Source: www.darkreading.com – Author: Joan Goodchild Source: Marek Uliasz via Alamy Stock Photo For years, cybersecurity was frequently (and derisively) referred to as the “Department of...
Month: January 2025
GhostGPT: Uncensored Chatbot Used by Cyber Criminals for Malware Creation, Scams – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Security researchers have discovered a new malicious chatbot advertised on cybercrime forums. GhostGPT generates malware, business email compromise scams, and...
Smashing Security podcast #401: Hacks on the high seas, and how your home can be stolen under your nose – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content An Italian hacker makes the grade and ends up in choppy waters, and hear true stories of...
CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380 Detection: CISA and FBI Warn Defenders of Two Exploit Chains Using Critical Ivanti CSA Vulnerabilities – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Defenders shed light on a set of vulnerabilities in Ivanti Cloud Service Appliances (CSA) that can be chained for further...
The Cyber Resilience Act: How Manufacturers Can Meet New EU Standards and Strengthen Product Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Cybersecurity has become a leading priority for manufacturers of embedded systems and IoT devices. The rapid proliferation of these technologies,...
Trump Pardons Silk Road Founder Ulbricht – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Donald Trump has used his presidential powers to pardon convicted felon Ross Ulbricht, the founder of notorious dark web marketplace Silk Road....
PlushDaemon APT Targeted South Korean VPN Software – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A cyber espionage operation targeting South Korean VPN software was conducted in 2023 by a previously undocumented advanced persistent threat (APT) group,...
Tycoon 2FA Phishing Kit Upgraded to Bypass Security Measures – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new version of the phishing kit Tycoon 2FA, which uses advanced tactics to bypass multi factor authentication (MFA) and evade detection,...
UK Mail Check: DMARC Reporting Changes to Know – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Bowers The UK National Cyber Security Centre (NCSC), the country’s technical authority for cyber security, has announced changes to its Mail...
DEF CON 32 – The Village Peoples’ Panel What Really Goes On In A Village – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, January 22, 2025 Home » Security Bloggers Network » DEF CON 32 – The Village Peoples’ Panel What Really...
Life in the Swimlane with Marian Fehrenbacher, HR Assistant & Office Manager – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore Welcome to the “Life in the Swimlane” blog series. Here we will feature interviews with Swimlaners to learn more about...
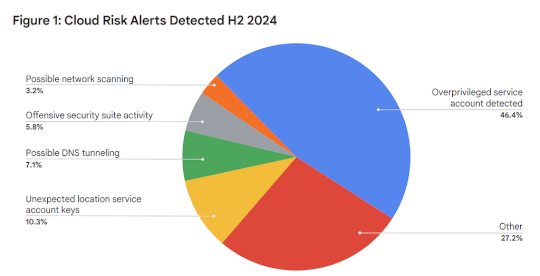
Google Cloud Security Threat Horizons Report #11 Is Out! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our next Threat...
Randall Munroe’s XKCD ‘Human Altitude’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Filtered to Perfection: Votiro’s Two-Layer Approach to Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro The Coffee-Making Process Meets Cybersecurity It’s early morning and you’re gearing up for a busy day. You grab your coffee pot,...
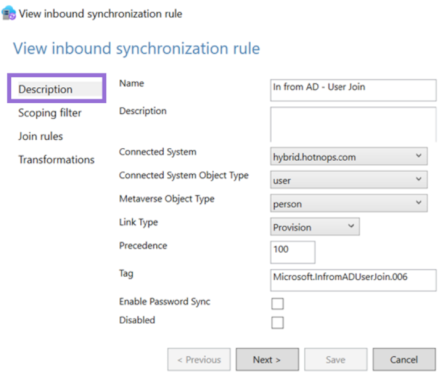
Entra Connect Attacker Tradecraft: Part 2 – Source: securityboulevard.com
Source: securityboulevard.com – Author: hotnops Now that we know how to add credentials to an on-premises user, lets pose a question: “Given access to a sync...
Rethinking Credential Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Enzoic A Candid Conversation with Enzoic’s CTO The digital landscape is evolving, and with it comes a wave of sophisticated attacks targeting...
DEF CON 32 – UDSonCAN Attacks Discovering Safety Critical Risks By Fuzzing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, January 22, 2025 Home » Security Bloggers Network » DEF CON 32 – UDSonCAN Attacks Discovering Safety Critical Risks...
How to Handle Secrets at the Command Line [cheat sheet included] – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dwayne McDaniel If developers all share one thing in common, it is their use of the command line to get their jobs...
FBI/CISA Share Details on Ivanti Exploits Chains: What Network Defenders Need to Know – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The US government’s cybersecurity and law enforcement agencies on Wednesday released technical details of at least two elaborate exploit chains...
DHS Disbands Cyber Safety Review Board, Ending One of CISA’s Few Bright Spots – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The Trump administration has removed all members from the Cyber Safety Review Board (CSRB), ending what some observers saw as...
Application Security Firm DryRun Raises $8.7 Million in Seed Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs DryRun Security on Wednesday announced raising $8.7 million in a seed funding round for its AI-powered application security solutions. The...
Doti AI Raises $7 Million Seed Funding for Instant Access to Internal Company Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Tel Aviv, Israel-based Doti AI has raised $7 million in seed funding led by F2 Venture Capital and angel investors...
Call for Presentations Open for SecurityWeek’s 2025 Supply Chain Security & Third-Party Risk Summit – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News The increasing frequency and severity of software supply chain attacks have sent shockwaves through the cybersecurity community. These incidents have...
Cyber Insights 2025: APIs – The Threat Continues – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek’s Cyber Insights 2025 examines expert opinions on the expected evolution of more than a dozen areas of cybersecurity interest...
Over $380,000 Paid Out on First Day of Pwn2Own Automotive 2025 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Trend Micro’s Zero Day Initiative (ZDI) has announced the results from the first day of the Pwn2Own Automotive 2025 hacking...
Murdoc Botnet Ensnaring Avtech, Huawei Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A new variant of the Mirai malware has been observed exploiting vulnerabilities in Avtech cameras and Huawei routers to ensnare...
Trump Overturns Biden Rules on AI Development, Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Andrey Popov via Alamy Stock Photo President Donald Trump revoked former President Joe Biden’s 2023...
Chinese Cyberspies Target South Korean VPN in Supply Chain Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: BeeBright via Shutterstock A newly discovered Chinese threat group has targeted a South Korean VPN developer with...
Trump Pardons ‘Silk Road’ Dark Web Drug Market Creator – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: White House Photo via Alamy Stock Photo NEWS BRIEF On just his second day in...
Will 2025 See a Rise of NHI Attacks? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Itzik Alvas Itzik Alvas, Co-Founder & CEO, Entro Security January 22, 2025 3 Min Read Source: Brain light via Alamy Stock Photo...









![how-to-handle-secrets-at-the-command-line-[cheat-sheet-included]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2025/01/156035-how-to-handle-secrets-at-the-command-line-cheat-sheet-included-source-securityboulevard-com.jpg)