Source: www.hackerone.com – Author: johnk. “I think we found something good,” said hackers @sumlac, @teknogeek, and @johnny said to a member of the MARFORCYBER team at...
Day: January 4, 2025
Friday Squid Blogging: Anniversary Post – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Critical Windows LDAP flaw could lead to crashed servers, RCE attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: LDAPNightmare: If December Patch Tuesday server updates have not yet been installed, it’s time to do so to avoid DoS or RCE...
US government sanctions Chinese cybersecurity company linked to APT group – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 03 Jan 20254 mins Advanced Persistent ThreatsGovernmentHacker Groups Integrity Tech has been accused of helping the advanced persistent threat group Flax...
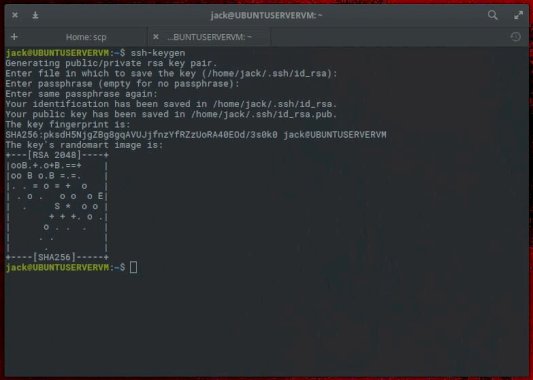
How To Use SCP (Secure Copy) With SSH Key Authentication – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
This Trusted App Helps Sluggish PCs Work Faster – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published January 3, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Thousands of Buggy BeyondTrust Systems Remain Exposed – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: artpartner-images.com via Alamy Stock Photo A remarkable number of BeyondTrust instances remain connected to the...
New HIPAA Cybersecurity Rules Pull No Punches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: MedStockPhotos via Alamy Stock Photo An unmitigated revamp of healthcare cybersecurity is coming in 2025, and experts...
Treasury Dept. Sanctions Chinese Tech Vendor for Complicity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: KB Photodesign via Shutterstock NEWS BRIEF The US Department of Treasury has sanctioned China-based cybersecurity...
Apple Offers $95M to Settle Siri Privacy Lawsuit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Bjanka Kadic via Alamy Stock Photo NEWS BRIEF Apple has agreed to pay a $95...
Why Small Businesses Can’t Rely Solely on AI to Combat Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Mutuski COMMENTARY As cybersecurity threats continue to surge, it has become crucial for small businesses to adopt proactive strategies to ensure...
Chrome Extension Compromises Highlight Software Supply Challenges – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Tada Images via Shutterstock On Christmas Eve, developers at data detection and response firm Cyberhaven received a...
Feel Relieved: Advanced Secrets Management Techniques – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Could Advanced Secrets Management be Your Way to Feeling Relieved? Think about it. If you could significantly decrease the likelihood...
Ensure Your Data’s Safety: Best Practices in Cloud Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Where Does Your Cloud Security Stand? Does your organization’s data management strategy consider non-human identities (NHIs) and secret security management?...
Imperva’s Wildest 2025 AppSec Predictions – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Holmes Humans are spectacularly bad at predicting the future. Which is why, when someone appears to be able to do it...
DEF CON 32 – The Past, Present, and Future of Bioweapons – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – The Past, Present, and Future of Bioweapons Authors/Presenters: Lucas Potter,...
Best of 2024: If You are Reachable, You Are Breachable, and Firewalls & VPNs are the Front Door – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richard Stiennon This year has witnessed a string of critical vulnerabilities in VPNs and firewalls, spanning many of the major vendors. Recently,...
Looking into 2025: Reflections & Observations from the Tidal Cyber Founders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tidal Cyber We want to wish you a Happy New Year! If you’re like us, the arrival of a new year is...
Randall Munroe’s XKCD ‘Time Capsule Instructions’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Friday, January 3, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
DEF CON 32 – You Got A Lighter I Need To Do Some Electroporation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – You Got A Lighter I Need To Do Some Electroporation...
Clarification on Shor’s Algorithm and GNFS Comparison – Source: securityboulevard.com
Source: securityboulevard.com – Author: Satyam Tyagi Some of our astute readers noticed an apparent anomaly in the graph comparing the complexities of Shor’s algorithm and GNFS...
Addressing PKI Management Pitfalls: From Chaos to Clarity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ashish Kumar Effective Public Key Infrastructure (PKI) management needs to combine ways of handling PKI infrastructure along with the recommended best practices....