Source: securityboulevard.com – Author: cybernewswire San Francisco, California, March 3rd, 2025, CyberNewsWire With the growing importance of security compliance for startups, more companies are seeking to...
Month: March 2025
DEF CON 32 – Differential Privacy Beyond Algorithm: Challenges For Deployment – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Differential Privacy Beyond Algorithm: Challenges For Deployment Author/Presenter: Rachel Cummings...
What Is Credential Management? Best Practices and Examples – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Strong credentials safeguard your digital resources, but common mistakes like weak passwords, credential reuse, and exposed secrets give attackers an...
What Is Code Scanning? Approaches and Best Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Identifying security flaws early in the software development lifecycle (SDLC) prevents vulnerabilities from reaching production, where they become more complex...
6 Effective Secret Scanning Tools – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Secret scanning tools identify and protect sensitive information that may be exposed within software assets. Developers often embed secrets like...
Randall Munroe’s XKCD ‘Giants’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Monday, March 3, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Security Pros Push Back as Trump Orders Halt to Cyber Ops vs. Russia – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The Trump Administration’s reported move to stop federal agencies from offensive cyber operations and investigations against Russia drew sharp rebuke...
DEF CON 32 – Cybersecurity Schoolhouse Rock – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » DEF CON 32 – Cybersecurity Schoolhouse Rock by Marc Handelman on...
Enhancing Application Security | Contrast ADR and Splunk | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Contrast Marketing Have you silenced WAF alerts in your SIEM or just stopped sending them altogether? You’re not alone. Many SOCs find...
Mozilla Revises Firefox Terms of Use After Inflaming Users Over Data Usage – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Esther Shein Image: iStock Mozilla wants to set the record straight: The company needs a license “to make some of the basic...
EU’s New Product Liability Directive & Its Cybersecurity Impact – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jatin Mannepalli Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Latin American Orgs Face 40% More Attacks Than Global Average – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Cisco’s SnapAttack Deal Expands Splunk’s Capabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
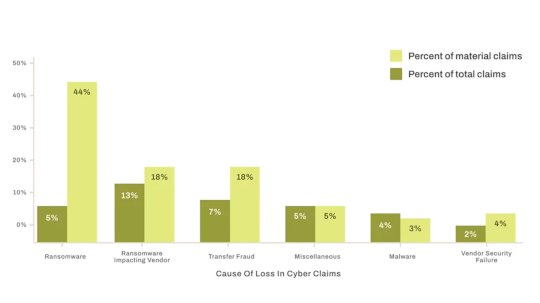
Third-Party Risk Top Cybersecurity Claims – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Stop targeting Russian hackers, Trump administration orders US Cyber Command – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley For years, the United States has joined with much of the rest of the world, in declaring that Russia poses...
Mobile malware evolution in 2024 – Source: securelist.com
Source: securelist.com – Author: Anton Kivva These statistics are based on detection alerts from Kaspersky products, collected from users who consented to provide statistical data to...
Black Basta Leak Offers Glimpse Into Group’s Inner Workings – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend A massive hoard of internal chats has been leaked from the Black Basta ransomware group, rivalling the Conti leaks of...
Ransomware access playbook: What Black Basta’s leaked logs reveal – Source: www.csoonline.com
Source: www.csoonline.com – Author: Analyzing leaked internal communication logs, security researchers are piecing together how one of the most notorious ransomware groups infiltrates its victims. Black...
Why cyber attackers are targeting your solar energy systems — and how to stop them – Source: www.csoonline.com
Source: www.csoonline.com – Author: Businesses that install and own solar distributed energy resources increase their attack surface and that of the electric grid. High energy costs...
Die besten XDR-Tools – Source: www.csoonline.com
Source: www.csoonline.com – Author: XDR-Tools bieten tiefergehende und automatisierte Möglichkeiten, Bedrohungen zu stoppen. Das sind die besten Lösungen im Bereich Extended Detection and Response. Lesen Sie,...
SWE Diverse Podcast Ep 250: Late Career Engineers Living Without Limits
Hear the inspiring stories of these late career engineers who are pursuing advocacy work, plus the advice they would give to their younger selves, on Diverse:...
SWE Diverse Podcast Ep 249: Allyship and Unlearning Silence With Author Elaine Lin Hering
Elaine Lin Hering explores the ways that individuals and organizations unintentionally silence marginalized voices, and how to change course, on this episode of Diverse: a SWE...
SWE President Discusses Closing the STEM Gap on Capitol Hill
Learn about this briefing at the Women’s Congressional Policy Institute on the challenges and solutions to increasing diversity in the STEM workforce. Source Views: 0
Navigating Career Advancement: A SWE Mentor Conversation
Want a behind-the-scenes look of what mentorship can look like for women engineers? Renee LaRocca shares the recent advice she gave to one of her mentees...
Celebrate SWE Outreach: A Year in Review
Read the fourth annual issue of “Celebrate SWE Outreach: A Year in Review” to learn about the Outreach and SWENext accomplishments created by SWE volunteers in...
How Engineer Kristin Ginn Returned to Work After a Career Break
Kristin Ginn returned to the engineering workforce after stepping back to focus on her family for four years. Read her story, including her effective two-phase networking...
SWE Cambridgeshire Affiliate Hosts “Meet, Greet & Treats” Outreach Event
Learn about the inaugural networking day that brought together 60 attendees from 20 organizations, fostering connection and collaboration. Source Views: 2
SWE Diverse Podcast Ep 248: From Chemical Engineer to Science Superheroine With Tamara Robertson
Engineer, TV host and STEM advocate Tamara Robertson (she/her) joined us on this episode of Diverse: a SWE podcast to discuss her efforts to instill hope...
11 Application Security Testing Types – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cycode Team As organizations accelerate their release cycles and rely on complex software ecosystems, security vulnerabilities become harder to track—and easier for...
Living Without Limits and Refired About SWE
As part of the Late Career & Retiree Affinity Group’s spotlight month, Vicki Johnson (she/her) reflects on her retirement journey and connections with other LCR AG...