Source: securelist.com – Author: Kaspersky ICS CERT Trends Relative stability from quarter to quarter. The percentage of ICS computers on which malicious objects were blocked remained...
Day: May 15, 2025
Stealth RAT uses a PowerShell loader for fileless attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: Remcos RAT gets a stealthy upgrade as attackers ditch old office exploits for a fileless PowerShell loader that runs entirely in memory....
Alternatives to Microsoft Outlook webmail come under attack in Europe – Source: www.csoonline.com
Source: www.csoonline.com – Author: Suspected Russian XSS attacks on organizations running Roundcube, Horde, MDaemon, and Zimbra. CISOs need to ensure that web email clients and browsers...
Data on sale: Trump administration withdraws data broker oversight proposal – Source: www.csoonline.com
Source: www.csoonline.com – Author: While the US Consumer Financial Protection Bureau cites policy shifts and legal concerns, critics argue the move undermines consumer privacy protections. The...
The most effective phishing QR code is a new drug and alcohol policy supposedly from HR – Source: www.csoonline.com
Source: www.csoonline.com – Author: Phishing emails presumably from IT or HR remain the most potent, with Zoom clips from managers, HR training info, and email server...
‘Aggressive, creative’ hackers behind UK breaches now eyeing US retailers – Source: www.csoonline.com
Source: www.csoonline.com – Author: The same group is believed to be behind the M&S breach and several other high-profile incidents in the US and UK. Google...
Hacker nehmen Rüstungslieferanten der Ukraine ins Visier – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Cyberkriegertruppe Fancy Bear gilt als eine der einflussreichsten staatlich gesteuerten Hackergruppen weltweit. Nun haben Experten eine neue Kampagne der Hacker aus...
How phones get hacked: 7 common attack methods explained – Source: www.csoonline.com
Source: www.csoonline.com – Author: Mobile security often is tighter than PC security, but users can still be fooled by social engineering techniques, and smartphones can still...
Die acht wichtigsten Sicherheitsmetriken – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 15. Mai 20255 Minuten Business IT AlignmentIT-StrategieROI und Metriken Zur Bewertung der Cybersicherheitsleistung sind Kennzahlen entscheidend – das sind die wichtigsten...
Ivanti patches two EPMM flaws exploited in the wild – Source: www.csoonline.com
Source: www.csoonline.com – Author: The vulnerabilities located in third-party open-source libraries impact Ivanti’s mobile device management appliance and can lead to unauthenticated remote code execution. IT...
Neue EU-Schwachstellen-Datenbank geht an den Start – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 14. Mai 20255 Minuten Threat and Vulnerability Management Nach dem Beinahe-Aus des CVE-Programm im April hat die Europäischen Agentur für Cybersicherheit...
CISA adds the notorious TeleMessage flaw to KEV list – Source: www.csoonline.com
Source: www.csoonline.com – Author: TeleMessage TM SGNL, a version of the Signal messaging app, contains a hidden functionality vulnerability in which the archiving backend holds cleartext...
Marks & Spencer räumt Datendiebstahl ein – Source: www.csoonline.com
Source: www.csoonline.com – Author: Der britische Einzelhandelsriese Marks & Spencer ist von einer Ransomware-Attacke betroffen. Der britische Retail-Riese Marks & Spencer wurde von Cyberkriminellen heimgesucht und...
Spain to vet power plants’ cybersecurity for ‘great blackout’ cause – Source: www.csoonline.com
Source: www.csoonline.com – Author: The Spanish government is gathering information on the cybersecurity measures of the country’s small electricity generating companies to assess whether malicious actors...
Patch Tuesday for May: Five zero day vulnerabilities CISOs should focus on – Source: www.csoonline.com
Source: www.csoonline.com – Author: Five of the Microsoft 70 vulnerabilities already under attack, and SAP and Zoom flaws are equally critical. CISOs need to pay attention...
4 critical leadership priorities for CISOs in the AI era – Source: www.csoonline.com
Source: www.csoonline.com – Author: The rise of AI demands a new set of goals and strategies for CISOs, who must put appropriate parameters around the use...
GUESST ESSAY: Cybercrime for hire: small businesses are the new bullseye of the Dark Web – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Doni Brass Small businesses make up 90% of all companies worldwide and account for half of global GDP. Yet despite...
Critical Infrastructure Under Siege: OT Security Still Lags – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
Infosec Layoffs Aren’t the Bargain That Boards May Think – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
AI Agents May Have a Memory Problem – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Using a Calculator to Take Guesswork Out of Measuring Cyber Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Ivanti EPMM Zero-Day Flaws Exploited in Chained Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Exploring Gender Bias Across Science Classrooms in India
Asambhava Shubha shares how conducting “draw a scientist” experiments in numerous classrooms inspired a documentary project on girls in STEM. Source Views: 0
Military and Veterans Affinity Group: Advocacy
As part of the Military and Veterans AG’s spotlight month, AG co-lead Helen Mills discusses how to be an ally and advocate for the military and...
What Is Generative AI (GenAI)? – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk Gartner’s Top Cybersecurity Trends of 2025 report emphasizes the growing influence of generative AI (GenAI), highlighting new opportunities for organizations...
Google’s Advanced Protection Now on Android – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Steve67 • May 14, 2025 7:35 AM They are adopting features that already exist in GrapheneOS, such as...
Smashing Security podcast #417: Hello, Pervert! – Sextortion scams and Discord disasters – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content Don’t get duped, doxxed, or drained! In this episode of “Smashing Security” we dive into the creepy...
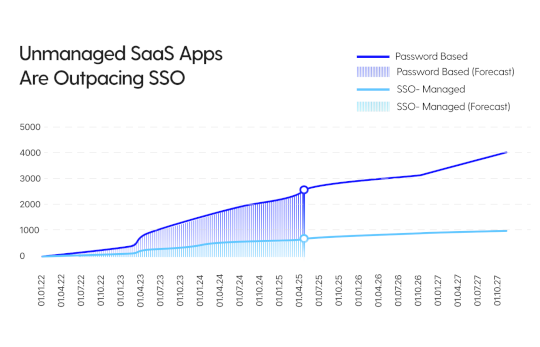
5 Identity Security Risks We Found in a Regulated Enterprise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog Even the most mature enterprises encounter new, subtle, and complex identity security challenges from the rapid growth of SaaS....
Stay Relaxed with Efficient Non-Human Identity Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Are You Safe With Your Current Non-Human Identity Security? The migration of services to the cloud promises flexibility, scalability, and...
Continuous Improvement in NHIs Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Can Continuous Improvement in NHIs Management Be the Key to Securing Your Operations? You’re no stranger to the importance of...