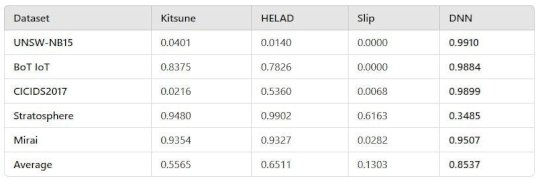
Source: socprime.com – Author: Justin Erb The rare command in Splunk helps you find the least common values in a specific field of your data. This is useful...
Year: 2024
coalesce Function in Splunk – Source: socprime.com
Source: socprime.com – Author: Justin Erb WRITTEN BY Justin Erb Threat Hunter [post-views] December 30, 2024 · 1 min read The Splunk coalesce function returns the first non-null...
The Traditional Advocates of the Security Perimeter Don’t Want You to Know about Data-Centric Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In an era defined by continuous media announcements of organizations that have suffered both government and private data breaches and...
Windows 11 Media Update Bug Stops Security Updates – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Published December 30, 2024 Microsoft advises users not to install recent security updates using physical media. The company is working...
VyprVPN Review (2025): Can It Still Perform This Year and Beyond? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Madeline Clarke We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
How to Get the Most Out of Cyber Insurance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rita Gurevich Source: Mungkhood Studio via Shutterstock COMMENTARY Cybersecurity insurance is the fastest-growing segment of the global insurance market, and there’s a good...
What Security Lessons Did We Learn in 2024? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild Source: Artur Szczybylo via Alamy Stock Photo From the growing sophistication of zero-day exploits to the entrenchment of nation-state and...
Deepfakes, Quantum Attacks Loom Over APAC in 2025 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Tero Vesalainen via Shutterstock If incidents this year are any indication, deepfakes and “harvest now, decrypt later”...
Happy 15th Anniversary, KrebsOnSecurity! – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Image: Shutterstock, Dreamansions. KrebsOnSecurity.com turns 15 years old today! Maybe it’s indelicate to celebrate the birthday of a cybercrime blog that...
Majority of UK SMEs Lack Cybersecurity Policy – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: More than two-thirds (69%) of UK small and medium enterprises (SMEs) lack a cybersecurity policy, according to figures from specialist insurance firm...
Achieve Satisfaction with Streamlined Secrets Rotation Processes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are Secrets Rotation Processes a Keystone in Your Cybersecurity Strategy? The digital business landscape has evolved with technologies enabling organizations...
Empowering Security: Mastering Least Privilege – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Mastering Least Privilege Essential? The least privilege principle remains a cornerstone for securing machine identities and their secrets....
DEF CON 32 – How State Laws Meant to Protect Children Raise Other Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Sunday, December 29, 2024 Home » Security Bloggers Network » DEF CON 32 – How State Laws Meant to Protect...
Anomaly Detection for Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Evan Powell A long promising approach comes of age I won’t revisit the arguments for anomaly detection as a crucial piece of cybersecurity....
A 9th Telecoms Firm Has Been Hit by a Massive Chinese Espionage Campaign, the White House Says – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A ninth U.S. telecoms firm has been confirmed to have been hacked as part of a sprawling Chinese espionage campaign...
Russia, Apple, And the New Front Line in The Fight for Internet Freedom – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Russia’s reputation for suppressing internet freedom and free expression is well documented. VPNs have long had a contentious relationship with...
Is Platform Engineering a Step Towards Better Governed DevOps? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Since 2010, Puppet’s annual State of DevOps Report has tracked trends in IT, including security and, more recently, the growth of platform...
Best Practices for Effective Privileged Access Management (PAM) – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Marcus Scharra senhasegura December 27, 2024 Privileged accounts are highly coveted targets for malicious attackers due to the extensive access...
Driving Security Forward: How Automakers Can Stay Ahead of Cyber Threats and Compliance Challenge – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team As technology revolutionizes the way OEMs build cars, this software-powered shift has also introduced new risks and challenges. As cars...
Embracing The Intersection of Ethics and Digital Trust – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The Ethical Dimension of Emerging Technologies Ethics, fundamentally, deals with moral values and codes of conduct within societies and social...
Best Practices in Cybersecurity With Exhaustive Static Analysis To Secure Software Integrity – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Introduction The complexity of modern software systems, coupled with the increasing sophistication of cyber threats, underscores the critical need for...
Gain Relief with Strategic Secret Governance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Efficient Secret Governance Essential? Have you ever pondered the importance of strategic secret governance and what it means...
Innovation in API Security: What’s New – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn So, What’s the Deal with Recent API Security Innovations? As companies across the spectrum of industries including finance, healthcare, travel,...
Robots.txt: From Basic Crawler Control to AI-Powered Security Shield – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author The humble robots.txt file has long been viewed as a simple traffic controller for search...
DEF CON 32 – XR for All: Accessibility and Privacy for Disabled Users – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Saturday, December 28, 2024 Home » Security Bloggers Network » DEF CON 32 – XR for All: Accessibility and Privacy...
Reassured Compliance in Multi-Cloud Environments – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn The Surefire Path to Reassured Security in Cloud Environments Is your organization grappling with the challenge of maintaining security in...
Budget-Friendly Security Solutions That Work – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Adopting Cost-Effective Security Protocols? As a cybersecurity specialist, you might have often questioned how you could manage your...
6 Security Vendors Named ‘Leaders’ In Gartner’s Inaugural Email Security Magic Quadrant – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: The first-ever Gartner ranking for Email Security Platforms included 14 companies in total. Six cybersecurity vendors were chosen to appear in the...
Best of 2024: AT&T Says 110M Customers’ Data Leaked — Yep, it’s Snowflake Again – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings NYSE:T loses yet more customer data—this time, from almost all of them. Almost all AT&T customers in 2022 had their phone metadata...
DEF CON 32 – Offensive Security Testing Safeguarding the Final Frontier – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Friday, December 27, 2024 Home » Security Bloggers Network » DEF CON 32 – Offensive Security Testing Safeguarding the Final...