAI report details a variety of techniques that the model maker is deploying against various attack methods, especially those leveraging social...
Mirai botnet weaponizes PoC to exploit Wazuh open-source XDR flaw – Source: www.csoonline.com
Source: www.csoonline.com – Author: Popular for monitoring Docker containers, Wazuh is being exploited by two Mirai botnet variants — one of which aligns closely with researchers’...
Seraphic Security Unveils BrowserTotal™ – Free AI-Powered Browser Security Assessment for Enterprises – Source: www.csoonline.com
Source: www.csoonline.com – Author: Available to the public and debuting at the Gartner Security & Risk Management Summit, BrowserTotal is a first of its kind browser security...
New npm threats can erase production systems with a single request – Source: www.csoonline.com
Source: www.csoonline.com – Author: The packages carry backdoors that first collect environment information and then delete entire application directories. Two malicious npm packages have been found...
Why agent fabrics and registries are central to AI identity security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eric Olden The age of agentic AI is here — and it’s changing everything about how we secure identity. As AI agents...
AI Ready: The Complete Guide to AI-Powered Cybersecurity Training in 2025/2026 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Polatsek Introduction: The AI Cybersecurity Crisis The cybersecurity landscape has fundamentally changed. AI-powered cyberattacks are projected to surge by 50% in...
Why Users Are Satisfied with Secure NHIs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Is Securing Non-Human Identities (NHIs) the Key to User Satisfaction? I can attest to the increasing importance of NHIs. Machine...
Capabilities Unlocked by Advanced NHI Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Can NHI Management Unlock Advanced Security Capabilities? Ever considered the security measures that stand behind extensive data networks? A...
Innovative Approaches to NHI Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Will Rising Cybercrimes Warrant a More Innovative Approach to NHI Protection? With the intensifying wave of cybercrimes, robust and innovative...
5 Common Ways Non-Human Identities Are Exploited – and How to Secure Them – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Kaplan 1) Token Abuse Token misuse remains one of the most effective attack techniques – especially when access tokens are bearer-based...
OffensiveCon25 – Breaking The Sound Barrier: Exploiting CoreAudio Via Mach Message Fuzzing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenter: Dillon Franke Our sincere appreciation to OffensiveCon by Binary Gecko, and the Presenters/Authors for publishing their outstanding OffensiveCon 2025...
How to Overcome Modern Colocation Challenges with DCIM Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi Effective digital infrastructure management remains crucial as colocation data centers grow more intricate and essential in supporting global digital operations....
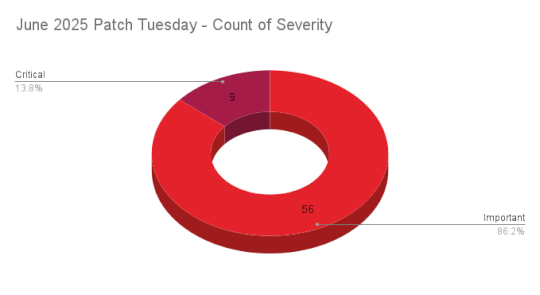
Microsoft’s June 2025 Patch Tuesday Addresses 65 CVEs (CVE-2025-33053) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Research Special Operations 9Critical 56Important 0Moderate 0Low Microsoft addresses 65 CVEs, including two zero-day vulnerabilities, with one being exploited in the wild....
Randall Munroe’s XKCD ‘Trojan Horse’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, June 11, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...