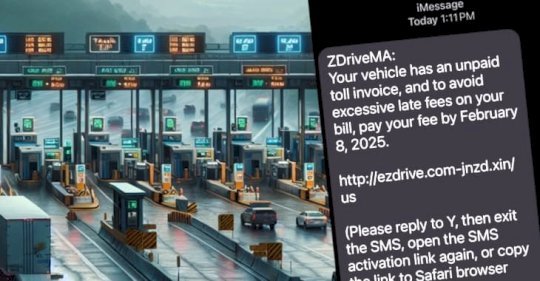
Source: www.bitdefender.com – Author: Graham Cluley North American drivers are continuing to be barraged by waves of scam text messages, telling them that they owe money...
Month: February 2025
Australians Hit With One Cyber Attack Every Second in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson A cyber attack hit an Australian user every second in 2024, marking a staggering twelvefold increase from the previous year....
How to Remove Your Saved Passwords in Chrome – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
MY TAKE: Securing the Internet of Everything: why self-healing devices are the next frontier – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido We’re just getting started down the road to the Internet of Everything (IoE.) Related: IoT growing at...
Why the Growing Risk of Cyber Inequity Threatens Critical Infrastructure – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Cyber inequity is a growing chasm that continues to separate organizations with robust cybersecurity and technology capabilities from those without....
Pairwise Authentication of Humans – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Here’s an easy system for two humans to remotely authenticate to each other, so they can be sure that neither...
Magecart Attackers Abuse Google Ad Tool to Steal Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Diana Vyshniakova via Alamy Stock Photo Attackers are exploiting Google Tag Manager by planting malicious code within...
Analyst Burnout Is an Advanced Persistent Threat – Source: www.darkreading.com
Source: www.darkreading.com – Author: William MacMillan Source: Brain light via Alamy Stock Photo COMMENTARY In the battle against cyber threats, we’re losing our most vital asset:...
So killen Sie NTLM – Source: www.csoonline.com
Source: www.csoonline.com – Author: NTLM ist aus Sicherheitsperspektive eine Katastrophe. Höchste Zeit, das Uralt-Protokoll für immer loszuwerden. Netzwerksicherheit und NTLM gehen nicht gut zusammen. PeopleImages.com –...
CISOs: Stop trying to do the lawyer’s job – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISOs are trained to fix problems. Lawyers are trained to find them. The two must work together to address complex challenges like...
PayPal Thanks Hackers with $1 Million in 7 Months on HackerOne – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. This blog post was written and contributed by Ray Duran on behalf of the PayPal security team. The security team for PayPal’s...
Building an Impenetrable Framework for Data Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why does the Secure Framework Matter? The focus of this operation isn’t just about the immediate prevention of potential threats...
Ensuring Satisfaction with Seamless Secrets Sprawl Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Properly Managing Your Non-Human Identities? Modern organizations are continually interacting with an ever-growing number of machines, applications, and...
Stay Relaxed with Top-Notch API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are Businesses Truly Aware of the Importance of Non-Human Identities in Cybersecurity? There’s one critical aspect that’s frequently overlooked: Non-Human...
DEF CON 32 – Exploiting Bluetooth From Your Car To The Bank Account – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Exploiting Bluetooth From Your Car To The Bank Account Authors/Presenters:...
UK Is Ordering Apple to Break Its Own Encryption – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier The Washington Post is reporting that the UK government has served Apple with a “technical capability notice” as defined by...
Secret Taliban records published online after hackers breach computer systems – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The Taliban government of Afghanistan is reeling after unidentified hackers successfully carried out a massive cyber attack against its computer...
How to Root Out Malicious Employees – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Malicious employees and insider threats pose one of the biggest security risks to organizations, as these users have more access...
Cyber Security in Customer Engagement: The Triple Defence Strategy – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team As digital interactions dominate modern communication, the rapid evolution of cyber threats demands robust security measures in customer engagement as...
Cloud Security Alliance Webinar Recap: Avoid the Breach with Shopify’s Andrew Dunbar – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. In this Cloud Security Alliance (CSA) fireside chat, Shopify’s VP of Security Engineering and IT sat down with HackerOne’s Luke Tucker...
HackerOne Praised By An Original Hacker – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. A hacker is “one who enjoys the intellectual challenge of creatively overcoming limitations.” No one exemplifies that definition like Steve Gibson,...
Navigating the New Frontier: Strengthening Cybersecurity Through Next-Gen Identity & Access Governance – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team It can be difficult to fully appreciate just what has changed when it comes to cybersecurity – and by how...
20% of Organizations Have Experienced a Non-Human Identity Security Incident – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Today’s business environment requires teams to do more — better than before, and at a faster rate. Thanks to third-party...
Justifying the Investment in Cloud Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Cloud Compliance Investment a Necessity? I often get asked, “Why is cloud compliance investment a necessity?” The answer...
Getting Better at Detecting Cyber Threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn A Question of Preparedness: How Prepared Are You In Detecting Cyber Threats? How confident are you in your organization’s ability...
Exciting Advances in Privileged Access Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why should we be excited about Privileged Access Management? Have you ever pondered the gravity of the implications of not...
DEF CON 32 – From Easy Wins To Epic Challenges: Bounty Hunter Edition – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Saturday, February 8, 2025 Home » Security Bloggers Network » DEF CON 32 – From Easy Wins To Epic Challenges:...
The Wall Street Journal: Lawmakers Push to Ban DeepSeek App From U.S. Government Devices – Source: securityboulevard.com
Source: securityboulevard.com – Author: mykola myroniuk Bipartisan Effort Seeks to Protect National Security Amid Concerns Over Chinese Data Collection WASHINGTON—A new bill set to be introduced...
Northland Power Cuts Vulnerability Management Time with Automation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore Innovation is a driving force in the world of renewable energy. For Northland Power, a global leader in power generation,...
How the Risk-Averse DoD Learned to Stop Worrying and Love the Hackers – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. There are few, if any, organizations more risk-averse than the U.S. Department of Defense. But even this staid agency has realized...