Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer 3 Min Read Source: Weitwinkel via Shutterstock The US government, in collaboration with private sector stakeholders, has been...
Year: 2024
ICS and OT threat predictions for 2024 – Source: securelist.com
Source: securelist.com – Author: Evgeny Goncharov Kaspersky Security Bulletin We do not expect rapid changes in the industrial cyberthreat landscape in 2024. Most of the below-described...
Italian Businesses Hit by Weaponized USBs Spreading Cryptojacking Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 31, 2024NewsroomCryptocurrency / Cybersecurity A financially motivated threat actor known as UNC4990 is leveraging weaponized USB devices as an initial...
The SEC Won’t Let CISOs Be: Understanding New SaaS Cybersecurity Rules – Source:thehackernews.com
Source: thehackernews.com – Author: . The SEC isn’t giving SaaS a free pass. Applicable public companies, known as “registrants,” are now subject to cyber incident disclosure...
Hackers Exploiting Ivanti VPN Flaws to Deploy KrustyLoader Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 31, 2024NewsroomCyber Attack / Network Security A pair of recently disclosed zero-day flaws in Ivanti Connect Secure (ICS) virtual private...
New Glibc Flaw Grants Attackers Root Access on Major Linux Distros – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 31, 2024NewsroomVulnerability / Endpoint Security Malicious local attackers can obtain full root access on Linux machines by taking advantage of...
New Images of Colossus Released – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments tfb • January 30, 2024 5:05 PM I do wonder whether the remaining colossi were really still useful...
NSA Buying Bulk Surveillance Data on Americans without a Warrant – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments whoops • January 30, 2024 7:58 AM The problem is partly the legality of the NSA buying this....
The Taylor Swift deepfake porn is nothing new – but that doesn’t mean we shouldn’t be concerned – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog In a recent unsettling turn of events, AI-generated explicit images of the renowned singer Taylor Swift have flooded X (formerly...
USENIX Security ’23 – Keane Lucas, Samruddhi Pai, Weiran Lin, Lujo Bauer, Michael K. Reiter, Mahmood Sharif – Adversarial Training for Raw-Binary Malware Classifiers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Keane Lucas, Samruddhi Pai, Weiran Lin, Lujo...
Most Ransom Groups Now Using Extortion, Delinea Survey Finds – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The ransomware landscape continues to evolve, with attackers now more likely to exfiltrate data and threaten victims with selling or...
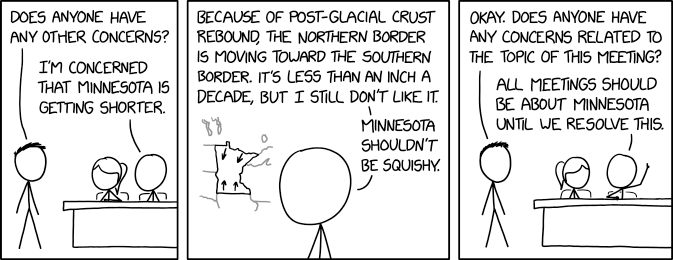
Randall Munroe’s XKCD ‘Minnesota’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
‘Extremely serious’ — Mercedes-Benz Leaks Data on GitHub – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings My friends all hack Porsches—I must make amends. For four months, Mercedes-Benz lost control of critical private data—including designs, security keys...
DTEX i³ Issues Threat Advisory for Mitigating Insider Abuse of Insecure Web Apps – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kellie Roessler Web applications offer powerful workforce efficiencies, but they are not without their risks. Misconfiguration of web applications can open the...
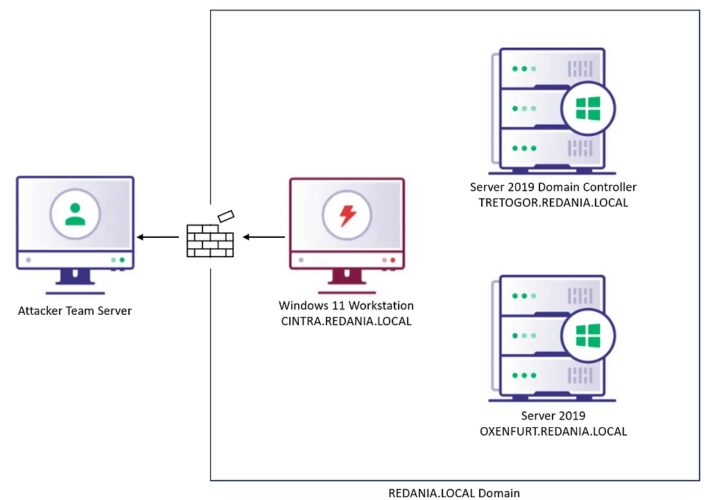
BOFHound: Session Integration – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Creel Background If you’ve found yourself on a red team assessment without SharpHound (maybe due to OPSEC or stealth requirements), you’d...
