Source: www.proofpoint.com – Author: Channel partners benefit from an unparalleled agile procurement process to strengthen their business opportunities and close deals faster SUNNYVALE, Calif., January 23,...
Day: January 23, 2025
Automating endpoint management doesn’t mean ceding control – Source: www.csoonline.com
Source: www.csoonline.com – Author: AEM can help solve persistent skills gaps, tool sprawl, and budget constraints. Beset with cybersecurity risks, compliance regimes, and digital experience challenges,...
Grohe AG mutmaßlich von Ransomware-Attacke betroffen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Cyber-Bande Ransomhub erpresst die Grohe AG mit gestohlenen Daten. Die Ransomware-Bande Ransomhub will 100 Gigabyte Daten von der Grohe AG erbeutet...
Cisco patches antivirus decommissioning bug as exploit code surfaces – Source: www.csoonline.com
Source: www.csoonline.com – Author: The flaw could allow remote attackers to shut down ClamAV scanning and compromise critical security workflows. Cisco has patched a denial-of-service (DoS)...
10 top XDR tools and how to evaluate them – Source: www.csoonline.com
Source: www.csoonline.com – Author: Extended detection and response tools provide a deeper and more automated means to identify and respond to threats. These are some of...
Python administrator moves to improve software security – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis 23 Jan 20255 mins The popular programming language has added a way to check for malware-laded packages. The administrators of...
Geben Sie LLM-Alarmismus keine Chance! – Source: www.csoonline.com
Source: www.csoonline.com – Author: Generative KI wird Cyberkriminellen keinen Vorteil verschaffen – im Gegenteil. Die Mär von der Cybercrime-KI-Revolution? Overearth | shutterstock.com Cybersicherheitsexperten haben in den...
Auswirkungen auf IT-Fachkräfte: 10 Anzeichen für einen schlechten CSO – Source: www.csoonline.com
Source: www.csoonline.com – Author: Sind Mitarbeiter motiviert und werden gefördert, arbeiten sie effektiver, auch in der IT-Security. Schlechte Stimmung kann an den Vorgesetzten liegen. Sind IT-Mitarbeiter...
Mastercard’s multi-year DNS cut-and-paste nightmare – Source: www.csoonline.com
Source: www.csoonline.com – Author: What is frightening about this mistake is not how much damage cyberthieves could have done, but how easy it is to make...
Third Interdisciplinary Workshop on Reimagining Democracy (IWORD 2024) – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Last month, Henry Farrell and I convened the Third Interdisciplinary Workshop on Reimagining Democracy (IWORD 2024) at Johns Hopkins University’s...
CISA: Ivanti Vulns Chained Together in Cyberattack Onslaught – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Kristoffer Tripplaar via Alamy Stock Photo NEWS BRIEF Cyberattackers are using a new threat vector...
The Security Risk of Rampant Shadow AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Anuj Jaiswal Anuj Jaiswal, Chief Product Officer, Fortanix January 23, 2025 3 Min Read Source: LuckyStep48 via Alamy Stock Vector COMMENTARY The...
Black ‘Magic’ Targets Enterprise Juniper Routers With Backdoor – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: LJSphotography via Alamy Stock Photo Dozens of organizations have been infected with router malware that uses a...
Doti AI Launches Platform to Securely Find Enterprise Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: YAY Media AS via Alamy Stock Photo NEWS BRIEF All organizations, regardless of size or industry, are experiencing...
Security Needs to Start Saying ‘No’ Again – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild Source: Marek Uliasz via Alamy Stock Photo For years, cybersecurity was frequently (and derisively) referred to as the “Department of...
GhostGPT: Uncensored Chatbot Used by Cyber Criminals for Malware Creation, Scams – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Security researchers have discovered a new malicious chatbot advertised on cybercrime forums. GhostGPT generates malware, business email compromise scams, and...
Smashing Security podcast #401: Hacks on the high seas, and how your home can be stolen under your nose – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content An Italian hacker makes the grade and ends up in choppy waters, and hear true stories of...
CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380 Detection: CISA and FBI Warn Defenders of Two Exploit Chains Using Critical Ivanti CSA Vulnerabilities – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Defenders shed light on a set of vulnerabilities in Ivanti Cloud Service Appliances (CSA) that can be chained for further...
The Cyber Resilience Act: How Manufacturers Can Meet New EU Standards and Strengthen Product Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Cybersecurity has become a leading priority for manufacturers of embedded systems and IoT devices. The rapid proliferation of these technologies,...
Trump Pardons Silk Road Founder Ulbricht – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Donald Trump has used his presidential powers to pardon convicted felon Ross Ulbricht, the founder of notorious dark web marketplace Silk Road....
PlushDaemon APT Targeted South Korean VPN Software – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A cyber espionage operation targeting South Korean VPN software was conducted in 2023 by a previously undocumented advanced persistent threat (APT) group,...
Tycoon 2FA Phishing Kit Upgraded to Bypass Security Measures – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new version of the phishing kit Tycoon 2FA, which uses advanced tactics to bypass multi factor authentication (MFA) and evade detection,...
UK Mail Check: DMARC Reporting Changes to Know – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Bowers The UK National Cyber Security Centre (NCSC), the country’s technical authority for cyber security, has announced changes to its Mail...
DEF CON 32 – The Village Peoples’ Panel What Really Goes On In A Village – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, January 22, 2025 Home » Security Bloggers Network » DEF CON 32 – The Village Peoples’ Panel What Really...
Life in the Swimlane with Marian Fehrenbacher, HR Assistant & Office Manager – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore Welcome to the “Life in the Swimlane” blog series. Here we will feature interviews with Swimlaners to learn more about...
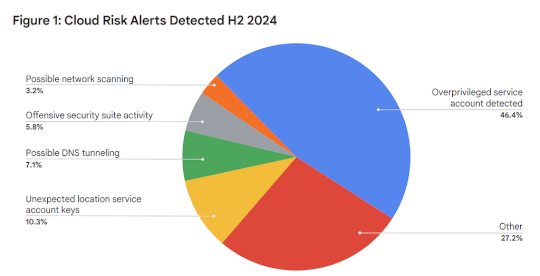
Google Cloud Security Threat Horizons Report #11 Is Out! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our next Threat...
Randall Munroe’s XKCD ‘Human Altitude’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Filtered to Perfection: Votiro’s Two-Layer Approach to Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro The Coffee-Making Process Meets Cybersecurity It’s early morning and you’re gearing up for a busy day. You grab your coffee pot,...
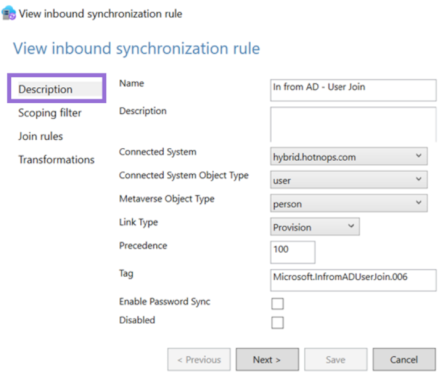
Entra Connect Attacker Tradecraft: Part 2 – Source: securityboulevard.com
Source: securityboulevard.com – Author: hotnops Now that we know how to add credentials to an on-premises user, lets pose a question: “Given access to a sync...
Rethinking Credential Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Enzoic A Candid Conversation with Enzoic’s CTO The digital landscape is evolving, and with it comes a wave of sophisticated attacks targeting...