Source: www.techrepublic.com – Author: Guest Contributor We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Day: January 16, 2025
CyberGhost VPN Review (2025): Features, Pricing, and Security – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares CyberGhost VPN fast facts Our rating: 4.3 stars out of 5 Pricing: Starts at $6.99 per month (6-month plan) Key...
Attackers Hijack Google Advertiser Accounts to Spread Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Primakov via Shutterstock In an especially brazen tactic, multiple threat actors are impersonating Google Ads login pages...
CISA: Second BeyondTrust Vulnerability Added to KEV Catalog – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: ktdesign via Adobe Stock NEWS BRIEF The Cybersecurity and Infrastructure Security Agency (CISA) is urging...
Extension Poisoning Campaign Highlights Gaps in Browser Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: VS148 via Shutterstock A Christmas Eve phishing attack resulted in an unknown party taking over a Cyberhaven...
North Korea’s Lazarus APT Evolves Developer-Recruitment Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: DD Images via Shutterstock North Korea’s Lazarus threat group has launched a fresh wave of attacks targeting...
OWASP’s New LLM Top 10 Shows Emerging AI Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: Matias Madou Matias Madou, Co-Founder & CTO, Secure Code Warrior January 15, 2025 5 Min Read Source: Nils Ackermann via Alamy Stock...
1Password’s Trelica Buy Part of Broader Shadow IT Play – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz 1Password’s acquisition of software-as-a-service (SaaS) access management provider Trelica is the latest move in a race to broaden the scope...
7 Essential Security Operations Center Tools for 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore Equipping your security operations center (SOC) team with the right tools is essential to their success. Without the right tools,...
News alert: Aembit announces speakers for NHIcon event, highlighting non-human identity security – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Silver Spring, MD, Jan. 15, 2025, CyberNewswire — Aembit, the non-human identity and access management (IAM) company, unveiled the full agenda...
News alert: Sweet Security’s LLM-powered detection engine reduces cloud noise to 0.04% – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Tel Aviv, Israel, Jan. 15, 2025, CyberNewswire — Sweet Security, a leader in cloud runtime detection and response, today announced the...
News alert: Wultra secures €3M funding to help financial firms mitigate coming quantum threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Prague, Czech Republic, Jan. 15, 2025, CyberNewswire — Quantum computing is set to revolutionize technology, but it also presents a significant...
DEF CON 32 – Small Satellite Modeling and Defender Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, January 15, 2025 Home » Security Bloggers Network » DEF CON 32 – Small Satellite Modeling and Defender Software...
FBI Deletes PlugX Malware From Computers Infected by China Group – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The FBI, with the help of French law enforcement and a private cybersecurity company, deleted a version of the PlugX...
Protecting the software supply chain: Insights from our expert panel – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens As software grows increasingly complex, ensuring the security of your software supply chain remains a critical priority. *** This is...
Randall Munroe’s XKCD ‘Chess Zoo’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Allstate Violates Drivers’ Privacy, Texas AG Alleges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings “We will hold all these companies accountable,” rants state attorney general Ken Paxton (pictured). Texas fires the next shot in lawmakers’ war...
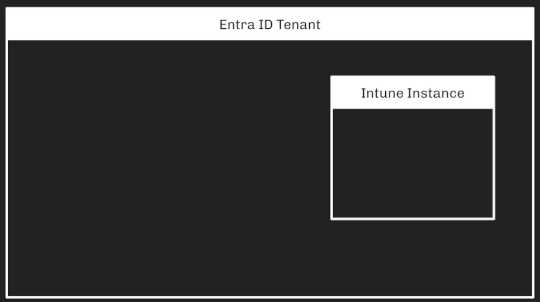
Intune Attack Paths — Part 1 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Robbins Intune Attack Paths — Part 1 Prior Work Several people have recently produced high-quality work around Intune tradecraft. I want to specifically mention:...
The AI Fix #33: AI’s deliberate deceptions, and Elon’s “unhinged” mode – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 33 of The AI Fix, our hosts watch a robot fall over, ChatGPT demonstrates that...