Source: www.cyberdefensemagazine.com – Author: News team “Shift-left” is a familiar concept to CISOs and security practitioners across the globe. A term coined to promote the integration...
Month: January 2025
The Role of AI in Evolving Cybersecurity Attacks – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In the ever-expanding digital landscape, cybersecurity remains a critical concern for individuals, businesses, and governments alike. As technology advances, so...
A Guide for SMB Defense Contractors to Achieve CMMC Compliance – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The Department of Defense (DoD) created the Cybersecurity Maturity Model Certification (CMMC) program to defend the vast attack surface of the Defense...
Navigating the Security Risks and Efficiency Gains of GenAI in Healthcare – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team SaaS technology and artificial intelligence (AI) are revolutionizing patient care, drug development, and health and wellness practices. Today, AI processes...
Fight Fire with Fire: 3 Strategies to Defeat Deepfakes – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Generative AI deepfakes represent another skirmish in the ongoing clash between two forces that never stop innovating I was there...
The Common Goods and Shared Threats of the Software Supply Chain – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Perhaps the defining quality of the software supply chain is complexity. Amid the countless lines of code that the modern...
The AI Fix #32: Agentic AI, killer robot fridges, and the robosexual revolution – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 32 of The AI Fix, our hosts learn the meaning of “poronkusema”, Mark discovers his...
Improve Credential Sharing with Hacker Email Aliases – Source:www.hackerone.com
Source: www.hackerone.com – Author: Martijn Russchen. Starting today, all existing and new hackers get a personalized email alias tied to their account, in the form of...
How CISOs can forge the best relationships for cybersecurity investment – Source: www.csoonline.com
Source: www.csoonline.com – Author: Securing a cybersecurity investment isn’t just about crunching numbers — it’s about fostering cross-functional relationships. For CISOs, engaging key stakeholders will help...
Placebo- versus Nocebo-Effekt: Die Psychologie hinter der Security Awareness – Source: www.csoonline.com
Source: www.csoonline.com – Author: Während der Placebo-Effekt positive Erwartungshaltungen beschreibt, steht der Nocebo-Effekt für negative Erwartungen. Beides spielt bei den Security-Vorgaben eines Unternehmens bei den Mitarbeitenden...
The deepfake threat just got a little more personal – Source: www.csoonline.com
Source: www.csoonline.com – Author: Researchers at Google DeepMind and Stanford University have created highly effective AI replicas of more than 1,000 people based on simple interviews....
CyTwist Launches Advanced Security Solution to identify AI-Driven Cyber Threats in minutes – Source: www.csoonline.com
Source: www.csoonline.com – Author: CyTwist, a leader in advanced next-generation threat detection solutions, has launched its patented detection engine to combat the insidious rise of AI-generated...
Russian hackers turn trusted online stores into phishing pages – Source: www.csoonline.com
Source: www.csoonline.com – Author: The PhishWP WordPress plugin is well-equipped to turn legitimate shopping sites into phishing pages that capture sensitive payment and browser details. In...
Chinesische Hacker attackieren US-Finanzministerium – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 07 Januar 20254 Minuten Advanced Persistent ThreatsCyberangriffeHacker-Gruppen Schwachstellen in einer Remote-Support-Software haben es APT-Angreifern aus China erlaubt, in die Systeme des...
SWE Bengaluru Affiliate and Wabtec Corporation Bring AI to Life: Highlights from the AI in Engineering Summit
From inspiring keynotes to forward-looking panel discussions, find out what leaders are saying about the future of AI in engineering. Source Views: 2
Global Affiliate Spotlight: SWE Toronto
Get to know the inspiring events and wide-reaching impact of the SWE Toronto Affiliate. Source Views: 0
SWE’s Third Virtual Event in Mexico: Fostering Women’s Collaboration
Read the highlights from SWE’s Mexico’s third installment of their virtual event series, featuring keynotes, panel discussions, and networking. Source Views: 1
Reemployment Project: Meet Alex Ryan – Source: securityboulevard.com
Source: securityboulevard.com – Author: psilva The numbers are staggering—2024 has seen over 200,000 layoffs across 1,200 companies, with 82% coming from the tech industry. Welcome to...
Top Tech Talent Reemployment Project: Helping Job Seekers Shine! – Source: securityboulevard.com
Source: securityboulevard.com – Author: psilva After being let go from F5 in May 2023, I started thinking about how to support job seekers during tough times....
The Digital Battlefield: Understanding Modern Cyberattacks and Global Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author Imagine waking up one morning to find your city’s power grid has failed, hospitals can’t...
Challenges and Solutions in API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are Organizations Fully Grasping the Importance of API Security? It is surprising how often businesses underestimate the importance of Application...
The Role of IAM in Securing Cloud Transactions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why Is Identity Access Management (IAM) Crucial in Cloud Security? Have you ever thought about how crucial Identity Access Management...
DEF CON 32 – Psychic Paper: Making E-Ink Access Badges Accessible For Anyone – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Psychic Paper: Making E-Ink Access Badges Accessible For Anyone Author/Presenter:...
Compliance as cybersecurity: A reality check on checkbox risk management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Todd R. Weiss In the world of cybersecurity, compliance is a no-brainer. Adhering to corporate and regulatory compliance standards is critical for...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #319 – Specialities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, January 7, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Exabeam Extends Scope and Reach of SIEM Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Exabeam today added a bevy of capabilities to its New-Scale Security Operations Platform, including support for open application programming interface...
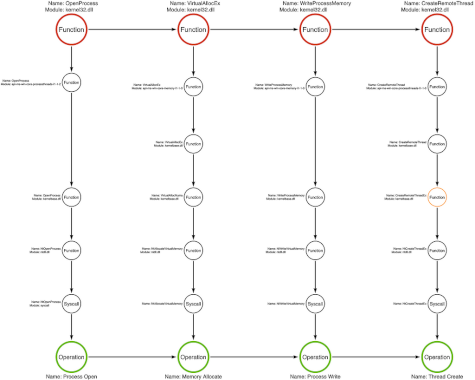
Part 15: Function Type Categories – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jared Atkinson On Detection: Tactical to Functional Seven Ways to View API Functions Introduction Welcome back to Part 15 of the On...
IVPN Review: Pricing, Features, Pros, and Cons – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jenna Phipps We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Sharing of Telegram User Data Surged After CEO Arrest – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Piotr Adamowicz via Alamy Stock Photo Before September 2024, policy of encrypted communications provider Telegram...
Pentagon Adds Chinese Gaming Giant Tencent to Federal Ban – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Cyberstock via Alamy Stock Photo NEWS BRIEF Chinese messaging and gaming giant Tencent has been...