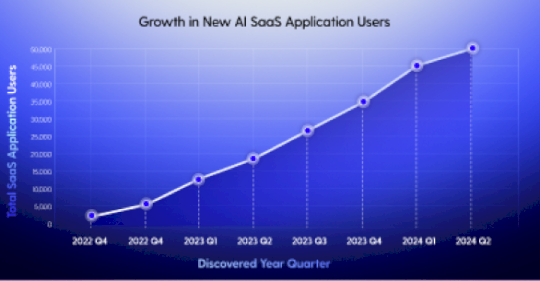
Source: securityboulevard.com – Author: Grip Security Blog Remember when we used ChatGPT to create cybersecurity haiku, dad jokes, and other whimsical tasks? Those days feel long...
Month: January 2025
Mobile Cybersecurity Trends for 2025: Key Predictions and Preparations – Source: securityboulevard.com
Source: securityboulevard.com – Author: George McGregor All the key players in cyber-security make predictions at the end of every year and 2025 is no exception, there...
Executive Order 14144 on Cybersecurity: Building on 2021’s Foundation with Advanced NHI Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dwayne McDaniel When President Biden signed Executive Order 14028 on Improving the Nation’s Cybersecurity on May 12, 2021, it marked a crucial...
Bluesky AT Protocol: Building a Decentralized TikTok – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author The Bluesky AT Protocol is designed as a federated social web protocol that emphasizes decentralization...
Privacy Roundup: Week 3 of Year 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avoid The Hack! This is a news item roundup of privacy or privacy-related news items for 12 JAN 2025 – 18 JAN...
Biden Signs New Cybersecurity Order – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier President Biden has signed a new cybersecurity order. It has a bunch of provisions, most notably using the US governments...
The 2025 Themes on Data GPS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Priyadarshi Prasad “God seems to know not only what we do but also what we think. Seems like a huge data privacy...
From Dark Web to Jackpot: How Cybercriminals Exploit Stolen Credentials in iGaming – Source: securityboulevard.com
Source: securityboulevard.com – Author: Artyom Buchkov In the rapidly evolving iGaming industry, platforms such as online casinos, sportsbooks and jackpot services have become prime targets for...
Information Security Manual (ISM) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deborah Erlanger What is the Information Security Manual (ISM)? The Information Security Manual (ISM) is a cybersecurity framework developed by the Australian...
So geht Tabletop Exercise – Source: www.csoonline.com
Source: www.csoonline.com – Author: Cybersecurity Tabletop Exercises bereiten Ihr Team auf den Ernstfall vor – insofern sie richtig aufgesetzt sind. Übung macht den Incident-Response-Meister. Foto: GaudiLab...
Cyberangriff auf Bundesdruckerei-Tochter – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Tochterfirma der Bundesdruckerei D-Trust wurde Ziel einer Cyberattacke. Dabei sind eventuell auch personenbezogene Daten abgeflossen. 2476561975 TippaPatt – Shutterstock.com Die D-Trust...
HPE’s sensitive data exposed in alleged IntelBroker hack – Source: www.csoonline.com
Source: www.csoonline.com – Author: The hacker is offering to sell stolen HPE source codes, private and public access keys and personally identifiable information (PIIs) of customers...
Ridding your network of NTLM – Source: www.csoonline.com
Source: www.csoonline.com – Author: The path to eradicating this ancient protocol and security sinkhole won’t be easy, but the time has come for its complete eradication....
MY TAKE: Here’s why Donald Trump really needs to fully embrace Joe Biden’s cybersecurity EO – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido As one of his final official acts, President Joe Biden issued a landmark directive, addressing the evolving...
Private Internet Access VPN Review: How Good Is PIA VPN? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Beyond Passwords: Transforming Access Security with Passwordless IAM – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Ever found yourself locked out of an account at the worst possibility? While rushing to meet a deadline or accessing...
7 Steps International Organizations Must Take to Defend Critical National Infrastructure – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Critical national infrastructure (CNI) is at risk in countries across the globe. When attackers target CNI systems—which include power plants,...
HTTP 1.1 Vs. HTTP 2: What Are the Differences? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team According to this recent report by McKinsey, 87% of consumers say they won’t do business with your company if they have concerns...
Name That Toon: Incentives – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner What motivates you? What will change how you do security? Send us a cybersecurity-related caption to describe the above scene...
US Ban on Automotive Components Could Curb Supply Chain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Hsyn20 via Shutterstock Smart-vehicle makers are facing supply chain disruption as the US Department of Commerce plans...
Phishing Attacks Are the Most Common Smartphone Security Issue for Consumers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Hollie Hennessy, Aaron West Source: Thomas Bethge via Alamy Stock Photo Highlights: Consumer survey shows that the most common security issues are...
Hackers Exploit AnyDesk Impersonating CERT-UA to Launch Cyber-Attacks – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Adversaries frequently leverage legitimate tools in their malicious campaigns. The popular AnyDesk remote utility has also been largely exploited by...
GitHub Embraces Hacker-Powered Security To Protect 55 Million Projects – Source:www.hackerone.com
Source: www.hackerone.com – Author: luke. We recently published The GitHub Bug Bounty Story and couldn’t be more excited to share it with you! TL;DR: Their lead...
How organizations can secure their AI code – Source: www.csoonline.com
Source: www.csoonline.com – Author: AI-generated code is surfacing everywhere, even in places where its use is officially banned. Here’s what cybersecurity leaders can do to ensure...
Midsize firms universally behind in slog toward DORA compliance – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis 20 Jan 20254 mins ComplianceFinancial Services IndustryRegulation The deadline for implementing the EU’s DORA has expired. How far have financial...
Diese Security-Technologien haben ausgedient – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Cybersicherheit entwickelt sich rasant weiter – insbesondere im KI-Zeitalter. Lesen Sie, welche Technologien und Methoden wegkönnen. Zeit für eine Frischzellenkur? JL_OFF...
DEF CON 32 – Exposing The Occultations In Large Off-Grid Solar Systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Exposing The Occultations In Large Off-Grid Solar Systems Authors/Presenters: Dan...
Legends of Music: Celebrating the Greatest Artists Across Generations Compilation – Source: securityboulevard.com
Source: securityboulevard.com – Author: psilva Adam Ant, AD Rock, Alan Parsons, Aldo Nova, Alex Lifeson, Andrew Gold, Angus Young, Barbra Streisand, Barry Gibb, Barry White, Benjamin...
Confident Cybersecurity: Essentials for Every Business – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are Businesses Truly Prepared for Today’s Cybersecurity Challenges? With the transition to a digital majority, company networks are continuously at...
Proactively Managing Cloud Identities to Prevent Breaches – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn What Role Does Proactive Handling of Cloud Identities Play in Avoiding Breaches? As cybersecurity experts, we are vested in the...