Source: securityboulevard.com – Author: Amy Cohn Capturing the Essence of Powerful Secrets Scanning Wondering how to enhance your organization’s cybersecurity measures? Among the vast spectrum of...
Month: April 2025
Certain Your Data Is Safe in the Cloud? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Confident Your Data Safety Measures Are Up to Scratch? The rise of digital transformation is not without its...
BSidesLV24 – Ground Truth – PhishDefend: A Reinforcement Learning Framework – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – Ground Truth – PhishDefend: A Reinforcement Learning Framework Author/Presenter: Bobby Filar Our...
Bugcrowd Launches Red Team Service to Test Cybersecurity Defenses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Bugcrowd today at the 2025 RSA Conference announced its intent to create a red team service to test cybersecurity defenses...
Blackpoint Cyber Extends MDR Service to Improve Cyber Resiliency – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Blackpoint Cyber today at the 2025 RSA Conference unveiled a unified security posture and response platform that is based on...
African Telecom Giant MTN Group Discloses Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire MTN Group, one of the largest telecommunications services providers in Africa, says the personal information of some customers was compromised...
News alert: Case dismissed against VPN executive, affirms no-logs policy as a valid legal defense – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Toronto, Canada, Apr. 28, 2025, CyberNewswire — Windscribe, a globally used privacy-first VPN service, announced today that its founder, Yegor Sak,...
MY TAKE: As RSAC 2025 opens, Microsoft, Amazon make GenAI grab — will control tighten? – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido SAN FRANCISCO — RSAC 2025 kicks off today at Moscone Center, with more than 40,000 cybersecurity pros,...
SAP NetWeaver Visual Composer Flaw Under Active Exploitation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
AI, Automation, and Dark Web Fuel Evolving Threat Landscape – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Forget the Stack; Focus on Control – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jonathan Meler Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
DoJ Data Security Program Highlights Data Sharing Challenges – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Reporting lines: Could separating from IT help CISOs? – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISOs who report to the CFO find that the shift away from IT can improve their ability to translate risk into business...
IT-Security ist keine Vertrauenssache – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine aktuelle Studie warnt davor, IT-Kompetenz mit echter Sicherheitskompetenz zu verwechseln. G Data warnt davor, die Komplexität heutiger Bedrohungsszenarien zu unterschätzen. Pictrider...
Creating Impenetrable Cloud Compliance Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Are Your Cloud Compliance Practices Truly Impenetrable? Non-Human Identities (NHIs) and Secrets Management have emerged as critical components of an...
Delivering Value with Advanced IAM – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why is Advanced Identity and Access Management Necessary? Have you ever imagined the chaos that would ensue if all the...
Optimistic About Your Cybersecurity Strategy? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why should Cybersecurity Strategy Spark Optimism? Why is there a growing wave of optimism surrounding cybersecurity strategies, especially with the...
Are You Capable of Managing NHIDs Efficiently? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Understanding the Complexities of Managing NHIDs? When it comes to reinforcing cybersecurity, how confident are you in providing...
New geolocus-cli For ONYPHE’s Geolocus Database – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr ONYPHE has made available a free API and free MMDB download of their new Geolocus database. It provided IP address metadata...
BSidesLV24 – Ground Truth – Seek Out New Protocols, And Boldly Go Where No One Has Gone Before – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – Ground Truth – Seek Out New Protocols, And Boldly Go Where No...
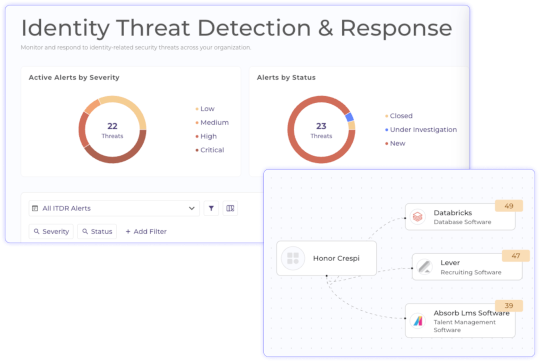
Grip Security Defines the Identity-Driven Future of SecOps – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog Security operations are entering a new era—one where identities, not endpoints, determine risk and response—and Grip is at the...
Identity is the New Perimeter: CybeReady’s Analysis of IBM’s X-Force 2025 Threat Intelligence Index – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Polatsek The New Dawn Returns – Horizon Shifts in Cyberattack Trends Following our in-depth analysis of IBM’s 2025 Threat Intelligence Index,...
NSFOCUS APT Monthly Briefing – March 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS Regional APT Threat Situation Overview In March 2025, the global threat hunting system of NSFOCUS Fuying Laboratory discovered a total of...
GDPR Data Breach Notification Template With Examples [Download] – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amit Kumar The GDPR is a law developed by the European Union (EU) to protect individuals’ personal data. Although it originated in...
Key Cybersecurity Considerations for 2025 – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team As we usher in a new year, it’s crucial to focus on key areas in cybersecurity that demand our attention....
Make the Most of Your Holiday Cybersecurity Awareness Efforts – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The holiday season is a time for joy, celebration, and, unfortunately, an uptick in cyber threats. From phishing scams that...
MY TAKE: Notes on how GenAI is shifting tension lines in cybersecurity on the eve of RSAC 2025 – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido SAN FRANCISCO — The first rule of reporting is to follow the tension lines—the places where old...
Access Uncoder AI Functionality via API – Source: socprime.com
Source: socprime.com – Author: Steven Edwards How It Works The Uncoder AI API provides access to the platform’s core functionality, enabling integration into your existing CI/CD...
Day in the Life of an Engineering Manager: Sahara Becker
Sahara is a Cybersecurity Operations Manager at McMaster-Carr. Learn more about her work as an Engineering Manager and how you can #BeThatEngineer! Source Views: 8
Engineering Management Student of the Month: Ann Shih
Learn more about Ann Shih and her experience as an engineering student! Source Views: 0



















![gdpr-data-breach-notification-template-with-examples-[download]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2025/04/169674-gdpr-data-breach-notification-template-with-examples-download-source-securityboulevard-com.jpg)




