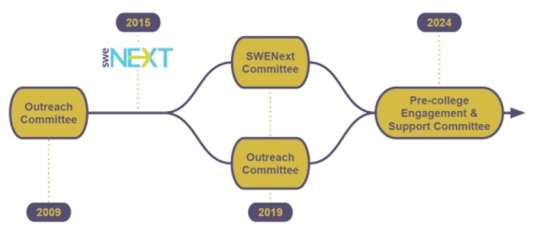
The newly named Pre-college Engagement & Support Committee will allow volunteers to focus on exploring strategic engagement of pre-college stakeholders, enhancing global growth, and kick-starting grassroots...
Day: February 21, 2025
Year in Review: SWENext High School Leadership Academy (SHLA)
With the FY24 SHLA program now at a close, SWE looks back on the sessions from this year. Source Views: 0
Two Unconventional Ways to Improve Your Public Speaking Skills
Yevheniia Trefilova shares personal experiences and actionable tips to help women in STEM improve their presentation skills. Source Views: 1
Developing the Leader Within Me Through ALWE
Dr. Jessica Ventura reflects on her experiences in SWE’s FY24 Academic Leadership for Women in Engineering (ALWE) Program. Source Views: 1
Finding Your “Why” Can Take You Places
Dr. Jayshree Seth and Dr. Amanda Diekman share how they bridged the industry-academia divide to develop resources that support women and minoritized individuals in STEM. Source...
Affinity Group Spotlight: LGBTQ+ and Allies Affinity Group
Each month throughout the year, we’ll be spotlighting a SWE Affinity Group. We are excited to highlight SWE’s LGBTQ+ & Allies Affinity Group! Source Views: 0
Ghost Ransomware Targets Orgs in 70+ Countries – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Google Adds Quantum-Resistant Digital Signatures to Cloud KMS – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
ZEST Security’s Cloud Risk Exposure Impact Report Reveals 62% of Incidents are Related to Risks Known to the Organization – Source: www.darkreading.com
Source: www.darkreading.com – Author: Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This website is...
When Brand Loyalty Trumps Data Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Paul Underwood Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Signs Your Organization’s Culture Is Hurting Your Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
CVE-2025-0108 Detection: Active Exploitation of an Authentication Bypass Palo Alto Networks PAN-OS Software – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk A recently patched firewall flaw in Palo Alto Networks PAN-OS, tracked as CVE-2025-0108, lets cybercriminals with network access to the...
Ghost (Cring) Ransomware Detection: The FBI, CISA, and Partners Warn of Increasing China-Backed Group’s Attacks for Financial Gain – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Increasing ransomware volumes, expanding hacker collectives, and record-breaking damage costs are redefining the cyber risk arena. The FBI, CISA, and...
Life in the Swimlane with Gabriella Lopez, Senior Sales Development Representative – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore Welcome to the “Life in the Swimlane” blog series. Here we will feature interviews with Swimlaners to learn more about...
Katie Arrington Appointed DoD CISO: What It Means for CMMC and the Defense Industrial Base – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sanjeev Verma Katie Arrington’s appointment as Chief Information Security Officer (CISO) of the U.S. Department of Defense (DoD) marks a pivotal moment...
Driving Innovation with Secure Cloud Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Innovation in Cybersecurity Crucial? An essential turn of the century question most organizations face is how they can...
Build a Confident Security Posture with Proven Tactics – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are Your Cybersecurity Tactics Building a Confident Security Posture? Have you ever wondered why certain organizations appear to have an...
Feel Empowered: Managing Access with Precision – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Access Management and NHIs: The Power Pairing in Cybersecurity? Managing access to sensitive data and systems is like navigating a...
How Page Protect Enabled Seamless PCI DSS 4.0 Compliance for a Leading Beverage Retailer – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paige Tester A leading online beverage retailer, known for offering an extensive selection of drinks from top retailers worldwide, processes thousands of...
48 Hours in the Trenches: The High-Stakes World of Incident Response – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lou Ardolino Okay, so this is all going to sound a bit dramatic, but it’s with good reason. I manage a cybersecurity...
DEF CON 32 – MicroHard More Like MicroEasy To Exploit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, February 20, 2025 Home » Security Bloggers Network » DEF CON 32 – MicroHard More Like MicroEasy To Exploit...
Early Trends in 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Enzoic Updates from Enzoic’s Threat Research Team A New Year Again Here we are halfway through February– seems like 2025 is really...
Achieving PCI DSS 4.0.1 Compliance for Companies (SAQ A-EP): A Comprehensive Guide for Feroot PCI PaymentGuard AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: mykola myroniuk In this article 1. Introduction Payment security for SAQ A-EP merchants has never been more critical. As e-commerce continues to...