Source: www.lastwatchdog.com – Author: bacohido Palo Alto, Calif., May 21, 2025 – DataHub, by Acryl Data, the leading open source metadata platform, today announced it has...
Day: May 21, 2025
News alert: Attaxion integrates its EASM Platform with ENISA’s EU Vulnerability Database (EUVD) – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Dover, Del., May 21, 2025, CyberNewswire — Attaxion, the external attack surface management (EASM) vendor with industry-leading asset coverage, announces the...
What to do if you can’t get into your Facebook or Instagram account – Source: www.theguardian.com
Source: www.theguardian.com – Author: Samuel Gibbs Consumer technology editor Your Facebook or Instagram account can be your link to friends, a profile for your work or...
Dero miner zombies biting through Docker APIs to build a cryptojacking horde – Source: securelist.com
Source: securelist.com – Author: Amged Wageh Introduction Imagine a container zombie outbreak where a single infected container scans the internet for an exposed Docker API, and...
Proofpoint to acquire Hornetsecurity in move to expand Microsoft 365 threat protection – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: SECURITY Proofpoint to acquire Hornetsecurity in move to expand Microsoft 365 threat protection Cybersecurity firm Proofpoint Inc. today announced it plans to acquire Hornetsecurity...
Proofpoint to acquire Hornetsecurity for over $1 billion – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Skip to main content Voting is open for the 2025 CyberScoop 50 awards! Click here! Listen to this article 0:00 Learn more....
Proofpoint CEO On ‘Monumental’ Hornetsecurity Deal, MSP Growth In US – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: With the acquisition deal positioning Proofpoint for major growth with MSPs and SMBs in the U.S. market, ‘this is a big strategic...
Cybersecurity firm Proofpoint to buy European rival for over $1 billion as it eyes IPO – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Pavlo Gonchar | Lightrocket | Getty Images Cybersecurity firm Proofpoint is acquiring European rival Hornetsecurity for north of $1 billion to strengthen...
RSAC 2025: Agentic AI, Identity And The New Rules Of Cyber Defense – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Cybersecurity leaders gather at RSAC 2025 to explore AI innovation, identity threats, and the future … More of digital defense in an...
Voice of the Vendor: RSAC 2025, Part 1 – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Acer America Corp. is a computer manufacturer of business and consumer PCs, notebooks, ultrabooks, projectors, servers, and storage products. Location 333 West...
Threat intelligence platform buyer’s guide: Top vendors, selection advice – Source: www.csoonline.com
Source: www.csoonline.com – Author: Threat intelligence platforms have evolved and became essential security defensive tools. Here is what you need to know before choosing a TIP....
Poor DNS hygiene is leading to domain hijacking – Source: www.csoonline.com
Source: www.csoonline.com – Author: Infoblox says crooks are finding and taking over ‘dangling’ CNAME records for scams. Threat actors continue to find ways of hijacking domains...
CSO30 Australia Awards 2025: Nominations now open – Source: www.csoonline.com
Source: www.csoonline.com – Author: CSO Australia is accepting nominations for the 2025 CSO30 Awards, entries close on 20 June. Nominations are officially open for the 2025...
8 KI-Sicherheitsrisiken, die Unternehmen übersehen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine Studie zeigt: Fast zwei Drittel der Unternehmen versäumen es, die Auswirkungen von GenAI-Tools auf die Sicherheit zu prüfen. In ihrem Wettlauf...
You’ve already been targeted: Why patch management is mission-critical – Source: www.csoonline.com
Source: www.csoonline.com – Author: Every day you delay a patch is a day attackers gain the upper hand. Proactive defense starts with closing the doors they...
Skitnet malware: The new ransomware favorite – Source: www.csoonline.com
Source: www.csoonline.com – Author: The modular malware is tailor-made for ransomware as it features dedicated plugins for theft, encryption, and persistence. Ransomware operators are now actively...
Uncensored AI Tool Raises Cybersecurity Alarms – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new AI chatbot called Venice.ai has gained popularity in underground hacking forums due to its lack of content restrictions. According to...
Debt Collector Data Breach Affects 200,000 Harbin Clinic Patients – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A third-party data breach has compromised personal information belonging to more than 200,000 Harbin Clinic patients. The breach stems from a cyber-attack...
Russian APT Groups Intensify Attacks in Europe with Zero-Day Exploits and Wipers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The end of 2024 and the start of 2025 were marked by the strengthened intensity of malicious cyber activity by Russian-aligned hacking...
Fitting Cybersecurity Investments into Your Budget – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Can You Make Cybersecurity Budget Allocations Effective? How do organizations allocate effective funds to cybersecurity? The million-dollar question remains...
Free to Choose the Right Security for Your Cloud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Is Choosing Cloud Security a Complex Task? From financial services and healthcare to DevOps and SOC teams, businesses across sectors...
Attack Surface Reduction for Enterprises: A Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: FireMon Today’s enterprises have embraced digital evolution. Business deals are conducted in online spaces, contracts are signed with a keyboard, data is...
BSidesLV24 – GroundFloor – Windows EventLog Persistence? The Windows Can Help Us – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – GroundFloor – Windows EventLog Persistence? The Windows Can Help Us Author/Presenter: Fabricio...
Why Your MTTR Is Too Slow — And How to Fix It Fast – Source: securityboulevard.com
Source: securityboulevard.com – Author: psilva SLASH YOUR MTTR! Join Us for a Live Webinar on Faster Incident Response & Reduced Downtime. MTTR (Mean Time to Response)...
Randall Munroe’s XKCD ‘Renormalization’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, May 21, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
The Role of Microsegmentation in Managing Lateral Movement Through Inbound and Outbound Traffic Policies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Klinchin Microsegmentation has become a foundational component of enterprise security and a Zero Trust Architecture (ZTA). As threats continue to grow in...
The State of AI in Cybersecurity 2025: What’s Working, What’s Lagging, and Why It Matters Now More Than Ever – Source: securityboulevard.com
Source: securityboulevard.com – Author: MixMode Threat Research MixMode Threat Research MixMode Threat Research is a dedicated contributor to MixMode.ai’s blog, offering insights into the latest advancements and...
Application Security Testing: Security Scanning and Runtime Protection Tools – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mend.io Communications Application security testing (AST) is the process of identifying and fixing security vulnerabilities in software applications. It ensures that applications...
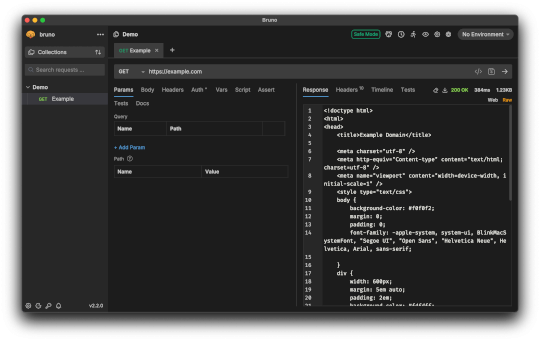
Scripting Outside the Box: API Client Security Risks (2/2) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Oskar Zeino-Mahmalat, Paul Gerste Welcome back to the second part of our deep dive into the security risks of API clients. In...
Event Preview: 2025 Threat Detection & Incident Response (Virtual) Summit – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s 2025 Threat Detection & Incident Response (TDIR) Summit will take place as a virtual summit on Wednesday, May 21st...