Source: www.darkreading.com – Author: PRESS RELEASE BOULDER, Colo., Feb 15, 2024 – Strata Identity, the Identity Orchestration company, today announced Global Access Orchestration Recipes that manage the...
Year: 2024
Quorum Cyber Joins Elite Microsoft FastTrack-Ready Partner Group – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Edinburgh, United Kingdom – February 15, 2024 – Quorum Cyber, a leading cybersecurity firm with operations in the UK and the...
LightEdge Releases Next-Gen Suite of Cloud Security & Managed Services – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE DES MOINES, Iowa, Feb. 15, 2024 /PRNewswire/ — LightEdge, a leading provider of secure cloud and colocation, has unveiled the next generation of...
Vectra AI Launches Global, 24×7 Open MXDR Service Built to Defend Against Hybrid Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE San Jose, Calif. – February 15, 2024 – Vectra AI, Inc., the leader in hybrid attack detection, investigation and response,...
Malware Response Checklist – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Whether an infection is the result of a disgruntled employee, hardware vulnerability, software-based threat, social engineering penetration, robotic attack or human error,...
Somos, Inc. Protects Businesses’ IoT Assets With the Availability of SomosID – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE EAST BRUNSWICK, N.J., Feb. 14, 2024 /PRNewswire/ — Somos, Inc., an industry expert in identity management, fraudprevention and data services who is recognized...
Volt Typhoon Hits Multiple Electric Utilities, Expands Cyber Activity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading The portion of China’s Volt Typhoon advanced persistent threat (APT) that focuses on infiltrating operational...
JumpCloud’s Q1 2024 SME IT Trends Report Reveals AI Optimism Tempered by Security Concerns – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE LOUISVILLE, Colo. — JumpCloud Inc., today announced the findings from its Q1 2024 small to medium-sized enterprise (SME) IT Trends Report,...
Feds Disrupt Botnet Used by Russian APT28 Hackers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Federal law enforcement kicked Russian state hackers off a botnet comprising at least hundreds of home office and small office...
USENIX Security ’23 – PrivTrace: Differentially Private Trajectory Synthesis by Adaptive Markov Models – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Haiming Wang, Zhikun Zhang, Tianhao Wang, Shibo He, Michael Backes, Jiming Chen, Yang Zhang Many thanks to USENIX for...
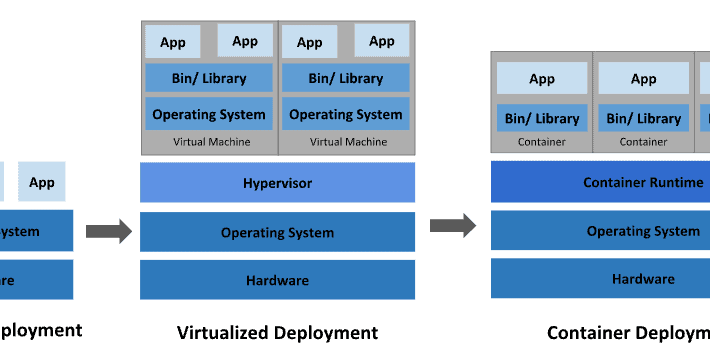
How To Monitor Kubernetes Audit Logs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelsey Gast In today’s fast-paced landscape of container orchestration, Kubernetes is a powerful tool for managing and scaling applications. However, ensuring the...
Learn the Most Essential Cybersecurity Protections for Schools – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith Malicious actors and hacker groups are actively targeting schools. According to reports, there has been a 146% increase in malware...
How ITDR Could Have Helped Microsoft in the Midnight Blizzard Hack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rezonate Identity-based attacks are on the rise, but they can be prevented with the right identity threat detection and response (ITDR) measures. ...
AppSec vendors and CISOs: a love-hate relationship? ⎜Olivia Rose – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Charikova Welcome to the Elephant in AppSec, the podcast to explore, challenge, and boldly face the AppSec Elephants in the room....
Randall Munroe’s XKCD ‘Research Account’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
The Strategic Partnership Elevating API and Endpoint Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tony Bradley Salt Security has announced a pivotal partnership with CrowdStrike. This collaboration marks a significant milestone for businesses seeking robust, integrated...
The Coming End of Biometrics Hastens AI-Driven Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Gallagher Until recently I thought we had a lot of time ahead of us to be secure in using biometrics to...
Complexity and software supply chain security: 5 key survey takeaways – Source: securityboulevard.com
Source: securityboulevard.com – Author: John P. Mello Jr. Organizations are struggling with software supply chain security. That fact was further exposed this month with the Enterprise...
Sophos’ Kris Hagerman Steps Down as CEO, Joe Levy Takes Helm – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Managed Detection & Response (MDR) Hagerman Moves to Advisory Role After Leading Company...
OpenAI and Microsoft Terminate State-Backed Hacker Accounts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Hackers Used LLMs to Perform Tasks That Non-AI Tools Can...
6 Categories of Modern Threat Landscape | Empowering Business Continuity for Cyber Resilience – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Darren Thomson Field CTO – Security, EMEAI, Commvault Darren is the Field CTO for Security covering EMEA and India, where he...
Harnessing Exploitability Information for Effective Prioritization – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , DevSecOps , Next-Generation Technologies & Secure Development Presented by Mend.io 60 minutes Do you...
Breach Roundup: Zeus Banking Trojan Leader Pleads Guilty – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Also: Polish Prime Minister Says Previous Administration Deployed Pegasus Spyware...
To Avoid Bankruptcy, EMR Firm Settles Lawsuit for $4M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Industry Specific , Legislation & Litigation Pediatric Tech Vendor Hit by 2022 Data Breach Affecting 3 Million – Mostly...
On the Insecurity of Software Bloat – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Good essay on software bloat and the insecurities it causes. The world ships too much code, most of it by...
WEF Global Security Outlook Report 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Secure Coding Guidelines for Application Development
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Ransomware Incident Response Playbook Framework – Learn how to build a ransomware IR playbook to prepare and protect your organization
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Purple Team Scenarios
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OT Cyber Security – Ensuring Business Resiliency in Life Sciences Manufacturing 4.0
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...