Source: www.techrepublic.com – Author: One of the key requirements of the General Data Protection Regulation is a demonstrated effort to enforce security measures that safeguard customer...
Year: 2024
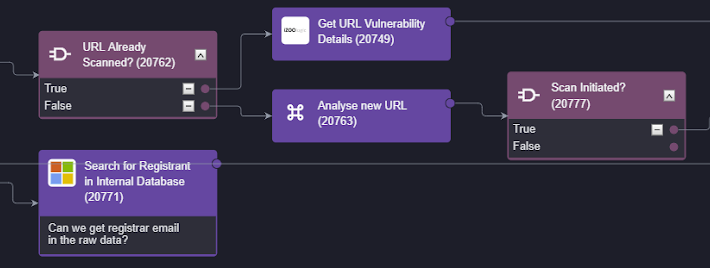
USENIX Security ’23 – Yu Chen, Yang Yu, Lidong Zhai – InfinityGauntlet: Expose Smartphone Fingerprint Authentication to Brute-force Attack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, February 28, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Why Smart SOAR is the Best SOAR for iZOOlogic – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pierre Noujeim The collaboration between Smart SOAR (Security Orchestration, Automation, and Response) and iZOOlogic offers a comprehensive solution to protect your brand...
Navigating the Waters of Generative AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: brianrobertson Part I: The Good and the Bad of AI Few would argue that 2023 was the year AI, specifically generative AI...
FBI Warns: Ubiquiti EdgeRouter is STILL Not Secure – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Fancy Bear still hacking ubiquitous gear, despite patch availability. Ubiquiti’s EdgeRouter ships with its config open to the internet and default...
Randall Munroe’s XKCD ‘Goodhart’s Law’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored by Marc Handelman. Read the original post...
10 Years of SafeBreach – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach We all know cybersecurity is a team sport—one that is enhanced and optimized by the collective knowledge of a committed community....
Building Cyber Resilience: Insights into NIST CSF 2.0 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maahnoor Siddiqui After several years of deliberation and collaboration with industry experts, NIST has released the newest version of the NIST CSF....
Imperva Customers are Protected Against New SQL Injection Vulnerability in WordPress Plugin – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gabi Stapel A critical security flaw, identified as CVE-2024-1071, was discovered in the Ultimate Member plugin for WordPress, affecting over 200,000 active...
Account Takeover Protection: Risks, Targets and Prevention Strategies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sarah Hunter-Lascoskie When a customer signs up for a loyalty program or otherwise entrusts your organization with their personal and sensitive data,...
USENIX Security ’23 – Yuanyuan Yuan, Zhibo Liu, Shuai Wang – CacheQL: Quantifying and Localizing Cache Side-Channel Vulnerabilities in Production Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics USENIX Security ’23 – Yu Chen, Yang Yu, Lidong Zhai – InfinityGauntlet: Expose Smartphone Fingerprint Authentication to Brute-force...
Okta Security Push Pays Dividends Following String of Issues – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Identity & Access Management , Security Operations Credential Stuffing Plummets, More Malicious Requests Detected Amid Huge Investment Michael Novinson (MichaelNovinson) •...
Has the US Created the Wrong War Machine? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Training & Security Leadership We Need Low-Cost, High-Volume Weapons Systems to...
Chinese Group Runs Highly Persistent Ivanti 0-Day Exploits – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development UNC5325 Can Remain in Hacked Devices...
PKI Modernization: Preparing for Emerging Challenges Like PQC and AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Device Identification , Endpoint Security Presented by DigiCert 45 minutes In today’s global landscape,...
Down, Not Out: Russian Hacktivists Claiming DDoS Disruptions – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Distributed Denial-of-Service Attacks Decline as Russia-Ukraine War Continues Mathew J. Schwartz (euroinfosec)...
BlackCat Pounces on Health Sector After Federal Takedown – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Feds Issue Alert as Change Healthcare Hack Affects Medicare, CVS Caremark, MetLife...
Smashing Security podcast #361: Wireless charging woe, AI romance apps, and ransomware revisited – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Your smartphone may be toast – if you use a hacked wireless charger, we take a closer look at the...
How to interpret the MITRE Engenuity ATT&CK® Evaluations: Enterprise – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Graham Cluley Security News is sponsored this week by the folks at Cynet. Thanks to the great team there for...
Matthew Perry’s Twitter account hacked by cryptocurrency scammers – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Matthew Perry’s official Twitter account was hijacked by scammers this week who attempted to solicit donations from well-meaning fans of...
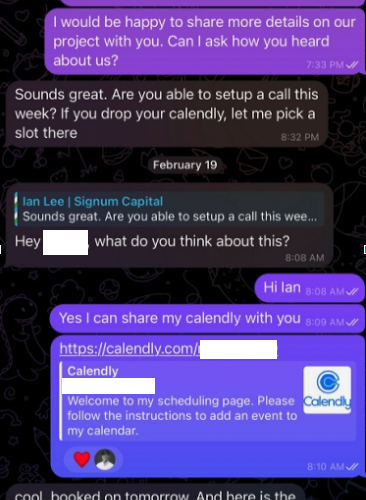
Calendar Meeting Links Used to Spread Mac Malware – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Malicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar...
‘Illusive’ Iranian Hacking Group Ensnares Israeli, UAE Aerospace and Defense Firms – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Zoonar GmbH via Alamy Stock Photo An Iranian Revolutionary Guard Corps (IGRC)-linked threat group is staging political...
Kaspersky Finds Attacks on Mobile Devices Significantly Increased in 2023 – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Woburn, MA – February 26, 2024 — In 2023, Kaspersky observed a steady increase in the number of attacks on mobile devices, reaching almost...
U-Haul Reports 67K Customers Impacted by Data Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: LH Images via Alamy Stock Photo U-Haul — a truck, trailer, and self-storage rental company based in Arizona...
Russia’s ‘Midnight Blizzard’ Targets Service Accounts for Initial Cloud Access – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: PopTika via Shutterstock “Midnight Blizzard,” the threat group affiliated with Russian intelligence services (SVR) and the entity...
Apple, Signal Debut Quantum-Resistant Encryption, but Challenges Loom – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Production Perig via Shutterstock Apple’s new PQ3 post-quantum cryptographic (PQC) protocol introduced last week is the latest...
Mexico’s ‘Timbre Stealer’ Campaign Targets Manufacturing – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Tom King via Alamy Stock Photo Cybercriminals are spreading a new infostealer across Mexico by catching targets...
UAC-0184 Targets Ukrainian Entity in Finland With Remcos RAT – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: David Chapman via Alamy Stock Photo The threat actor tracked as UAC-0184 has been using steganography techniques...
NIST Releases Cybersecurity Framework 2.0 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Borka Kiss via Alamy Stock Photo After several years of deliberation, the National Institute for Standards and Technology...
The Next Gen of Cybersecurity Could Be Hiding in Big Tech – Source: www.darkreading.com
Source: www.darkreading.com – Author: Yaniv Vardi Source: Federico Caputo via Alamy Stock Photo COMMENTARY The world is facing an unprecedented number of cyber threats and historic...