Source: www.csoonline.com – Author: CISOs outline their goals for 2025, from leveraging AI for defense to ensuring swift recovery in the face of cyberattacks. As cyber...
Month: January 2025
7 fundamentale Cloud-Bedrohungen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Cloud-Sicherheitsrisiken zu ignorieren, geht nicht gut aus. Ganz besonders in diesen sieben Fällen. Dieser Artikel hilft, Unsicherheiten in Cloud-Umgebungen vorzubeugen. Foto: Roman...
Tenable Chairman and CEO Amit Yoran Has Died – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bridgett Paradise It is with profound sadness that we share the news of the passing of our beloved CEO Amit Yoran on...
Unlocking the Potential of Machine Identity Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are you aligning your cybersecurity efforts with the contemporary needs and trends? Organizations often overlook the significance and strategic depth...
Feel Supported by Advanced Machine Identity Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why Does Machine Identity Management Matter? Why should advanced machine identity management be a key concern for CISOs? With rapid...
How Reliable Secret Storage Enhances Cloud Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Effective Secret Storage So Crucial to Cloud Security? In an increasingly digitized world where every information is stored...
Threat Intelligence Hot Shots Part 3: Episodes 4-13 (Compilation) – Source: securityboulevard.com
Source: securityboulevard.com – Author: psilva This is Episode 4 of Threat Intelligence Hot Shots. Sr. Threat Intelligence Analyst, Alex Ryan, and Peter discuss the recent shutdown...
The Unemployed Chronicles: Learn from My Mistakes – Source: securityboulevard.com
Source: securityboulevard.com – Author: psilva I had rehearsed a whole opening for Episode 6 of The Unemployed: My Laid-Off Life but alas, I did not get...
The Unemployed Chronicles: A Lesson from My Laid Off Life – Source: securityboulevard.com
Source: securityboulevard.com – Author: psilva Welcome to Episode 4 of ‘The Unemployed: My Laid-Off Life.’ We’ve officially got a title for this journey! Today, I have...
Thanksgiving Gratitude & Job Hunt Updates for Episode 3 of, The Unemployed – Source: securityboulevard.com
Source: securityboulevard.com – Author: psilva Welcome to Week 3 of my Joblessness Journey—if you’re in the same boat, come on over! It’s Thanksgiving week, so take...
DEF CON 32 – RF Attacks on Aviation’s Defense Against Mid-Air Collisions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – RF Attacks on Aviation’s Defense Against Mid-Air Collisions Authors/Presenters: G....
Making FedRAMP ATOs Great with OSCAL and Components – Source: securityboulevard.com
Source: securityboulevard.com – Author: stackArmor OMB Memo M-24-15 published on July 24, 2024 directed GSA and the FedRAMP PMO to streamline the FedRAMP ATO process using...
Introducing the Hacker101 CTF – Source:www.hackerone.com
Source: www.hackerone.com – Author: Cody Brocious. Hacker101 is getting something brand new: our own Capture The Flag! For those who are unfamiliar, Capture The Flags (better...
The AWS Shared Responsibility Model: 3 Areas of Improvement to Make Today, Part 1 – Source:www.hackerone.com
Source: www.hackerone.com – Author: Justin Boyer. Migrating your digital assets to the cloud can seem overwhelming at times. But you’re not alone. AWS has done a...
Confidently Secure: Leveraging PAM for Enhanced Protections – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Harnessing Non-Human Identities Central to Your Cybersecurity Strategy? In the realm of information security, managing identities – whether...
Stay Assured: Critical Insights into Secrets Rotation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why Is Secrets Rotation a Critical Aspect of Cybersecurity? Isn’t it intriguing how an object as intangible as ‘information’ can...
DEF CON 32 – The Interplay between Safety and Security in Aviation Systems3 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Saturday, January 4, 2025 Home » Security Bloggers Network » DEF CON 32 – The Interplay between Safety and Security...
Privacy Roundup: Week 1 of Year 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avoid The Hack! This is a news item roundup of privacy or privacy-related news items for 29 DEC 2024 – 4 JAN...
The U.S. Marine Corps Resolves Nearly 150 Vulnerabilities Thanks to Hackers – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. “I think we found something good,” said hackers @sumlac, @teknogeek, and @johnny said to a member of the MARFORCYBER team at...
Friday Squid Blogging: Anniversary Post – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Critical Windows LDAP flaw could lead to crashed servers, RCE attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: LDAPNightmare: If December Patch Tuesday server updates have not yet been installed, it’s time to do so to avoid DoS or RCE...
US government sanctions Chinese cybersecurity company linked to APT group – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 03 Jan 20254 mins Advanced Persistent ThreatsGovernmentHacker Groups Integrity Tech has been accused of helping the advanced persistent threat group Flax...
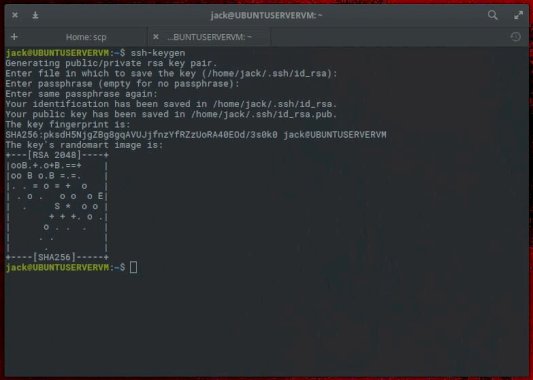
How To Use SCP (Secure Copy) With SSH Key Authentication – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
This Trusted App Helps Sluggish PCs Work Faster – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published January 3, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Thousands of Buggy BeyondTrust Systems Remain Exposed – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: artpartner-images.com via Alamy Stock Photo A remarkable number of BeyondTrust instances remain connected to the...
New HIPAA Cybersecurity Rules Pull No Punches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: MedStockPhotos via Alamy Stock Photo An unmitigated revamp of healthcare cybersecurity is coming in 2025, and experts...
Treasury Dept. Sanctions Chinese Tech Vendor for Complicity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: KB Photodesign via Shutterstock NEWS BRIEF The US Department of Treasury has sanctioned China-based cybersecurity...
Apple Offers $95M to Settle Siri Privacy Lawsuit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Bjanka Kadic via Alamy Stock Photo NEWS BRIEF Apple has agreed to pay a $95...
Why Small Businesses Can’t Rely Solely on AI to Combat Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Mutuski COMMENTARY As cybersecurity threats continue to surge, it has become crucial for small businesses to adopt proactive strategies to ensure...
Chrome Extension Compromises Highlight Software Supply Challenges – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Tada Images via Shutterstock On Christmas Eve, developers at data detection and response firm Cyberhaven received a...