Source: www.hackerone.com – Author: luke. One of the top IT research and advisory companies, 451 Research, recently authored a new “pathfinder report” advising decision-makers on the...
Day: January 18, 2025
Key Findings From The Hacker-Powered Security Report: Security Responsiveness is Improving (2 of 6) – Source:www.hackerone.com
Source: www.hackerone.com – Author: luke. With hacker-powered security, it’s critical to open and maintain a line of communication with the hackers who are working to find...
Has the TikTok Ban Already Backfired on US Cybersecurity? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Roykas Tenys via Alamy Stock Photo Now that the US Supreme Court has upheld a...
Employees Enter Sensitive Data Into GenAI Prompts Far Too Often – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Marcos Alvarado via Alamy Stock Photo A wide spectrum of data is being shared by...
15K Fortinet Device Configs Leaked to the Dark Web – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: JHVEPhoto via Alamy Stock Photo Dated configuration data and virtual private network (VPN) credentials for 15,474 Fortinet...
US Sanctions Chinese Hacker & Firm for Treasury, Critical Infrastructure Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Trek and Shoot via Alamy Stock Photo NEWS BRIEF The Department of the Treasury’s Office...
Secure AI? Dream on, says AI red team – Source: www.infoworld.com
Source: www.infoworld.com – Author: Microsoft’s ethical AI hackers provide some answers — as well as more questions. The group responsible for red teaming of over 100...
US hits back against China’s Salt Typhoon group – Source: www.csoonline.com
Source: www.csoonline.com – Author: Experts welcome economic sanctions against gang believed to be behind telecom hacks, but warn tougher action is needed. The US is hitting...
DORA-Umsetzung hält Banken-CISOs auf Trab – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Frist für die Umsetzung der EU-Verordnung DORA ist abgelaufen. Doch wie weit sind die Finanzdienstleister? Finanzunternehmen müssen seit heute die neuen...
Poor patching regime is opening businesses to serious problems – Source: www.csoonline.com
Source: www.csoonline.com – Author: About 70% of organizations did not regularly patch flaws in their internet-facing systems, according to an S&P Global Ratings report. Vulnerability remediation...
US Government Agencies Call for Closing the Software Understanding Gap – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The cybersecurity agency CISA and other government agencies are calling to action for the US to take the necessary steps...
In Other News: Lawsuits and Settlements, CrowdStrike Phish, MITRE’s D3FEND 1.0 – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy stories that might have slipped under the radar. We provide...
Wolf Haldenstein Data Breach Impacts 3.4 Million People – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Law firm Wolf Haldenstein Adler Freeman & Herz LLP is notifying more than 3.4 million individuals that their personal information...
Google Releases Open Source Library for Software Composition Analysis – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google on Thursday announced the release of OSV-SCALIBR (Software Composition Analysis LIBRary), an open source library for software composition analysis....
US Announces Sanctions Against North Korean Fake IT Worker Network – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Department of the Treasury’s Office of Foreign Assets Control (OFAC) on Thursday announced sanctions against two individuals and...
Industry Reactions to Biden’s Cybersecurity Executive Order: Feedback Friday – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs President Joe Biden this week issued an executive order aimed at strengthening the United States’ cybersecurity and making it easier...
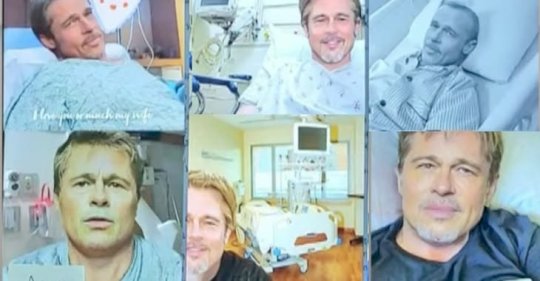
No, Brad Pitt isn’t in love with you – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley For Anne, a French woman in her fifties, things began innocently enough in early 2023. The interior designer, who had...
Q&A With @MalwareTechBlog – Source:www.hackerone.com
Source: www.hackerone.com – Author: luke. When he’s not reverse engineering malware, Marcus Hutchins (aka @MalwareTechBlog) can be found surfing, partying, or traveling. That’s to be expected...
SWE Mid-Career Professionals Affinity Group: Growing Your Career and Network Through SWE Mentoring
As part of their spotlight month, the Mid-Career Professionals AG describes how SWE members dealing with career breaks, job loss, family planning, relocations, or career transitions...
Fitness as a Professional Development Tool
As part of their spotlight month, the Early Career Professionals AG discusses the importance of fitness for field engineers, including three key benefits it offers to...
Exciting Changes to SWE’s Advance Learning Center!
SWE is thrilled to announce a new and improved Advance Learning Center (ALC) designed to help you find exactly what you need, when you need it....
Friday Squid Blogging: Opioid Alternatives from Squid Research – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Friday Squid Blogging: Opioid Alternatives from Squid Research Is there nothing that squid research can’t solve? “If you’re working with...
Social Engineering to Disable iMessage Protections – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier I am always interested in new phishing tricks, and watching them spread across the ecosystem. A few days ago I...
Growing Enterprise Data is Creating Big Cybersecurity Risk – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Buzz about big data permeated tech conversations in the mid-1990s, but people today don’t talk as much about big data...
Exploring the Vishing Threat Landscape – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Voice phishing, also known as vishing, represents a growing threat to organizations worldwide. Keepnet’s 2024 Vishing Response Report illuminates the...
How Can Generative AI be Used in Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Mata Generative AI is reshaping cybersecurity by providing advanced threat detection, automation, and data analysis capabilities. However, as generative AI evolves,...
GUEST ESSAY: President Biden’s cybersecurity executive order is an issue of national security – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Jonathan Gill President Biden’s detailed executive order relating to cybersecurity is great to see. Biden’s order reflects the importance of...
DEF CON 32 – Bypass 101 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » DEF CON 32 – Bypass 101 by Marc Handelman on January...
The Comprehensive Guide to Understanding Grok AI: Architecture, Applications, and Implications – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author Grok AI continues to evolve in both scale and capability, bolstered by recent funding of...
Back to the Basics For 2025: Securing Your Business – Source: securityboulevard.com
Source: securityboulevard.com – Author: hmeyers January 17, 2025 Gary Perkins, CISO at CISO Global Cybersecurity may seem complex, but it boils down to consistent implementation of...