Source: www.hackerone.com – Author: luke. Our Hacker-Powered Security Report is so chock-full of compelling insights, interesting tidbits, and surprising stats that we decided to distill them...
Day: January 17, 2025
GUEST ESSAY: President Biden’s cybersecurity executive order is an issue of national security – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido President Biden’s detailed executive order relating to cybersecurity is great to see. Biden’s order reflects the importance of cybersecurity at the...
Mercedes-Benz Head Unit security research report – Source: securelist.com
Source: securelist.com – Author: Kaspersky Security Services Introduction This report covers the research of the Mercedes-Benz Head Unit, which was made by our team. Mercedes-Benz’s latest...
Leveraging Behavioral Insights to Counter LLM-Enabled Hacking – Source: www.darkreading.com
Source: www.darkreading.com – Author: Aybars Tuncdogan, Oguz A. Acar COMMENTARY Hacking is innovation in its purest form. Like any other innovation, a successful hack requires developing...
Russian APT Phishes Kazakh Gov’t for Strategic Intel – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Daniren via Alamy Stock Photo A suspected Russia-nexus threat actor has been executing convincing spear phishing attacks...
EU’s DORA could further strain cybersecurity skills gap – Source: www.csoonline.com
Source: www.csoonline.com – Author: As the EU’s Digital Operational Resilience Act comes into force, financial sector firms, especially smaller ones, may face resources constraints, adding pressure...
Was ist ein Payload? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Kein Cyberangriff ohne Payload. Doch was genau meint der Begriff, welche Arten gibt es und wie lassen sich böswillige Nutzlasten erkennen und...
Millions of tunneling hosts are vulnerable to spoofing, DDoS attacks, say researchers – Source: www.csoonline.com
Source: www.csoonline.com – Author: The solution: Use IPsec and similar security protocols to protect against exploitation by threat actors. There are more than 4 million vulnerable...
How do you unlock automation within IT security and IT operations? – Source: www.csoonline.com
Source: www.csoonline.com – Author: IT ops and security teams are overwhelmed by spiraling complexity, falling further and further behind as their organizations try to scale endpoint...
Biden White House goes all out in final, sweeping cybersecurity order – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis 16 Jan 20258 mins Data and Information SecurityGovernmentSecurity Practices The ambitious final executive order requires 52 agency actions to bolster...
Vulnerabilities in SimpleHelp Remote Access Software May Lead to System Compromise – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Vulnerabilities in the SimpleHelp remote access software are trivial to exploit and could allow attackers to compromise the server and...
Cisco Unveils New AI Application Security Solution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Cisco this week unveiled AI Defense, a new solution designed to help enterprises secure the development and use of AI...
Russian Cyberspies Caught Spear-Phishing with QR Codes, WhatsApp Groups – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Microsoft researchers have uncovered Russian intelligence agencies using spear-phishing tactics to target victims with QR codes and WhatsApp group chats....
Millions of Internet Hosts Vulnerable to Attacks Due to Tunneling Protocol Flaws – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs New research shows that over 4 million systems on the internet, including VPN servers and home routers, are vulnerable to...
Wultra Raises €3 Million for Post-Quantum Authentication – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Authentication solutions startup Wultra on Wednesday announced raising €3 million (~$3.1 million) in seed funding for its post-quantum technology. Tensor...
380,000 Impacted by Data Breach at Cannabis Retailer Stiiizy – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire California-based cannabis brand Stiiizy is notifying 380,000 individuals that their personal information was compromised in a data breach at one...
North Korean Hackers Targeting Freelance Software Developers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire North Korean hackers are targeting the software supply chain in a new campaign aimed at developers looking for freelance Web3...
Cyber Insights 2025: Identities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek’s Cyber Insights 2025 examines expert opinions on the expected evolution of more than a dozen areas of cybersecurity interest...
Cybersecurity: How to Involve People in Risk Mitigation – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Cybersecurity: how to involve people in risk mitigation Cefriel presented the white paper “Cyber Security and the Human Element”, an...
SWARM: Pioneering The Future of Autonomous Drone Operations and Electronic Warfare – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Modern unmanned technologies are experiencing rapid growth, encompassing both civilian and military applications. Autonomous vehicles, delivery drones, and unmanned aerial...
CVE-2024-55591 Detection: Critical Zero-Day Vulnerability in Fortinet FortiOS and FortiProxy Actively Exploited in the Wild – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk This week, over 700 new vulnerabilities have been identified, continuing the trend of rising security risks for organizations worldwide. Among...
Watch WE24’s Keynote Presentations and Q&A
At this year’s WE24 conference, we sat down with all three of the keynote speakers after their presentations for a quick Q&A. Source Views: 0
Smashing Security podcast #400: Hacker games, AI travel surveillance, and 25 years of IoT – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content The video game Path of Exile 2 suffers a security breach, we explore the issues of using...
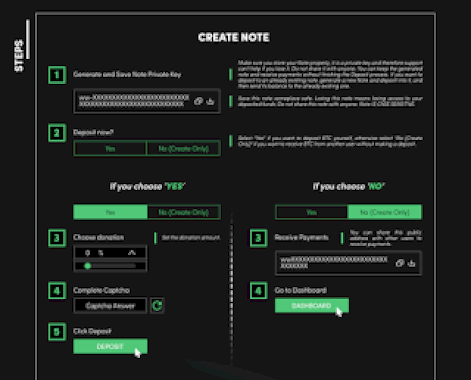
A Peek Inside the Current State of BitCoin Mixers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dancho Danchev Dear blog readers, In this post I’ll provide some actionable intelligence on the current state of active BitCoin Mixers landscape...
A Peek Inside the Current State of BitCoin Exchanges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dancho Danchev Dear blog readers, In this post I’ll provide some actionable intelligence on the current state of active BitCoin Exchanges landscape...
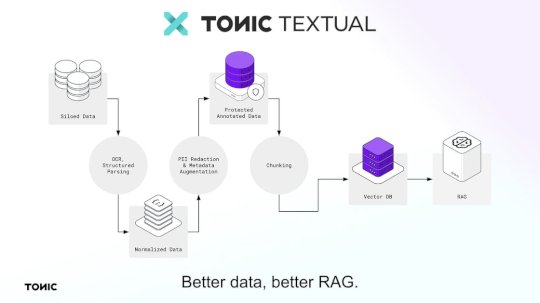
Test your apps with high-fidelity, production-like data with Release and Tonic – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog Guest post: the following article was written by Release CTO and co-founder Erik Landerholm....
Tonic.ai product updates: July 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog We’re excited to share the latest updates and announcements designed to improve your...
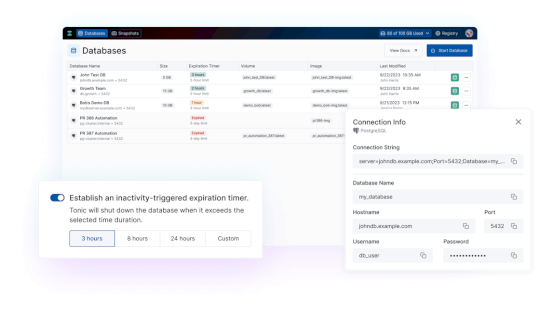
Tonic.ai product updates: March 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog We’re excited to share the latest product updates and announcements designed to improve...
Tonic.ai product updates: February 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog We’re excited to share the latest product updates and announcements designed to improve...
Tonic.ai product updates: April 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog We’re excited to share the latest updates and announcements designed to improve your...