Source: securityboulevard.com – Author: Jeffrey Burt Palo Alto Network’s cybersecurity recently outlined two vulnerabilities it found in Google Kubernetes Engine (GKE) that, individually, don’t represent much...
Year: 2024
Google Cloud Report Spotlights 2024 Cybersecurity Challenges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard As the New Year dawns, a cybersecurity report from Google Cloud suggests that while there are many challenges ahead, it...
GUEST ESSAY: Leveraging DevSecOps to quell cyber risks in a teeming threat landscape – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Yuga Nugraha In today’s digital landscape, organizations face numerous challenges when it comes to mitigating cyber risks. The constant evolution...
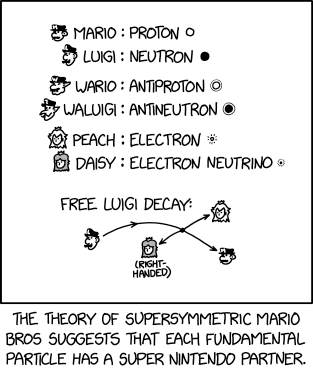
Randall Munroe’s XKCD ‘Supersymmetry’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
What is Security Posture? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire Security posture is a term often mentioned in cybersecurity, with businesses often told to improve or maintain a robust security...
Exploiting an API with Structured Format Injection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dana Epp Never trust user input. It’s been the mantra for years in popular secure coding books. Yet, even today, we continue...
Google Whistles While OAuth Burns — ‘MultiLogin’ 0-Day is 70+ Days Old – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Infostealer scrotes having a field day with unpatched vulnerability. A zero-day vulnerability, publicly revealed in October, is still unpatched. Google’s...
Top 5 Cyber Predictions for 2024: A CISO Perspective – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepen Desai Amidst the ever-evolving realm of enterprise security, a new year unfolds, introducing a dynamic array of emerging threats. While the...
State AG Hits Hospital With $300K Fine for Web Tracker Use – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Healthcare , HIPAA/HITECH NewYork-Presbyterian Disabled Website, Patient Portal Trackers in 2022 Marianne Kolbasuk McGee (HealthInfoSec) •...
European Central Bank to Put Banks Through Cyber Stress Test – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Finance & Banking , Governance & Risk Management , Industry Specific 109 Banks to Participate in Simulated Cyberattacks to Assess Cyber...
Merry ‘Leaksmas’! Hackers Give Away 50 Million Pieces of PII – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Holiday Leaks Could Result in More Digital Identity Theft and...
LockBit 3.0 Claims Attack on Australian Auto Dealer Eagers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Fraud Management & Cybercrime , Ransomware Eagers Says It Doesn’t Know Full Extent of Hack But Has Started...
Cybercriminals Share Millions of Stolen Records During Holiday Break – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Anucha Cheechang via Shutterstock Cybercriminals collectively leaked some 50 million records containing sensitive personal information in the...
Google Settles Lawsuit Over Tracking ‘Incognito Mode’ Chrome Users – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Tim Walton via Alamy Stock Photo Google is settling a class-action lawsuit over how it tracks data...
Cyberattackers Target Nuclear Waste Company via LinkedIn – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Alekesey Zotov via Alamy Stock Photo Last week, a group of hackers targeted Radioactive Waste Management (RWM), a...
Israel Battles Spike in Wartime Hacktivist, OT Cyberattacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Source: Birgit Korber via Alamy Stock Photo For Israel, 2023 will be remembered as the beginning...
CISO Planning for 2024 May Struggle When It Comes to AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild, Contributing Writer Source: Robert Hyrons via Alamy Stock Photo Just about every CISO knows how this scenario goes: Called in...
Attackers Abuse Google OAuth Endpoint to Hijack User Sessions – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: imageBROKER via Alamy Stock Photo Attackers have been exploiting an undocumented Google OAuth endpoint to hijack user...
Startups Scramble to Build Immediate AI Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Paul Shomo Source: Andrii Yalanskyi via Alamy Stock Photo COMMENTARY At the start of 2003, nobody knew the industry would be handed...
10 Years After Yahoo Breach, What’s Changed? (Not Much) – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: PhotoEdit via Alamy Stock Photo In September 2016, Yahoo copped to a breach of 500 million user...
Over $80m in Crypto Stolen in Cyber-Attack on Orbit Chain – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Over $80m worth of cryptocurrency has been stolen following a cyber-attack on cross-chain bridge project Orbit Chain. The blockchain revealed the...
Australian Court Service Hacked, Hearing Recordings at Risk – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Court cases and tribunals in Australia have been impacted by a cybersecurity incident, with attackers potentially accessing recordings of hearings, according...
Teen Found Alive After “Cyber-Kidnapping” Incident – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Chinese foreign exchange student has been found alive and well by Utah police after being caught up in what authorities...
Black Basta Ransomware Decryptor Published – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have published a new suite of tools designed to help victims of the prolific Black Basta ransomware recover their...
