Source: securityboulevard.com – Author: Security Insights Team CVSS base scores and temporal scores are not the same. Understanding the distinctions between them is critical for any...
Month: December 2024
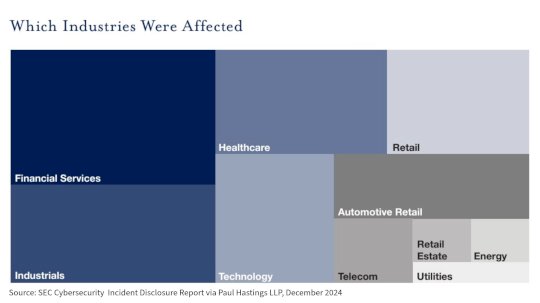
SEC Disclosures Up, But Not Enough Details Provided – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid Source: Paul Hastings, LLP The new cybersecurity disclosure rules introduced by the US Securities and Exchange Commission (SEC) last...
Emerging Threats & Vulnerabilities to Prepare for in 2025 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading In 2024, we at Dark Reading covered a variety of attacks, exploits, and, of course, vulnerabilities...
DDoS Attacks Surge as Africa Expands Its Digital Footprint – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Golden Dayz via Shutterstock Rising Internet adoption and digital transformation initiatives are exposing organizations in Africa to...
Scams Based on Fake Google Emails – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Menu Blog Newsletter Books Essays News Talks Academic About Me HomeBlog Scams Based on Fake Google Emails Scammers are hacking...
How are you securing your communications in the wake of the Volt Typhoon revelations? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 26 Dec 20246 mins Communications SecurityHacker GroupsTelecommunications Industry The alarming news that Chinese-affiliated threat groups have likely infiltrated US telecommunications is...
Adobe ColdFusion Any File Read Vulnerability (CVE-2024-53961) – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS Overview Recently, NSFOCUS CERT detected that Adobe issued a security announcement and fixed any file read vulnerability in Adobe ColdFusion (CVE-2024-53961)....
Feel Supported: Integrating IAM with Your Security Policies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Integrating IAM Crucial for Your Security Policies? As we move more and more of our activities online, the...
Stay Calm and Secure: Secrets Management for the Modern Age – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn How Effective is Your Modern Secrets Management Strategy? Have you ever wondered about the strength of your modern secrets management?...
Relax with Secure Cloud-Native Solutions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn What Does Securing Your Cloud-Native Solutions Mean? Cloud-native solutions are becoming more popular by the day. They are seen as...
Drive Innovation with Enhanced Secrets Scanning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Does the thought of data breaches keep you up at night? If so, you’re not alone. The modern, interconnected business...
A Merry Little Christmas And A Happy New Year – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2024/12/a-merry-little-christmas-and-a-happy-new-year-2/ Category & Tags: Security Bloggers Network,Happy New...
Spyware Maker NSO Group Found Liable for Hacking WhatsApp – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Spyware Maker NSO Group Found Liable for Hacking WhatsApp A judge has found that NSO Group, maker of the...
10 essenzielle Maßnahmen für physische Sicherheit – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die physische Sicherheit von Gebäudekomplexen und Geräten zu gewährleisten, kann ebenso herausfordernd sein wie Cyberbedrohungen abzuwehren. Wenn physische Security nur immer so...
The 2024 cyberwar playbook: Tricks used by nation-state actors – Source: www.csoonline.com
Source: www.csoonline.com – Author: Beyond the usual playbook, nation-state actors in 2024 relied on a mix of advanced tactics, including sophisticated backdoors and stealthy LOTL, to...
The AI Fix #30: ChatGPT reveals the devastating truth about Santa (Merry Christmas!) – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 30 of The AI Fix, AIs are caught lying to avoid being turned off, Apple’s...
FBI Blames North Korea for $308M Cryptocurrency Hack as Losses Surge in 2024 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The Federal Bureau of Investigation (FBI) is publicly blaming North Korean government hackers for a $308 million cryptocurrency heist from...
American Addiction Centers Data Breach Impacts 422,000 People – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire American Addiction Centers is notifying more than 422,000 people that their personal information was stolen in a recent data breach....
2025 NDAA Provides $3 Billion Funding for FCC’s Rip-and-Replace Program – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The 2025 National Defense Authorization Act (NDAA), signed into law by President Biden on Monday, authorizes several cyber-related initiatives, including...
Adobe Patches ColdFusion Flaw at High Risk of Exploitation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Adobe on Monday warned that proof-of-concept (PoC) code exists for a fresh ColdFusion vulnerability. Tracked as CVE-2024-53961 (CVSS score of...
Unmasking the Risks: Auditing Your Web Pixel Usage – Source: securityboulevard.com
Source: securityboulevard.com – Author: mykola myroniuk In our last post, we discussed the powerful, yet potentially risky nature of web pixels. Now, let’s dive into how...
Best of 2024: Gmail Error: Email Blocked Because Sender is Unauthenticated – Source: securityboulevard.com
Source: securityboulevard.com – Author: Yunes Tarada Reading Time: 7 min Attention users! Gmail has officially started rolling out Google email sender policies for 2024, and users...
DEF CON 32 – What To Expect When You’re Exploiting: 0Days, Baby Monitors & Wi-Fi Cams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – What To Expect When You’re Exploiting: 0Days, Baby Monitors &...
Randall Munroe’s XKCD ‘D Roll’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
DEF CON 32 – Your Smartcard Is Dumb: A Brief History Of Hacking Access Control Systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, December 24, 2024 Home » Security Bloggers Network » DEF CON 32 – Your Smartcard Is Dumb: A Brief...
Best of 2024: An Accidental Discovery of a Backdoor Likely Prevented Thousands of Infections – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Larkin Yesterday’s discovery of the xz backdoor was an accident. But what a fortunate accident it was. The actor (or actors,...
PowerDMARC in 2024: A Year in Review – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ahona Rudra As we close out 2024, PowerDMARC stands stronger than ever. This year marked a host of milestones that highlight our...
5 Common DNS Vulnerabilities and How to Protect Your Network – Source: securityboulevard.com
Source: securityboulevard.com – Author: Yunes Tarada DNS vulnerabilities are often overlooked in cybersecurity strategies, despite DNS being a “phonebook” of the internet. DNS enables seamless interaction...
How to Streamline Your Cybersecurity Risk Management Process – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Furneaux Many industry regulations require or promote cybersecurity risk assessments to bolster incident response, but what is a cybersecurity risk assessment?...