Source: www.securityweek.com – Author: Ionut Arghire The Play ransomware group has claimed responsibility for the cyberattack that disrupted operations at donut and coffee retail chain Krispy...
Month: December 2024
Another NetWalker Ransomware Affiliate Gets 20-Year Prison Sentence in US – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A Romanian national accused of conducting cyberattacks using the NetWalker ransomware has been sentenced to 20 years in prison in...
CISA Urges Immediate Patching of Exploited BeyondTrust Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US cybersecurity agency CISA warns that a recently disclosed vulnerability in BeyondTrust’s remote access products has been exploited in...
Rockwell PowerMonitor Vulnerabilities Allow Remote Hacking of Industrial Systems – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Critical vulnerabilities patched by Rockwell Automation in its Allen-Bradley PowerMonitor 1000 product could allow remote hackers to breach an organization’s...
How to Implement Impactful Security Benchmarks for Software Development Teams – Source: www.securityweek.com
Source: www.securityweek.com – Author: Matias Madou Vulnerabilities introduced from third-party components continue to create major issues for organizations: Nearly all codebases, for example, contain open-source components,...
CISA Releases Mobile Security Guidance After Chinese Telecom Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US cybersecurity agency CISA on Wednesday released guidance for highly targeted individuals to protect their mobile communications against exploitation...
Ukrainian Raccoon Infostealer Operator Sentenced to Prison in US – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Department of Justice on Wednesday announced the sentencing of a Ukrainian national for his role in the distribution...
SWE Shares First Conference Sustainability Report
Sharing a few highlights from the WE24 conference held at McCormick Place. Source Views: 3
OT/ICS Engineering Workstations Face Barrage of Fresh Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Constantine Johnny via Alamy Stock Photo NEWS BRIEF Operational technology (OT) and Industrial control systems...
Fortinet Addresses Unpatched Critical RCE Vector – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Konstantin Nechaev via Alamy Stock Photo NEWS BRIEF Fortinet has finally patched a critical...
Orgs Scramble to Fix Actively Exploited Bug in Apache Struts 2 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: ZUMA Press, Inc. via Alamy Stock Photo A critical, stubborn new vulnerability in Apache Struts 2 may...
Bridging the ‘Keyboard-to-Chair’ Gap With Identity Verification – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild Source: Carlos Castilla via Alamy Stock Photo Just about everyone is familiar with the annoying process of becoming locked out...
Vendors Chase Potential of Non-Human Identity Management – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Source: Poptika via Shutterstock When industrial automation giant Schneider Electric revealed last month that ransomware gang Hellcat stole 40GB of sensitive data,...
Malvertisers Fool Google With AI-Generated Decoy Content – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Bits And Splits via Shtterstock Threat actors appear to have found yet another innovative use case for...
Supply Chain Risk Mitigation Must Be a Priority in 2025 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob T. Lee Rob T. Lee, Chief of Research & Head of Faculty, SANS Institute December 19, 2024 5 Min Read Source:...
CISO Challenges for 2025: Overcoming Cybersecurity Complexities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Horn As organizations recognize the immense value and criticality of your data and systems, cybersecurity has become intrinsically linked to business...
DEF CON 32 – Exploiting Cloud Provider Vulnerabilities for Initial Access – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, December 19, 2024 Home » Security Bloggers Network » DEF CON 32 – Exploiting Cloud Provider Vulnerabilities for Initial...
Protecting Your Heart and Wallet: A Guide to Safe Charitable Giving – Source: securityboulevard.com
Source: securityboulevard.com – Author: hmeyers December 19, 2024 The holiday season brings out the best in people, with many feeling inspired to support worthy causes. Unfortunately,...
What Is Privilege Escalation? Types, Examples, and Prevention – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Privilege escalation is a critical cybersecurity threat in which a user—usually a malicious actor—gains access to data beyond what their...
Detection as Code: Key Components, Tools, and More – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security As software development accelerates, the need to identify threats and respond in real time is greater than ever. Detection as...
Kubernetes Secrets: How to Create and Use Them – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Kubernetes, also known as K8s, is a powerful platform for orchestrating containers in complex, distributed environments. Among its many features,...
Randall Munroe’s XKCD ‘Linear Sort’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
CVE-2024-50379: A Critical Race Condition in Apache Tomcat – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lisa Haas Recently, an Apache Tomcat web server vulnerability, tracked as CVE-2024-50378, has been published, exposing the platform to remote code execution...
BadRAM-ifications: A Low-Cost Attack on Trusted Execution Environments – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Recent research has uncovered a concerning vulnerability in modern Trusted Execution Environments (TEEs) that challenges fundamental assumptions about memory security....
Healthcare in the Cross Hairs: Cybercriminals Have Found Another High-Value Target – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bob Palmer Here at ColorTokens, we’ve recently been engaged with a leading cancer center to improve its cybersecurity posture. After phase one...
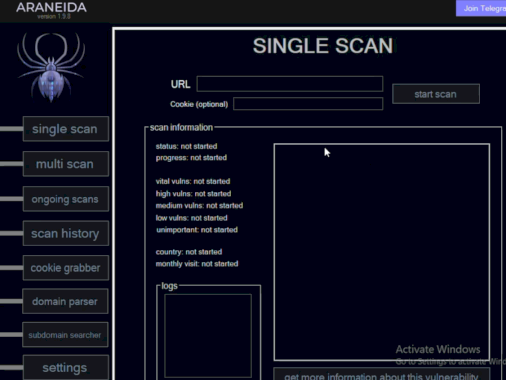
Web Hacking Service ‘Araneida’ Tied to Turkish IT Firm – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Cybercriminals are selling hundreds of thousands of credential sets stolen with the help of a cracked version of Acunetix, a powerful...
US Organizations Still Using Kaspersky Products Despite Ban – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Written by Despite the ban on Kaspersky products in the US they continue to be actively used by US organizations, including by...
New Malware Can Kill Engineering Processes in ICS Environments – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: New malware attacks targeting industrial control systems (ICS) are capable of killing engineering processes, a Forescout analysis has found. The researchers identified...
EU Opens Door for AI Training Using Personal Data – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Using personal data without consent to train AI models will not necessarily infringe the EU’s General Data Protection Regulation (GDPR), according to...
Crypto-Hackers Steal $2.2bn as North Koreans Dominate – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Threat actors stole $2.2bn from cryptocurrency platforms in 2024, with the majority (61%) of illicit funds attributed to North Korean hackers, according...