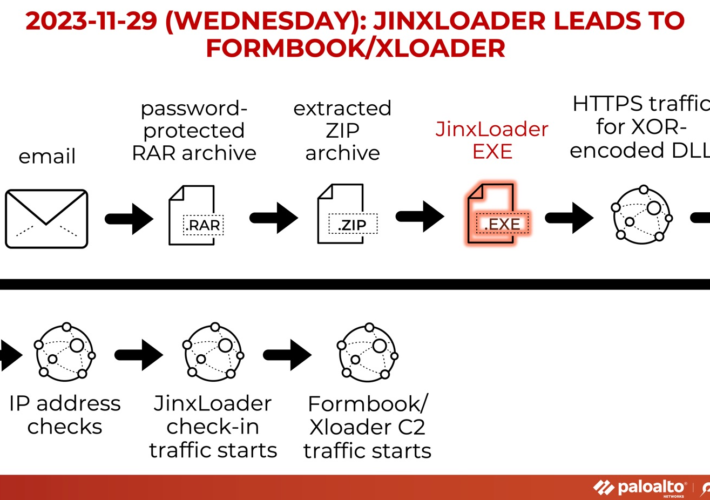
Experts warn of JinxLoader loader used to spread Formbook and XLoader – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of JinxLoader loader used to spread Formbook and XLoader JinxLoader is a new Go-based loader that was spotted...
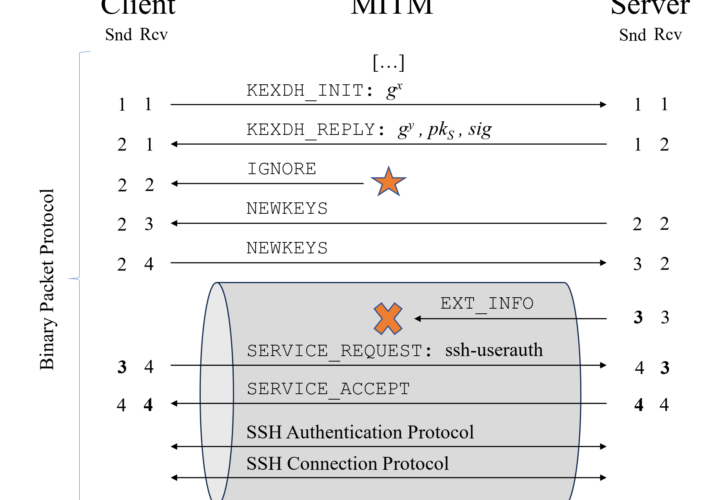
Terrapin attack allows to downgrade SSH protocol security – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Terrapin attack allows to downgrade SSH protocol security Researchers discovered an SSH vulnerability, called Terrapin, that could allow an attacker...
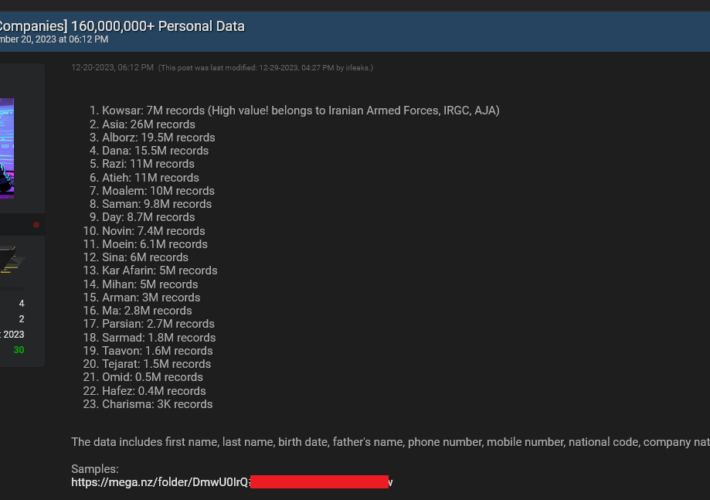
Multiple organizations in Iran were breached by a mysterious hacker – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Multiple organizations in Iran were breached by a mysterious hacker Hudson Researchers reported that a mysterious hacker launched a series...
Top 2023 Security Affairs cybersecurity stories – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Top 2023 Security Affairs cybersecurity stories These are the Top 2023 Security Affairs cybersecurity stories … enjoy it. CYBERCRIMINALS LAUNCHED...
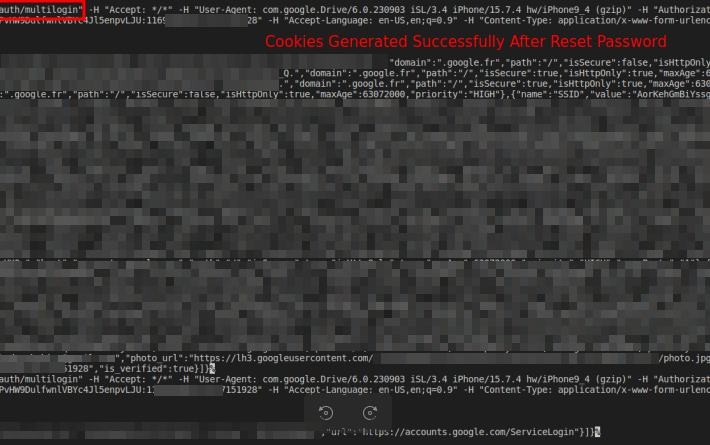
Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies CloudSEK researchers analyzed a zero-day exploit that can allow the...
The Definitive Enterprise Browser Buyer’s Guide – Source:thehackernews.com
Source: thehackernews.com – Author: . Security stakeholders have come to realize that the prominent role the browser has in the modern corporate environment requires a re-evaluation...