Source: www.techrepublic.com – Author: Allison Francis Published March 27, 2025 Microsoft’s .NET MAUI lets developers build cross-platform apps in C#, but its use of binary blob...
Day: March 27, 2025
Which Top Cybersecurity Role of 2024 Was Featured in 64,000+ Job Postings? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Security engineer was the most common title in cybersecurity job listings in 2024, according to security and IT workforce management...
A Taxonomy of Adversarial Machine Learning Attacks and Mitigations – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Clive Robinson • March 27, 2025 1:17 PM @ ALL, Hmm… “… comprehensive taxonomy of adversarial machine learning attacks…” Those...
DoJ Recovers $5M Lost in BEC Fraud Against Workers’ Union – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Fake DeepSeek Ads Spread Malware to Google Users – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
High-Severity Cloud Security Alerts Tripled in 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Malaysian PM says “no way” to $10 million ransom after alleged cyber attack against Kuala Lumpur airport – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Malaysian Prime Minister Anwar Ibrahim has said that he refused to pay a US $10 million ransom demanded by hackers...
Smashing Security podcast #410: Unleash the AI bot army against the scammers – now! – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content A YouTuber has unleashed an innovative AI bot army to disrupt and outwit the world of online...
Is Someone Lurking in The Background Waiting To Impersonate You? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Are you confident someone isn’t lurking in the background on your computer right now, gathering information and preparing to impersonate...
What VirusTotal Missed — Discover with Unknown Cyber – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary “VirusTotal gives you opinions. Hybrid Analysis gives you behavior. Unknown Cyber gives you the truth in the code—before the malware even...
More Solar System Vulnerabilities Expose Power Grids to Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Researchers at cybersecurity firm Forescout have found dozens of vulnerabilities across solar power system products from Sungrow, Growatt and SMA,...
AI Security Firm Straiker Emerges From Stealth With $21M in Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Another AI security firm has announced its launch. Straiker emerged from stealth mode on Thursday with a solution designed to...
OpenAI Offering $100K Bounties for Critical Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Artificial intelligence tech giant OpenAI has raised its maximum bug bounty payout to $100,000 (up from $20,000) as part of...
Russian Ransomware Gang Exploited Windows Zero-Day Before Patch – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Security researchers at Trend Micro say one of the six zero-days patched by Microsoft earlier this month was being exploited...
AMTSO Releases Sandbox Evaluation Framework – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs AMTSO, the cybersecurity industry’s testing standards community, on Wednesday announced the creation of a sandbox evaluation framework whose goal is...
Island Banks $250M in Series E Funding for Enterprise Browser – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Island, a late-stage startup selling a security-themed enterprise browser, on Wednesday announced another massive $250 million Series E funding round...
New Ransomware Group Claims Attack on US Telecom Firm WideOpenWest – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A new ransomware group claims to have hacked the systems of US telecommunications provider WideOpenWest (WOW!), and to have taken...
SplxAI Raises $7 Million for AI Security Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire AI security startup SplxAI today announced raising $7 million in a seed funding round that brings the total raised by...
Creating Community With CCASE and the City College of San Francisco Affiliate
Learn how SWE’s Community College Affiliate Support and Expansion (CCASE) Program helped the SWE City College of San Francisco Affiliate grow their membership and activities. Source...
Weaver Ant Attack Detection: China-Linked Group Targets a Telecom Provider in Asia Using Multiple Web Shells, Including China Chopper – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk APT groups from China were ranked among the top global cyber threats alongside North Korea, russia, and Iran, showcasing heightened...
CVE-2025-1974: Critical Set of Vulnerabilities in Ingress NGINX Controller for Kubernetes Leading to Unauthenticated RCE – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Heads-up for Kubernetes admins! A batch of five critical vulnerabilities called “IngressNightmare” (CVE-2025-24513, CVE-2025-24514, CVE-2025-1097, CVE-2025-1098, and CVE-2025-1974) affecting Ingress...
Die 10 häufigsten IT-Sicherheitsfehler – Source: www.csoonline.com
Source: www.csoonline.com – Author: In der Praxis begegnen Incident-Response-Teams immer wieder denselben Schwachstellen. Welche sind das und wie lassen sich diese beheben? Von ungepatchten Sicherheitslücken bis...
Even anti-scammers get scammed: security expert Troy Hunt pwned by phishing email – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 26 Mar 20254 mins CSO and CISOPhishingSocial Engineering Illustrating that there is no such thing as immunity from phishing, the founder...
KI-Agenten erobern die Cybersicherheitsbranche – Source: www.csoonline.com
Source: www.csoonline.com – Author: Unternehmen setzen zunehmend bei Cybersecurity auf smarte Automatisierung. Microsofts Security Copilot-Agenten sollen hierbei helfen. Microsoft führt KI-Agenten ein, um die Cybersicherheit angesichts...
Mit GenAI zum Insider-Threat – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine aktuelle Studie offenbart: Ohne angemessene Datensicherheitskontrollen macht generative künstliche Intelligenz (GenAI) Mitarbeiter zu unbeabsichtigten Insider-Bedrohungen. Viele Unternehmen haben nicht auf dem...
VMware plugs a high-risk vulnerability affecting its Windows-based virtualization – Source: www.csoonline.com
Source: www.csoonline.com – Author: Improper access control issues in VMware Tools for Windows could allow privilege escalation on affected virtual machines. Broadcom is warning customers of...
Identity security: A critical defense in 2025’s threat landscape – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gerry Gebel Trends in identity security for 2025 Managing multiple IDPs becomes the new normal The days of relying on a single...
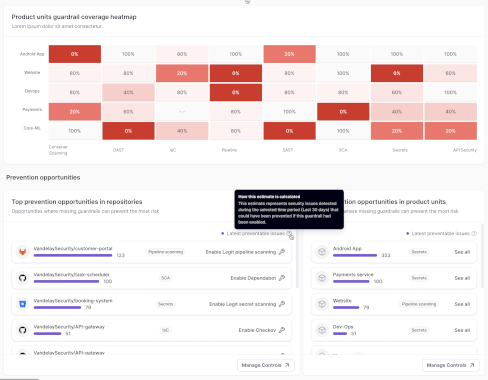
Legit Announces New Vulnerability Prevention Capabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Mandel Get details on Legit’s new capabilities that allow AppSec teams to prevent introducing vulnerabilities.. Software development, accelerated by AI, continues...
Which frameworks assist in ensuring compliance for NHIs? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why Compliance Frameworks are Crucial for NHIs? Could the answer to your organization’s cybersecurity woes lie in Non-Human Identities (NHIs)?...
How can I align our NHI management with GDPR and other standards? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Is Your NHI Management GDPR Compliant? It isn’t just humans who have identities, but machines as well. In-depth understanding and...