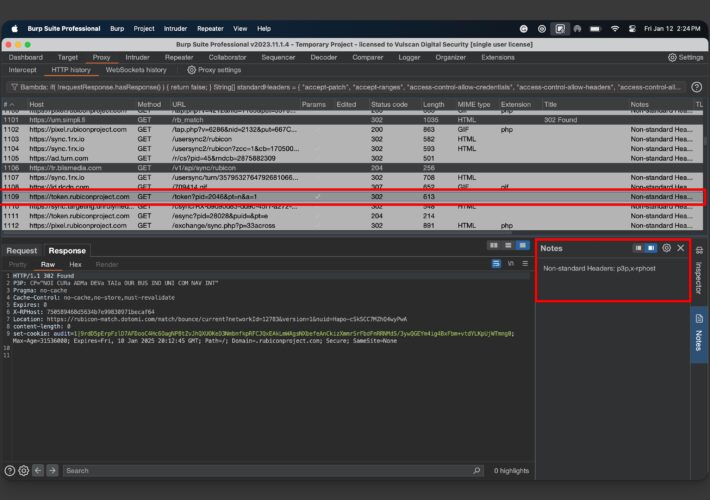
Detecting Uncommon Headers in an API using Burp Bambda Filters – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dana Epp What if I told you that many APIs leverage custom HTTP headers to drive business logic and behavior? Would you...
Use LLMs Safely with AI Workflows | Impart Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Impart Security Blog Today we are announcing the launch of Impart AI Workflows, our newest LLM-powered enhancement. ✨ Impart Security’s AI Workflows...
Insurance Broker Keenan Says 1.5 Million Affected by Data Breach – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Insurance broker Keenan and Associates is notifying more than 1.5 million people that their personal information may have been stolen...
Ransomware Attack Hits Schneider Electric Sustainability Unit – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Manufacturer Confirms Systems Down, Data on Energy Consumption, Emission Accessed Cal Harrison • January 30,...
Jenkins Servers Used for CI/CD Contain Critical RCE Flaw – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Approximately 45,000 Vulnerable Servers Worldwide Mihir Bagwe (MihirBagwe) , Prajeet Nair (@prajeetspeaks) • January...
The Power Trio: UEBA, Cloud, and ML for Unusual Security Behaviors – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Boyu Wang Principal Data Scientist, Snowflake Boyu Wang is a Principal Data Scientist at Snowflake where he designs, architects, as well...
Italian Data Regulator Slams EU-Funded AI Projects – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , General Data Protection Regulation (GDPR) , Next-Generation Technologies & Secure Development City of Trento Must...
US IaaS Providers Face ‘Know Your Customer’ Regulation – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Security Operations Rule Is a Bid to Deter Malicious Foreign Use of US IaaS Providers Chris Riotta (@chrisriotta)...
Brazilian Feds Dismantle Grandoreiro Banking Trojan, Arresting Top Operatives – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 30, 2024NewsroomCyber Crime / Malware A Brazilian law enforcement operation has led to the arrest of several Brazilian operators in...
URGENT: Upgrade GitLab – Critical Workspace Creation Flaw Allows File Overwrite – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 30, 2024NewsroomDevSecOps / Vulnerability GitLab once again released fixes to address a critical security flaw in its Community Edition (CE)...
China-Linked Hackers Target Myanmar’s Top Ministries with Backdoor Blitz – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 30, 2024NewsroomMalware / Cyber Espionage The China-based threat actor known as Mustang Panda is suspected to have targeted Myanmar’s Ministry...
Online ransomware decryptor helps recover partially encrypted files – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas CyberArk has created an online version of ‘White Phoenix,’ an open-source ransomware decryptor targeting operations using intermittent encryption. The company announced...
US charges two more suspects with DraftKing account hacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Department of Justice arrested and charged two more suspects for their involvement in the hacking of almost 68,000 DraftKings accounts in...
Vastaamo hacker traced via ‘untraceable’ Monero transactions, police says – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Julius Aleksanteri Kivimäki, the suspect believed to be behind an attack against one of Finland’s largest psychotherapy clinics, Vastaamo, was...
A mishandled GitHub token exposed Mercedes-Benz source code – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A mishandled GitHub token gave unrestricted access to Mercedes-Benz’s internal GitHub Enterprise Service, exposing source code to the public. Mercedes-Benz...