Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Rob Crandall via Alamy Stock Photo NEWS BRIEF The US Cybersecurity and Infrastructure Security Agency...
Day: February 12, 2025
Data Leaks Happen Most Often in These States — Here’s Why – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Oleckii Mach via Alamy Stock Photo States are increasingly embracing data privacy regulation, and Kentucky,...
Salt Typhoon’s Impact on the US & Beyond – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michael McLaughlin, Jillian Cash, Kellen Carleton Source: vska via Alamy Stock Photo COMMENTARY The Chinese-linked hacking group Salt Typhoon recently was detected...
DeepSeek AI Fails Multiple Security Tests, Raising Red Flag for Businesses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Mundissima via Alamy Stock Photo Organizations might want to think twice before using the Chinese generative AI...
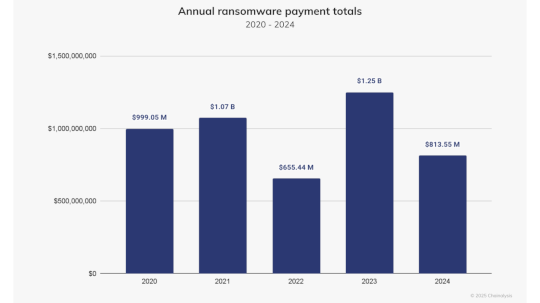
Ransomware Groups Made Less Money in 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: The total volume of ransom payments decreased year-over-year by approximately 35%, due to law enforcement activities and more victims refusing to pay,...
Product Update | Cloud Monitor + Content Filter – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexa Sander NEW! In Cloud Monitor: Policy Enhancements We’re thrilled to introduce our latest Cloud Monitor policy updates! We designed these enhancements...
Authorities Seize 8Base Ransomware Infrastructure, Arrest Four Russians – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Law enforcement agencies from more than a dozen countries in a joint operation arrested four people linked to the Russian-based...
The Current State of the CISO with Nick Kakolowski – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Nick Kakolowski, senior research director for IANS, dives into a survey done in conjunction with Artico Search on the current...
Enhancing IAM Security with AI Agents: A Strategic Approach by SecureFLO – Source: securityboulevard.com
Source: securityboulevard.com – Author: service Enhancing IAM Security with AI Agents: A Strategic Approach by SecureFLO Enhancing IAM Security with AI Agents: A Strategic Approach by...
Adam Khan on the Unique Security Challenges in Education IT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Adam Khan, vice president of global security operations for Barracuda Networks, explains what makes securing schools, such as universities, so...
Microsoft’s February 2025 Patch Tuesday Addresses 55 CVEs (CVE-2025-21418, CVE-2025-21391) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tenable Security Response Team 3Critical 52Important 0Moderate 0Low Microsoft addresses 55 CVEs with three rated critical and four zero-day vulnerabilities, including two...
Comic Agilé – Luxshan Ratnaravi, Mikkel Noe-Nygaard – #325 – Fixing the Bug – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the respected Software Engineering expertise of Mikkel Noe-Nygaard and the lauded Software Engineering / Enterprise Agile Coaching work of Luxshan Ratnaravi at Comic Agilé! Permalink *** This is a...
The Field Engineer’s Handbook: Configuring an Arista Networks Switch with Splunk – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jessi Clark Transform your network monitoring capabilities with the powerful combination of Arista Networks’ advanced telemetry and Splunk’s powerful analytics platform. This...
Navigating Firewall Security Policy Challenges in Technology Organizations: How FireMon Simplifies Complexity – Source: securityboulevard.com
Source: securityboulevard.com – Author: FireMon In the technology sector, innovation and agility are key drivers of success. Organizations in this field lead the charge in adopting...
Networks hosting botnet C&Cs: Same players, same problems – Source: securityboulevard.com
Source: securityboulevard.com – Author: The Spamhaus Team With every Botnet Threat Update we publish, the same networks consistently appear in the Top 20 for hosting botnet...
February Patch Tuesday: CISOs should act now on two actively exploited Windows Server vulnerabilities – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 11 Feb 20255 mins Threat and Vulnerability ManagementVulnerabilitiesWindows Security Also prioritize patches for vulnerabilities in LDAP and NTLM, as well as...
Authorities seize Phobos and 8Base ransomware servers, arrest 4 suspects – Source: www.csoonline.com
Source: www.csoonline.com – Author: An international law-enforcement collaboration has taken down two Russian nationals and two unidentified women in Thailand who ran Phobos ransomware affiliate platforms....
How to communicate clearly (and legally) during a cybersecurity crisis – Source: www.csoonline.com
Source: www.csoonline.com – Author: Trying to duck the consequences of a breach can be dangerous: better to quickly explain what you know and keep affected parties...
Hacker bringen falsche Rechnungen in Umlauf – Source: www.csoonline.com
Source: www.csoonline.com – Author: Ein Handelsunternehmen in Mecklenburg-Vorpommern wurde Ziel einer Cyberattacke. Infolgedessen wurden gefälschte Rechnungen im Namen der Firma verschickt. Hacker haben eine Handelsfirma in...
World Economic Forum Annual Meeting 2025: Takeaways, reflections, and learnings for the future – Source: www.csoonline.com
Source: www.csoonline.com – Author: While people, technology, and processes are crucial to enhancing cybersecurity, no individual or organization can have complete insight into all existing threats....
CSO Award and Hall of Fame Nominations Open Now – Source: www.csoonline.com
Source: www.csoonline.com – Author: Has your organization pioneered groundbreaking security initiatives that delivered real business value? If so, now is the time to showcase your achievements...
Hackerangriff auf LUP-Kliniken – Source: www.csoonline.com
Source: www.csoonline.com – Author: Zwei Standorte der LUP-Kliniken kämpfen aktuell mit technischen Problemen. Ursache ist eine Cyberattacke. Krankenhäuser geraten immer öfter in das Visier von Cyberkriminellen....
Over 12,000 KerioControl firewalls remain prone to RCE attacks amid active exploits – Source: www.csoonline.com
Source: www.csoonline.com – Author: While unpatched instances were reduced to half within a month, a huge number of them remain vulnerable even as attackers exploit the...
Why security leaders must ensure they have a recovery plan for Active Directory attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: Active Directory (AD) is an increasingly attractive target for cyber attacks. If AD is not properly protected, recovery from cyber incidents will...
Apple issues emergency patches to contain an ‘extremely sophisticated attack’ on targeted individuals – Source: www.csoonline.com
Source: www.csoonline.com – Author: A critical USB restriction flaw was addressed in an emergency iOS and iPadOS update. Apple has rolled out emergency security patches after...