Source: securityaffairs.com – Author: Pierluigi Paganini
Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies

CloudSEK researchers analyzed a zero-day exploit that can allow the generation of persistent Google cookies through token manipulation.
In October 2023, a developer known as PRISMA first uncovered an exploit that allows the generation of persistent Google cookies through token manipulation. An attacker can use the exploit to access Google services, even after a user’s password reset.
Researchers from Hudson Rock were among the first to warn of threat actors exploiting the zero-day exploit:
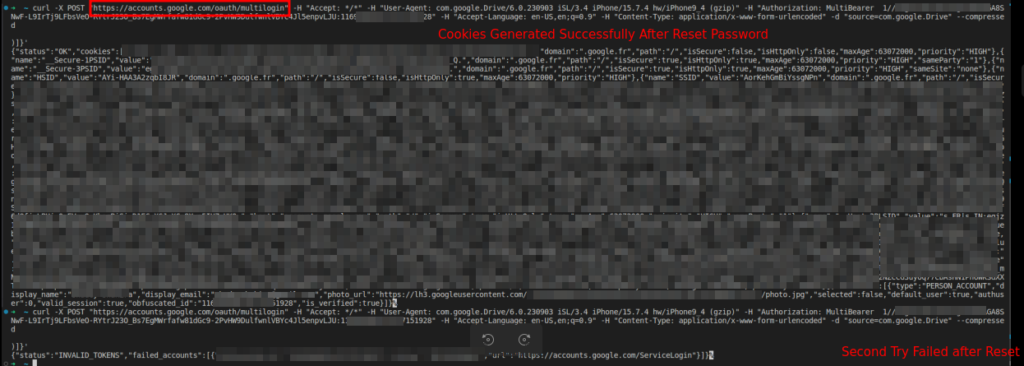
CloudSEK performed a reverse engineering of the exploit and discovered it relies on an undocumented Google OAuth endpoint named ‘MultiLogin.
The MultiLogin endpoint endpoint is an internal mechanism that allows the synchronization of Google accounts across services.
This endpoint receives a vector containing account IDs and auth-login tokens for efficiently handling concurrent sessions or seamlessly transitioning between user profiles.
The Lumma Infostealer was spotted using the exploit on November 14. Subsequently, other malware integrated the exploit, including Rhadamanthys, Risepro, Meduza, Stealc Stealer and recently the White Snake.
The researchers discovered that the malware targets Chrome’s token_service table of WebData to extract tokens and account IDs of chrome profiles logged in.
“This table contains two crucial columns: service (GAIA ID) and encrypted_token. The encrypted tokens are decrypted using an encryption key stored in Chrome’s Local State within the UserData directory, similar to the encryption used for storing passwords.” reads the report published by CloudSEK.

The Lumma malware continuously regenerates cookies for Google services by manipulating the token:GAIA ID pair. The experts pointed out that the exploit works even after users have reset their passwords.
“This persistence in access allows for prolonged and potentially unnoticed exploitation of user accounts and data.” continues the report.

“Analysis of the user-agent string found in the source code as seen in Figure7 (com.google.Drive/6.0.230903 iSL/3.4 iPhone/15.7.4 hw/iPhone9_4 (gzip)) suggests that a penetration test on Google Drive’s services on Apple devices was a potential origin for the exploit. The exploit’s imperfect testing led to revealing its source.” concludes the report.

At this time, Google has yet to confirm that threat actors are using the zero-day exploit in the MultiLogin endpoint.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Google cookies)
Original Post URL: https://securityaffairs.com/156723/hacking/exploit-regenerates-google-cookies.html
Category & Tags: Breaking News,Hacking,Malware,Cybercrime,Google cookies,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News – Breaking News,Hacking,Malware,Cybercrime,Google cookies,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News
Views: 0