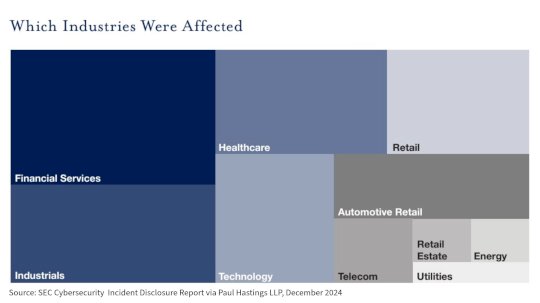
Source: www.darkreading.com – Author: Fahmida Y. Rashid Source: Paul Hastings, LLP The new cybersecurity disclosure rules introduced by the US Securities and Exchange Commission (SEC) last...
Day: December 26, 2024
Emerging Threats & Vulnerabilities to Prepare for in 2025 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading In 2024, we at Dark Reading covered a variety of attacks, exploits, and, of course, vulnerabilities...
DDoS Attacks Surge as Africa Expands Its Digital Footprint – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Golden Dayz via Shutterstock Rising Internet adoption and digital transformation initiatives are exposing organizations in Africa to...
Scams Based on Fake Google Emails – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Menu Blog Newsletter Books Essays News Talks Academic About Me HomeBlog Scams Based on Fake Google Emails Scammers are hacking...
How are you securing your communications in the wake of the Volt Typhoon revelations? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 26 Dec 20246 mins Communications SecurityHacker GroupsTelecommunications Industry The alarming news that Chinese-affiliated threat groups have likely infiltrated US telecommunications is...
Adobe ColdFusion Any File Read Vulnerability (CVE-2024-53961) – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS Overview Recently, NSFOCUS CERT detected that Adobe issued a security announcement and fixed any file read vulnerability in Adobe ColdFusion (CVE-2024-53961)....
Feel Supported: Integrating IAM with Your Security Policies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Integrating IAM Crucial for Your Security Policies? As we move more and more of our activities online, the...
Stay Calm and Secure: Secrets Management for the Modern Age – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn How Effective is Your Modern Secrets Management Strategy? Have you ever wondered about the strength of your modern secrets management?...
Relax with Secure Cloud-Native Solutions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn What Does Securing Your Cloud-Native Solutions Mean? Cloud-native solutions are becoming more popular by the day. They are seen as...
Drive Innovation with Enhanced Secrets Scanning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Does the thought of data breaches keep you up at night? If so, you’re not alone. The modern, interconnected business...
A Merry Little Christmas And A Happy New Year – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2024/12/a-merry-little-christmas-and-a-happy-new-year-2/ Category & Tags: Security Bloggers Network,Happy New...