Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Ronstik via Alamy Stock Photo An active, one-click phishing campaign is targeting the X accounts of high-profile...
Month: February 2025
Proactive Vulnerability Management for Engineering Success – Source: www.darkreading.com
Source: www.darkreading.com – Author: Remi Yazigi Remi Yazigi, Information Security Engineer, Cisco Systems February 3, 2025 4 Min Read Source: Cagkan Sayin via Alamy Stock Photo...
Black Hat USA 2024 Highlights – Source: www.darkreading.com
Source: www.darkreading.com – Author: TechTarget and Informa Tech’s Digital Business Combine.TechTarget and Informa TechTarget and Informa Tech’s Digital Business Combine. Together, we power an unparalleled network...
CISA Warns of Backdoor Vulnerability in Contec Patient Monitors – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A hidden backdoor function embedded in the firmware of the Contec CMS8000 patient monitor has been identified by the US Cybersecurity and...
High-profile X Accounts Targeted in Phishing Campaign – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A phishing campaign targeting high-profile X accounts has been observed hijacking and exploiting them for fraudulent activity. The campaign, uncovered by SentinelLabs,...
768 CVEs Exploited in the Wild in 2024 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A total of 768 CVEs were publicly reported as exploited in the wild for the first time in 2024, according to new...
European Police: Data Volumes and Deletion Hindering Investigations – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: European police are struggling to access, analyze and store potentially huge volumes of data needed to advance cybercrime investigations, a new Europol...
UK Announces “World-First” AI Security Standard – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The UK government has announced a new AI Code of Practice which it claims will form the basis of a global standard...
Sophos finalizes $859 million acquisition of rival Secureworks – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 03 Feb 20252 mins Channel SalesIntrusion Detection SoftwareManaged Service Providers The deal makes Sophos the leading cybersecurity provider of MDR services,...
Schutz von Onlinekonten: Starkes Passwort reicht nicht aus – Source: www.csoonline.com
Source: www.csoonline.com – Author: Einfache Passwörter gelten schon seit langem als Sicherheitsrisiko im Netz. Doch auch starke Passwörter können bei einem Datenleck oder einem Phishing-Angriff in...
Hacker nutzen Google Gemini zur Verstärkung von Angriffen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine Analyse hat gezeigt, dass Hacker bereits die Leistung offener KI-Systeme für Auskundschaftung, Fehlersuche im Code und Manipulation von Inhalten nutzen. Lesen...
39% of IT leaders fear major incident due to excessive workloads – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis 03 Feb 20256 mins IT SkillsIncident ResponseSecurity Operations Center IT leaders worry that ongoing staff shortages in the face of...
The CISO’s role in advancing innovation in cybersecurity – Source: www.csoonline.com
Source: www.csoonline.com – Author: Collaborating with startups, acting as advisors and supporting innovators are some of the ways security leaders can play their part in fostering...
Cybertrends 2025: KI-Cyberwaffen, Zero Days und gefördertes Chaos – Source: www.csoonline.com
Source: www.csoonline.com – Author: Anlässlich der Verlagerung von Konflikten in den Cyberraum könnten Unternehmen Opfer von Cyberwarfare werden. CISOs sollten sich vorbereiten. Im Jahr 2025 werden...
Download the Agentic AI Enterprise Spotlight – Source: us.resources.csoonline.com
Source: us.resources.csoonline.com – Author: Register Download the February 2025 issue of the Enterprise Spotlight from the editors of CIO, Computerworld, CSO, InfoWorld, and Network World. See...
General Motors Celebrates Long-Term Success With Hackers – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. General Motors has been engaged with HackerOne for seven years. Here’s what the team at General Motors had to say about...
Cyber Insights 2025: Quantum and the Threat to Encryption – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek’s Cyber Insights 2025 examines expert opinions on the expected evolution of more than a dozen areas of cybersecurity interest...
Hundreds of Thousands Hit by Data Breaches at Healthcare Firms in Colorado, North Carolina – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Asheville Eye Associates and Delta County Memorial Hospital District last week disclosed separate data breaches that impacted hundreds of thousands...
Casio Website Infected With Skimmer – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A threat actor has infected the website of Casio UK and 16 other victims with a web skimmer that altered...
DeepSeek Security: System Prompt Jailbreak, Details Emerge on Cyberattacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs China’s recently launched DeepSeek gen-AI continues to be analyzed by the cybersecurity community. While some researchers have found a jailbreak...
Insurance Company Globe Life Notifying 850,000 People of Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Insurance company Globe Life is notifying 850,000 individuals of a data breach that might have involved their personal, health, and...
1 Million Impacted by Data Breach at Connecticut Healthcare Provider – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Connecticut healthcare provider Community Health Center, Inc. (CHC) is notifying over one million individuals that their personal information was compromised...
2 officers bailed as anti-corruption unit probes data payouts to N Irish cops – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones The Police Service of Northern Ireland (PSNI) has bailed two officers after they were arrested as part of a fraud...
Privacy Commissioner warns the ‘John Smiths’ of the world can acquire ‘digital doppelgangers’ – Source: go.theregister.com
Source: go.theregister.com – Author: Simon Sharwood Australia’s privacy commissioner has found that government agencies down under didn’t make enough of an effort to protect data describing...
Medical monitoring machines spotted stealing patient data, users warned to pull the plug ASAP – Source: go.theregister.com
Source: go.theregister.com – Author: Brandon Vigliarolo Infosec in brief The United States Food and Drug Administration has told medical facilities and caregivers that monitor patients using...
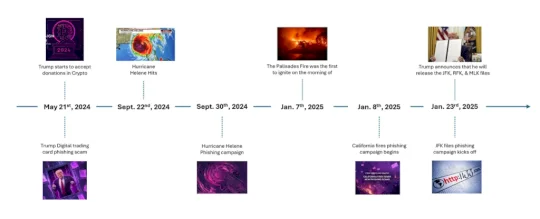
Hackers Hijack JFK File Release: Malware & Phishing Surge – Source: securityboulevard.com
Source: securityboulevard.com – Author: Veriti Research Veriti Research has uncovered a potentially growing cyber threat campaign surrounding the release of the declassified JFK, RFK, and MLK...
Core Features in NSFOCUS RSAS R04F04 1-2 – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS In the new NSFOCUS RSAS version R04F04, we optimized several core features and functions. In this post, we will focus on...
What does it mean to build in security from the ground up? – Source: go.theregister.com
Source: go.theregister.com – Author: Larry Peterson Systems Approach As my Systems Approach co-author Bruce Davie and I think through what it means to apply the systems...
Gilmore Girls fans nabbed as Eurocops dismantle two major cybercrime forums – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones Law enforcement officers across Europe assembled again to collectively disrupt major facilitators of cybercrime, with at least one of those...
Innovations in Identity and Access Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are IAM Innovations the Future of Cybersecurity? Identity and Access Management (IAM) has become instrumental in maintaining an effective cybersecurity...