Source: www.darkreading.com – Author: PRESS RELEASE VANCOUVER, BC,March 12, 2024/PRNewswire/ — Codezero, the innovator in secure enterprise microservices development, today announced a $3.5 million seed-funding round led...
Year: 2024
Claroty Launches Advanced Anomaly Threat Detection for Medigate – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE NEW YORK and ORLANDO, Fla. — March 12, 2024 — Claroty, the cyber-physical systems (CPS) protection company, today announced at...
10 Tips for Better Security Data Management – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer Whether it is to support compliance efforts for regulatory mandated logging, feed daily security operations center (SOC) work,...
ChatGPT Spills Secrets in Novel PoC Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: PopTika via Shutterstock A team of researchers from Google DeepMind, Open AI, ETH Zurich, McGill University, and...
Yacht Retailer MarineMax Files ‘Cyber Incident’ with SEC – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading 1 Min Read Source: Kip Evans via Alamy Stock Photo According to the documents it filed...
How to Identify & Monitor Insider Threat Indicators [A Guide] – Source: securityboulevard.com
Source: securityboulevard.com – Author: The Constella Team Most security protocols look outward when looking for cybersecurity threats. But what about threats from inside your organization? Our...
USENIX Security ’23 – Pushed By Accident: A Mixed-Methods Study On Strategies Of Handling Secret Information In Source Code Repositories – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Alexander Krause, Jan H. Klemmer, Nicolas Huaman, Dominik Wermke, Yasemin Acar, Sascha Fahl Many thanks to USENIX for publishing...
Illicit Credentials Marketplace Admin Gets 42-Month Sentence – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Mihir Bagwe (MihirBagwe) • March 15, 2024 A co-administrator of an illicit online...
Ransomware Groups’ Data Leak Blogs Lie: Stop Trusting Them – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Mathew J. Schwartz (euroinfosec) • March 15, 2024 Ransomware leak sites are not...
Hackers exploit Aiohttp bug to find vulnerable networks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The ransomware actor ‘ShadowSyndicate’ was observed scanning for servers vulnerable to CVE-2024-23334, a directory traversal vulnerability in the aiohttp Python...
TikTok Ban Raises Data Security, Control Questions – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: SOPA Images Limited via Alamy Stock Photo Congress voted in favor of banning the popular social media...
Global Threat Intelligence Report March 2024 by Blackberry Cybersecurity
As we enter 2024, we mark a full calendar year of quarterly BlackBerry® Global Threat Intelligence Reports. And what a year it has been. Over the...
Active Directory Security Guide – The Complete Active Directory Security Handbook
Active Directory (AD), introduced with Windows 2000, has become an integral part of modern organizations, serving as the backbone of identity infrastructure for 90% of Fortune...
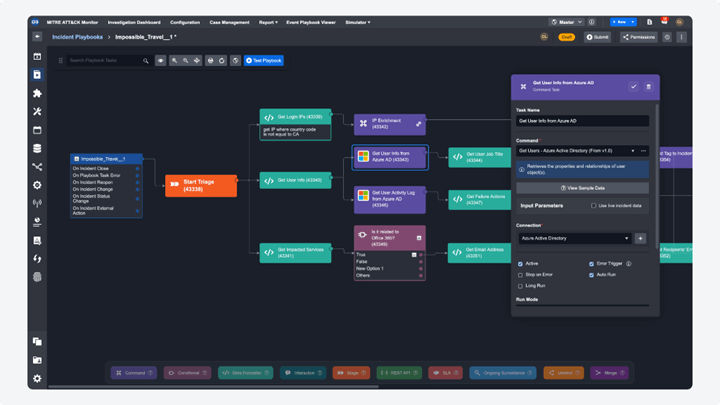
What it’s Like Using Integrations Built by D3 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pierre Noujeim Integrating a variety of cybersecurity tools and platforms is often a complex and demanding task. This process, essential to the...
International Monetary Fund email accounts hacked in cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The International Monetary Fund (IMF) disclosed a cyber incident on Friday after unknown attackers breached 11 IMF email accounts earlier...
CEO of Data Privacy Company Onerep.com Founded Dozens of People-Search Firms – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The data privacy company Onerep.com bills itself as a Virginia-based service for helping people remove their personal information from almost 200...
Patch Tuesday, March 2024 Edition – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Apple and Microsoft recently released software updates to fix dozens of security holes in their operating systems. Microsoft today patched at...
‘GhostRace’ Speculative Execution Attack Impacts All CPU, OS Vendors – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: raigvi via Shutterstock Researchers at IBM and VU Amsterdam have developed a new attack that exploits speculative...
NHS Breach, HSE Bug Expose Healthcare Data in the British Isles – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Panther Media via Alamy Stock Photo This week, a division of the National Health Service (NHS) Scotland...
ChatGPT vs. Gemini: Which Is Better for 10 Common Infosec Tasks? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alex Haynes Alex Haynes, Chief Information Security Officer, IBS Software March 15, 2024 5 Min Read Source: Blackboard via Alamy Stock Photo...
6 CISO Takeaways From the NSA’s Zero-Trust Guidance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Olivier Le Moal via Shutterstock The reality of cybersecurity for companies is that adversaries compromise systems and...
Red Canary Announces Full Coverage of All Major Cloud Providers – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE DENVER, March 5, 2024 – Red Canary today announced full coverage of its detection and response capabilities to include all...
Expel Releases Updated Toolkit in Response to NIST 2.0 – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE HERNDON, Va., March 13, 2024 — (BUSINESS WIRE) — Expel, the leading managed detection and response (MDR) provider, today unveiled...
Nozomi Networks Secures $100M Investment to Defend Critical Infrastructure – Source: www.darkreading.com
Source: www.darkreading.com – Author: SAN FRANCISCO, March 13, 2024 — Nozomi Networks Inc. today announced a $100 million Series E funding round to help accelerate innovative...
FCC Approves Voluntary Cyber Trust Labels for Consumer IoT Products – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: 1800 JIRAROJ PRADITCHAROENKUL via Alamy Stock Photo The Federal Communications Commission (FCC) will be rolling out a...
Fortinet Warns of Yet Another Critical RCE Flaw – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer 3 Min Read Source: Postmodern Studio via Shutterstock Fortinet has patched a critical remote code execution (RCE) vulnerability...
Alabama Under DDoS Cyberattack by Russian-Backed Hacktivists – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Illustrated History via Alamy Stock Photo Alabama has been grappling with network disruptions, following cyber...
StopCrypt: Most widely distributed ransomware now evades detection – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new variant of StopCrypt ransomware (aka STOP) was spotted in the wild, employing a multi-stage execution process that involves...
SIM swappers hijacking phone numbers in eSIM attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas SIM swappers have adapted their attacks to steal a target’s phone number by porting it into a new eSIM card,...
Tech support firms Restoro, Reimage fined $26 million for scare tactics – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Tech support companies Restoro and Reimage will pay $26 million to settle charges that they used scare tactics to trick...






![how-to-identify-&-monitor-insider-threat-indicators-[a-guide]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2024/03/122991/how-to-identify-monitor-insider-threat-indicators-a-guide-source-securityboulevard-com.jpg)